View the manual for the TP-Link CPE220 here, for free. This user manual comes under the category access points and has been rated by 8 people with an average of a 8.6. This manual is available in the following languages: English. Do you have a question about the TP-Link CPE220?
Ask your question here
Frequently asked questions
Can’t find the answer to your question in the manual? You may find the answer to your question in the FAQs about the TP-Link CPE220 below.
What is the height of the TP-Link CPE220?
The TP-Link CPE220 has a height of 33.5 mm.
What is the width of the TP-Link CPE220?
The TP-Link CPE220 has a width of 110 mm.
What is the depth of the TP-Link CPE220?
The TP-Link CPE220 has a depth of 57 mm.
What certifications does the TP-Link CPE220 have?
The TP-Link CPE220 has the following certifications: — CE/FCC/UL/IC/GS/PSB/C-tick/SAA/S-Mark/KC-mark\n- RoHS, IPX5.
Is the manual of the TP-Link CPE220 available in English?
Yes, the manual of the TP-Link CPE220 is available in English .
Is your question not listed? Ask your question here

Installation Guide
Outdoor CPE
CPE210 / CPE220 / CPE510 / CPE520

CONTENTS
Overview
Hardware Connection
Site Consideration
Ethernet Cable Selection
Connection and Installation
Lightning & ESD Protection
Software Conguration
Login to Pharos
Antenna Alignment
Specications
Frequently Asked Questions (FAQ)
1
3
5
6
7
8
11
12
13
Overview
TP-LINK’s Pharos series outdoor CPEs are dedicated to remote pointto-point connection. This guide is applicable to products including
CPE210, CPE220, CPE510 and CPE520.
• Package Contents
Installation Guide
Power Cord
Outdoor CPE
CPE210 / CPE220 / CPE510 / CPE520
Pharos CPE Passive PoE
TERMS OF USE: TP-LINK’s Pharos series outdoor CPEs must be professionally
installed. Shielded Ethernet cable and earth grounding must be used as
conditions of product warranty. TOUGHCable is designed for outdoor
installations. It is the customer’s responsibility to follow local country
regulations, including operation within legal frequency channels, output
power, and Dynamic Frequency Selection (DFS) requirements.
Adapter
Pole Mounting
Straps
Installation Guide
1
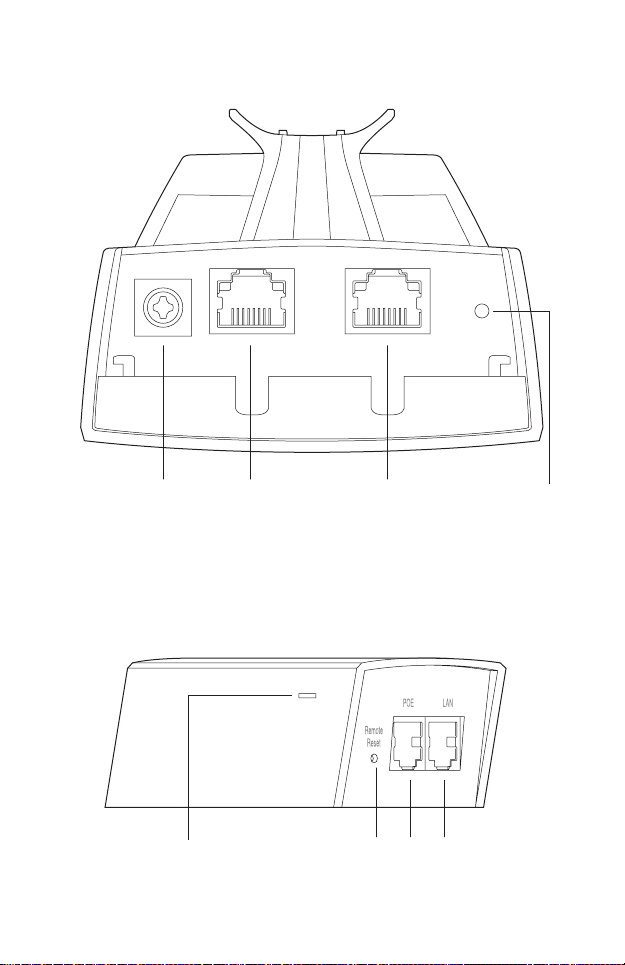
• Panel Layout
Pharos CPE:
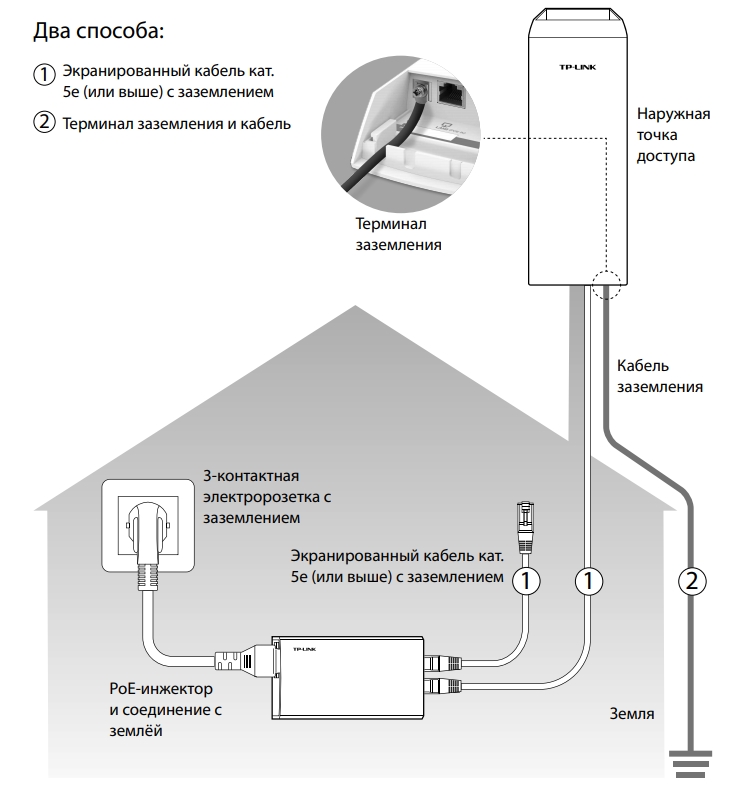
Grouding
Terminal
Passive PoE Adapter:
Power LED
The Power LED indicates the
electricity current situation:
green (0~0.8A), red (0.8A~1A).
2
Shielded Ethernet Port
LAN0 (Passive PoE in)
Shielded Ethernet Port
LAN1
Reset
RESET
LANPOERemote
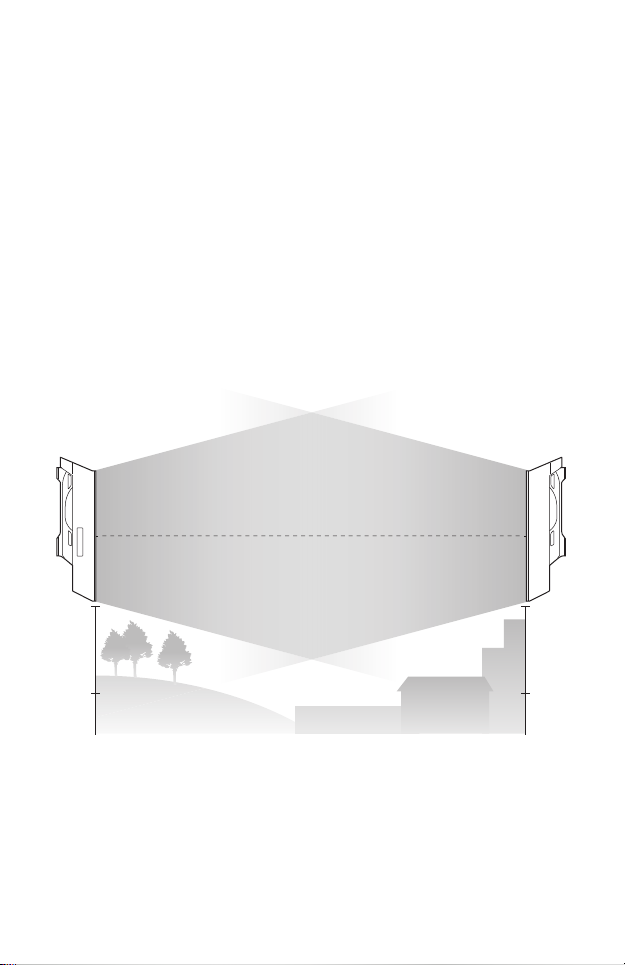
Hardware Connection
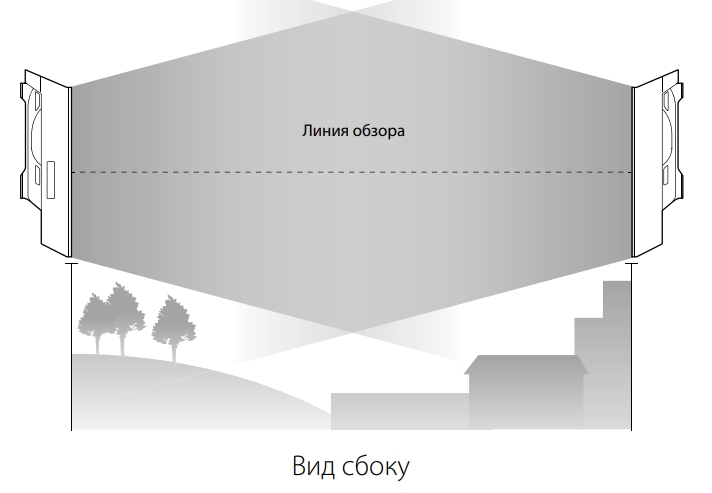
1. Site Consideration
• Mounting Height
Ensure a clear line of sight between the wireless devices for an
optimum performance. An elevated location is recommended as
obstacles like trees, buildings and large steel structures will weaken the
wireless signal.
See Q2 in FAQ for details about how to calculate the minimum
mounting height of the devices.
line of sight
Side View
3
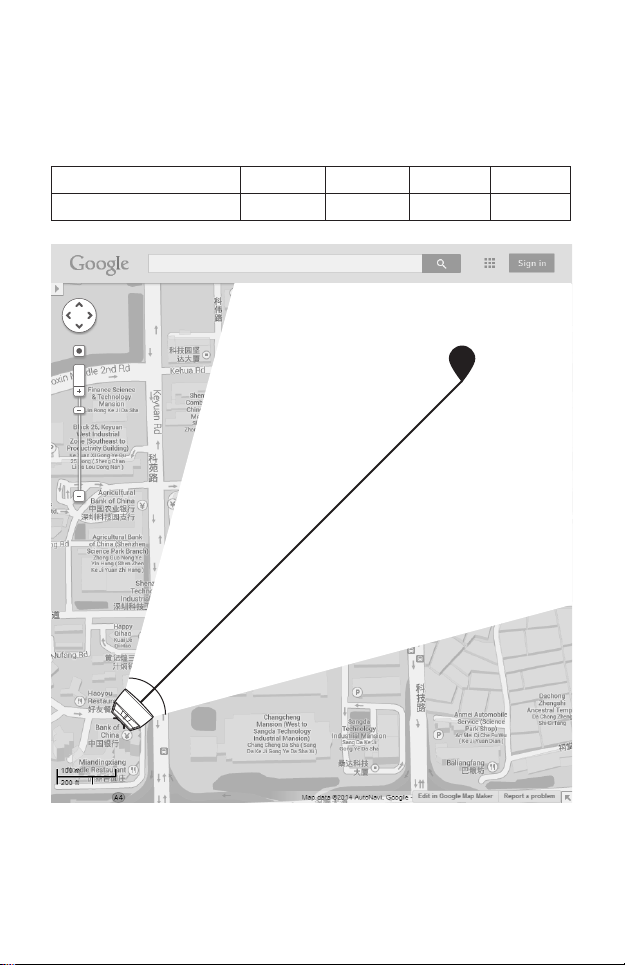
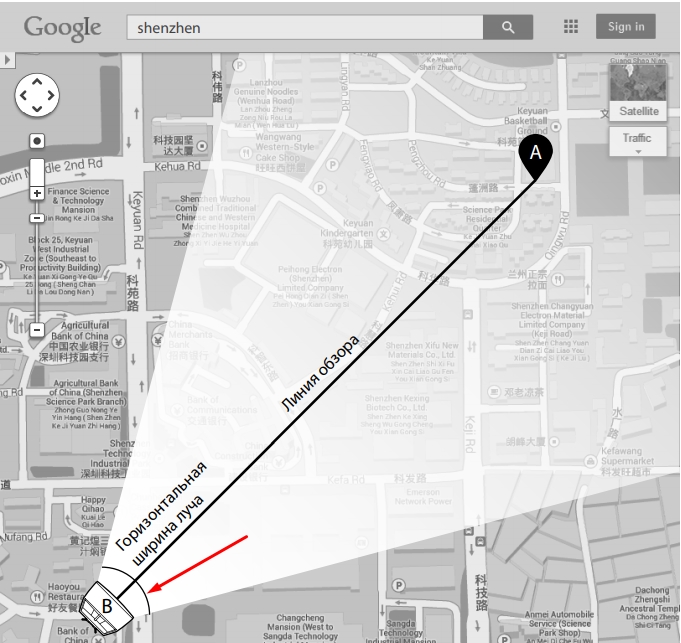
• Orientation
Install the CPE devices with their fronts facing the signal receivers. You
can orient the devices with the assistance of Google Map, GPS and
some landmarks according to the horizontal beamwidth listed below.
Models CPE210 CPE220 CPE510 CPE520
Horizontal Beamwidth 65° 45° 45° 50°
shenzhen
A
line of sight
Horizontal
Beamwidth
B
4
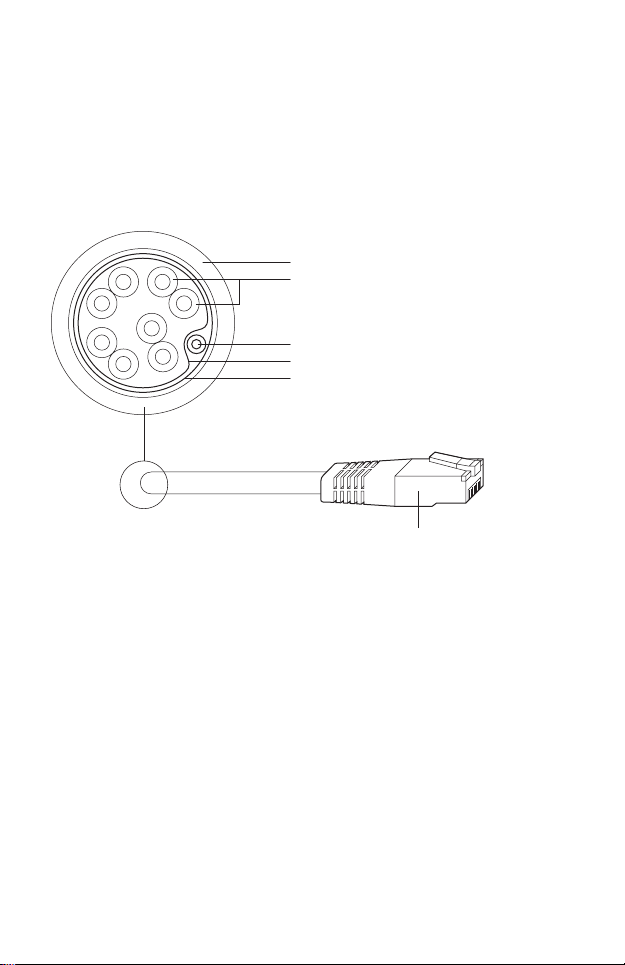
2. Ethernet Cable Preparation
1. Select the adequate type of Ethernet cable.
The shielded CAT5e cable with ground wire (refer to the figure below)
is prior to the general shielded CAT5e cable during the whole cabling.
The former can more effectively protect your devices against ESD
attacks under brutal outdoor environment.
Sheath
Twisted Pair
Ground Wire
Cable Shield
Secondary Cable Shield
Shielded RJ45 Connector
Shielded CAT5e Cable with Ground Wire
2. Review the routes of connecting the POE Adapter to the CPE and
evaluate the Ethernet cable length for all the connections, then
prepare adequate Ethernet cable.
5
Loading…
Всем привет на портале WiFiGid! Сегодня мы поговорим про одну из самых популярных точек доступа – модель TP-Link CPE510. В общем они все примерно одинаковые, поэтому данная статья подойдет и для пользователей других моделей: CPE520, CPE220 и CPE210. Они имеют одинаковую операционную систему PHAROS, подключаются и настраиваются одинаково. Есть пара отличий в характеристиках, но об этом чуть позже.
Брал я ее для раздачи интерната на большую территорию, но данные модели подойдут и для других вариантов использования. Я все описал максимально подробно. Так как данное устройство будет работать на улице, и есть вероятность удара молнии или короткого замыкания, то советую читать все очень внимательно от самого начала и до конца. Поехали!
Содержание
- Плюсы, минусы и мое мнение
- ШАГ 1: Распаковка и комплектация
- ШАГ 2: Порты и подключение
- ШАГ 4: Настройка
- Точка доступа
- Клиент/Ретранслятор (Усилитель)/ Мост
- Точка доступа с маршрутизатором
- Беспроводной клиент (WISP)
- ШАГ 5: Боевая установка
- Настройка DHCP
- Мульти SSID (Несколько Wi-Fi сетей)
- Фильтрация MAC-адресов
- Обновление прошивки
- Характеристики и сравнение с CPE220 и CPE210
- Эмулятор
- Руководство пользователя
- Видео
- Задать вопрос автору статьи
Плюсы, минусы и мое мнение
- Работает в разных режимах: точка доступа, клиент, повторитель, мост, обычный роутер, подключение к WISP. Про эти режимы я подробно расскажу ниже.
- Очень удобная и понятная прошивка. Если честно она мне понравилась даже больше, чем на обычных домашних роутерах.
- Прочный корпус из PBT пластика, а не из ABS.
- Режим защиты от влаги и пыли по стандарту IPX
- Есть регулировка мощности сигнала от 0 до 20 дБм (или 100 мВт).
- Поддержка MIMO 2х2.
- Две встроенные двухполяризационные антенны по 13 дБи.
- TP-LINK Pharos MAXtream TDMA – данный режим позволяет работать сразу с несколькими точками доступа.
- PoE питание и дополнительный обычный LAN порт.
- Поддержка 5 ГГц. Младшие модели CPE220 и CPE210 работают с 2,4 ГГц.
- Процессор Qualcomm Atheros с тактовой частотой 560 МГц позволяет отлично переваривать большое количество устройств.
- MAXtream TDMA – данный режим позволяет уменьшить конфликты большого количества точек доступа. Также это позволяет улучшить связь и пропускную способность сети. Запатентованная технология, которая работает только с TP-Link точками доступа. Но её можно отключить.
- Защита от ударов молний.
- Защита от электростатического разряда.
- Поддержки ширины канала в 5, 10, 20 и 40 МГц.
- Работает на расстоянии до 15 километров.
- Функция автоматической отправки журнала событий на почту.
- Есть возможность настроить мульти-SSID – несколько разделенных по VLAN вай-фай сетей.
- Дополнительные функции: Ping Watch Dog, DDNS, агент SNMP, подключение WEB-сервера, SSH-сервер, фильтрация MAC-адресов.
- Очень смешная цена у CPE
- Pharos Control – программа для управления несколькими точками.
- В режиме роутера не поддерживает L2TP и PPTP типы подключения.
- Нет фильтрации по URL.
Сразу скажу, что я точкой доступа очень доволен. Во-первых, она очень просто и легко подключается. Даже простой пользователь с легкостью её настроит. Во-вторых, внутри стоит очень удобный интерфейс. В-третьих, антенна действительно может покрыть достаточно большую территорию. Я её установил на кронштейн на базе, и она покрывает всю территорию. В-четвертых, брал её за 4200 рублей – согласитесь, даже роутеры стоят дороже. При подключении до 20 устройств, работает стабильно, не греется и не отваливается. Система позволяет мониторить большое количество данных и отправлять их на почту.
Если вы используете несколько точек доступа от TP-Link, то для удобства управления есть специальное приложение Pharos Control.
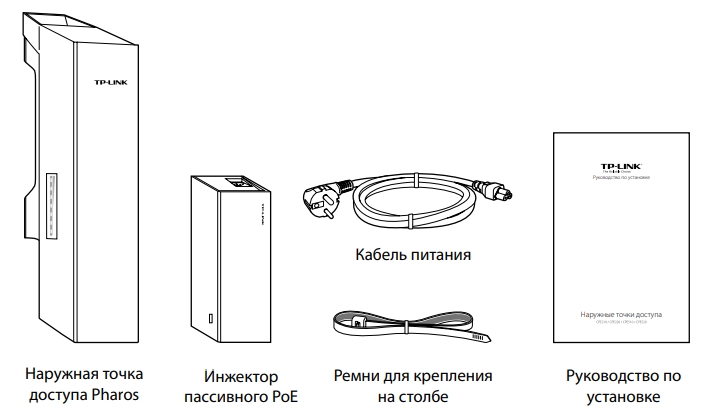
ШАГ 1: Распаковка и комплектация

Итак, у в комплекте идет достаточно небольшая коробка. Давайте её распакуем и посмотрим, что же внутри:
- Само устройство.
- Блок питания
- Кабель питания.
- Стяжки.
- Гарантийный талон.
- Руководство пользователя.
И другие не очень важные бумажки. Корпус белый, сделанный из качественного пластика. Точка доступа может спокойно работать в уличных условиях. Корпус выполнен с защитой IPX5.
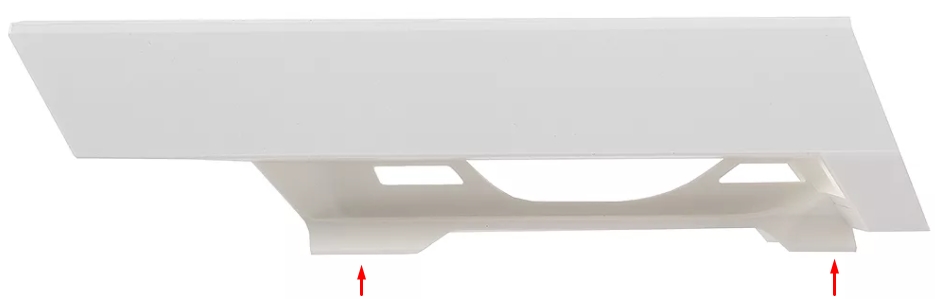
Снизу можно заметить специальные держатели, с помощью которых можно повесить устройство на кронштейн. Именно для этого в коробке есть стяжки. Устройство способно работать в самых экстремальных условиях от -40 до +70 градусов по Цельсию.
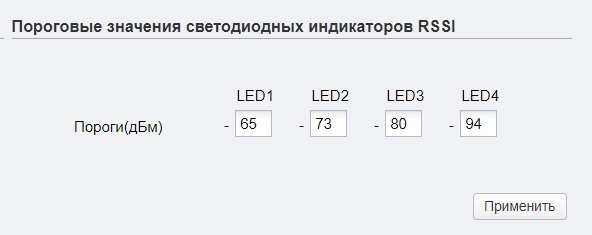
Как я понял, корпус сделан не из дешевого ABS пластика, который используется везде. А из прочного и стойкого PBT. Сбоку есть индикация:

- Первые четыре лампочки – это индикация порога в дБм:
- 65 дБм.
- 73 дБм.
- 80 дБм
- 94 дБм
- LAN 0-1 – подключение к локальным портам.
- POWER – питания.
Порог индикации можно будет изменить в настройках, в разделе «Система», подраздел «Пороговые значения светодиодных индикаторов RSSI».
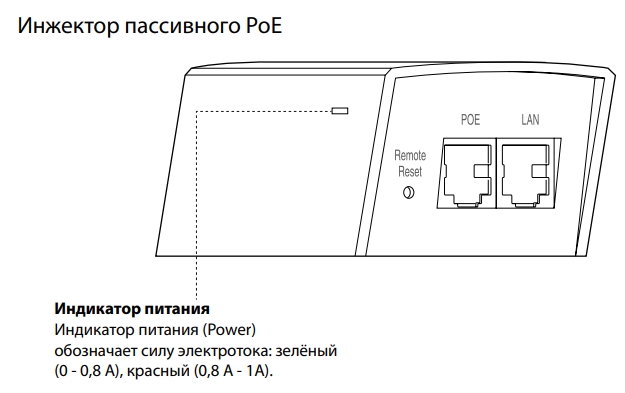
Если посмотреть на инжектор, то можно также увидеть индикатор питания, который может гореть и обозначать силу электротока:
- Зеленый (0-0,8А).
- Красный (0,8-1А).
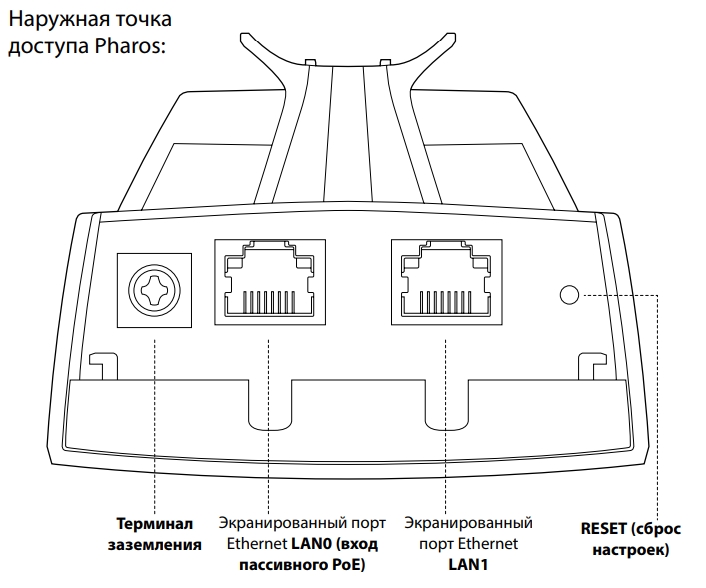
ШАГ 2: Порты и подключение
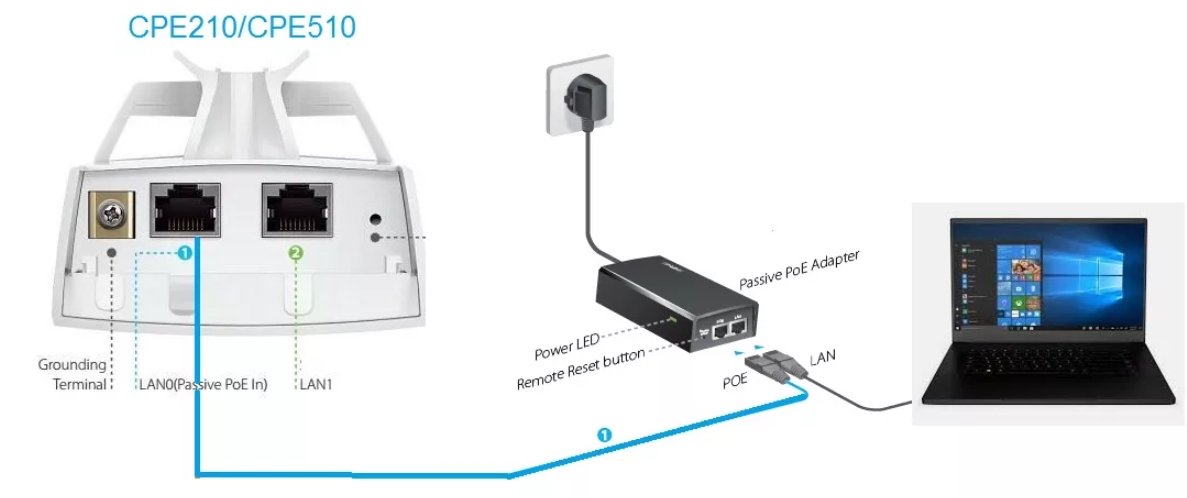
Давайте рассмотрим все порты на точке доступа и сразу её подключим. Снизу мы можем увидеть:
- Терминал заземления
- LAN порт с пассивным питанием PoE.
- Обычные LAN порт.
- Reset – кнопка для сброса точки доступа до заводской конфигурации. Для этого её нужно зажать на 10 секунд при включенном устройстве.
Для настройки вам нужно будет подключить ноутбук или компьютер к точке доступа по схеме выше. Для этого вам понадобятся два сетевых Ethernet кабеля. Один подключаем от «PoE In» точки доступа к аналогичному PoE блока питания. Второй кабель просто подключаем к ноутбуку.
Обычно данное устройство настраивают в двух режимах: точка доступа и клиент. То есть одно раздает Wi-Fi, а второе к нему подключается. Можно использовать вообще один аппарат, а подключаться к вай-фай с роутеров, телефонов, ноутбуков или других устройств. Отлично подойдет для раздачи интернета в промышленных зонах, на складах и в крупных предприятиях.
По умолчанию в прошивке не включен DHCP, поэтому для входа в настройки устройства нужно будет прописать статический IP в сетевой конфигурации ноутбука или компьютера.
- Нажмите одновременно на клавиши «Win» и «R» и введите команду:
ncpa.cpl
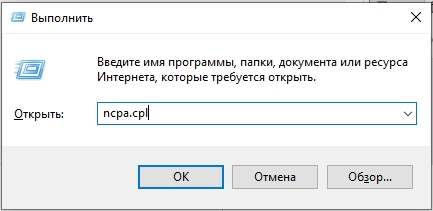
- Откройте свойства Ethernet подключения.
- Нажмите один раз по IPv4 и зайдите в «Свойства». Далее установите галочку для ручной конфигурации. Вводим значения:
- IP-адрес – 192.168.0.2
- Маска подсети – 255.255.255.0 (Установится автоматический)
- Основной шлюз – 192.168.0.254
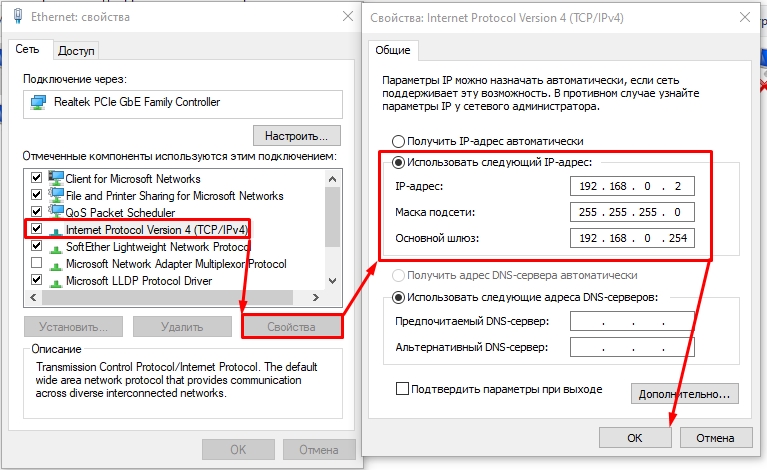
ШАГ 4: Настройка
- Теперь открываем браузер и в адресную строку вводим адрес точки доступа:
192.168.0.254
ПРИМЕЧАНИЕ! Если будут проблемы с входом, то добавьте в начало строки «http://», чтобы получилось так – http://192.168.0.254
- Вас также попросят ввести:
- Логин – admin
- Пароль – admin
- Выберите регион, а также язык. Обязательно выделите галочку ниже и нажмите по кнопке «Login».
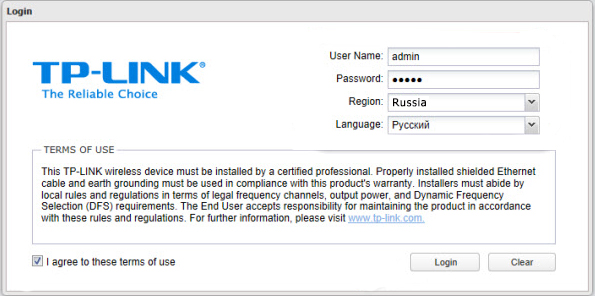
- После этого язык панели изменится на русский, и вам будет предложено изменить пароль от админки.
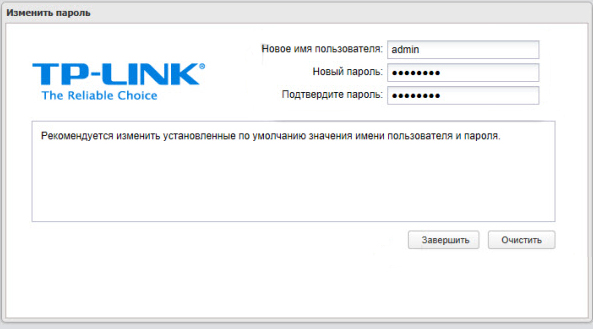
- Мы попадем на вкладку «Состояния», чтобы приступить к настройке нажмите по первому разделу «МАСТЕР».
Далее вы увидите несколько режимов, в которых может работать наше устройство. Давайте поподробнее разберем каждый, а вы уже на примере сможете выбрать тот, который нужен именно вам.
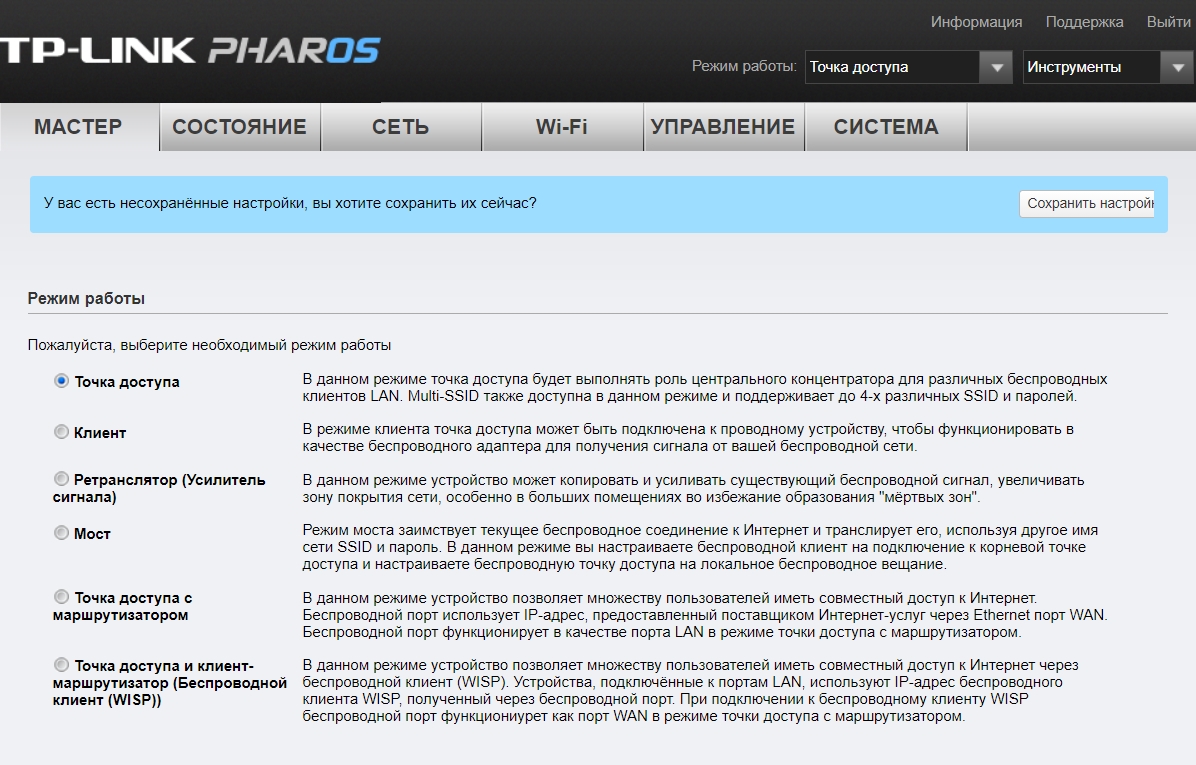
Точка доступа
Для подключения к интернету мы будем использовать основной маршрутизатор, к которому и будет подключен интернет. Далее от LAN порт роутера идет подключение к тому же порту на TP-Link CPE510. И уже точка доступа будет раздавать Wi-Fi на другие устройства. Все настройки DHCP будет раздавать роутер, а не точка доступа.
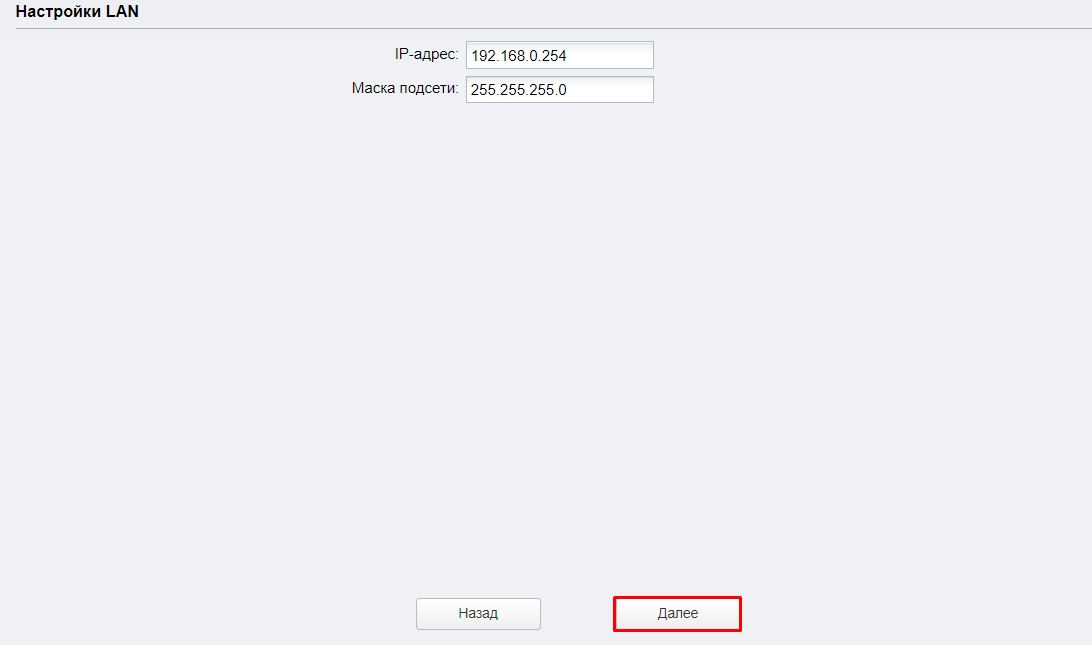
Когда вы выберите этот пункт, вам предложат изменить IP адрес устройства – оставляем значение как есть и переходим к следующему шагу.
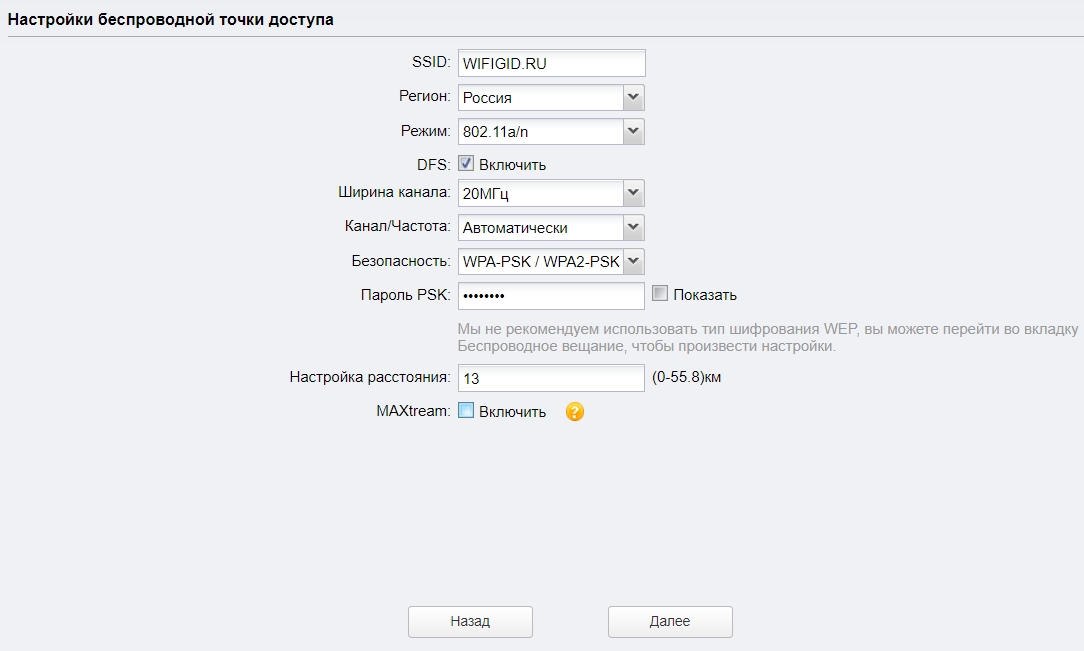
Теперь давайте пройдемся по настройкам:
- SSID – имя вай-фай сети.
- Регион – установите ваш регион.
- Режим – оставляем значение по умолчанию.
- DFS – включаем.
- Ширину канала – ставим 20/40 или 20 МГц.
- Канал/Частота – Автоматически.
- Безопасность – WPA-PSK / WPA2-PSK.
- Пароль PSK – вводим ключ от вайфай.
- Настройка расстояния – если вы не знаете точное расстояние, то установите значение 0.
- MAXtream – как я понял, это собственная разработка от TP-Link, которая увеличивает расстояние работы беспроводной сети. Проблема всех этих разработок, что они могут криво работать со сторонними устройствами, так что я бы её выключил. Но ради теста, можете попробовать – если будут проблемы с подключением, то выключите.
Клиент/Ретранслятор (Усилитель)/ Мост
В режиме «Клиента» точка доступа подключается к сторонней Wi-Fi сети роутера, а раздает его по проводу. К проводу можно подключить не только одно устройство (компьютер или ноутбук), но и другой роутер. Роутер должен быть подключен к WAN порту, а в настройках интернет подключения (WAN) выбрать DHCP (Динамический IP).

В режиме «Ретранслятор (Усилитель сигнала)» точка доступа подключается к роутеру или другой точке доступа и усиливает сигнал в данной области, полностью копируя данную Wi-Fi сеть. Режим «Моста» повторяет то же самое подключение, но есть одно отличие – в таком режиме точка доступа будет раздавать самостоятельную Wi-Fi сеть.

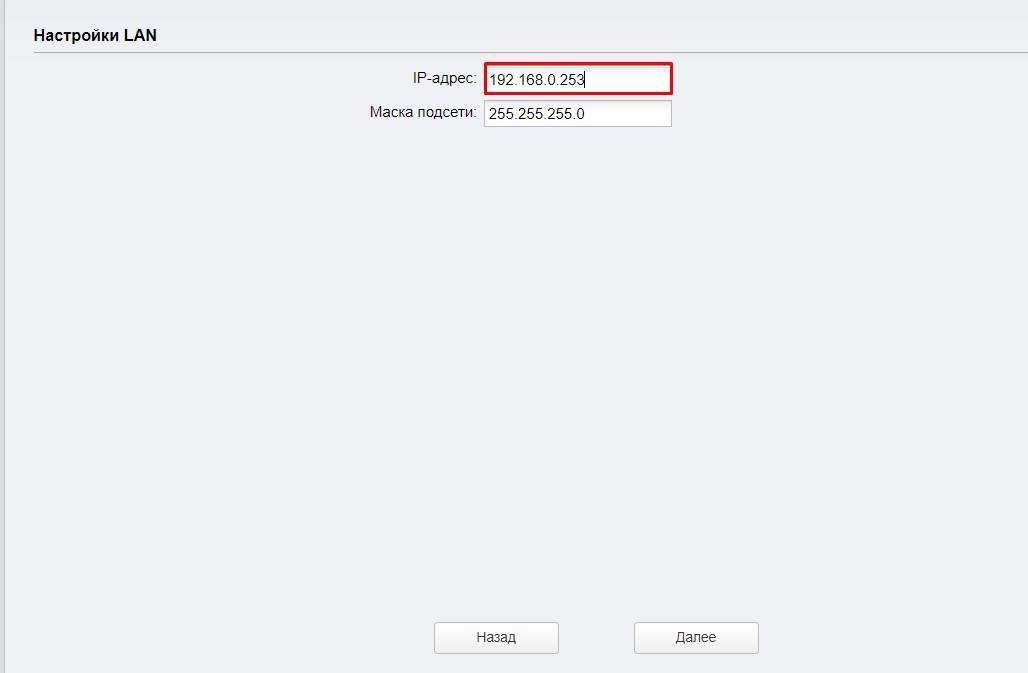
Если вы используете в качестве основной точки доступа такую же модель (TP-Link CPE510/CPE220/CPE210/CPE520), то вам нужно изменить IP-адрес и поменять одну цифру. То есть будет так:
- Точка доступа – 192.168.0.254
- Клиент – 192.168.0.253
Если вы будете подключаться к Wi-Fi роутера или другого подобного устройства, то вам нужно узнать IP-адрес этого аппарата и сделать аналогичные действия – установить такой же IP, но изменить последнюю цифру. Также в роутере зайдите в раздел LAN-клиентов и установите статический, зарезервированный адрес для этой точки доступа в режиме клиента.
СОВЕТ! Если будут проблемы с коннектом, то после настройки перейдите в раздел «Сеть» и установите «Тип подключения» в «Динамический» режим. То есть данная точка доступа будет получать IP от другого устройства. На нем должен быть включен DHCP-сервер.
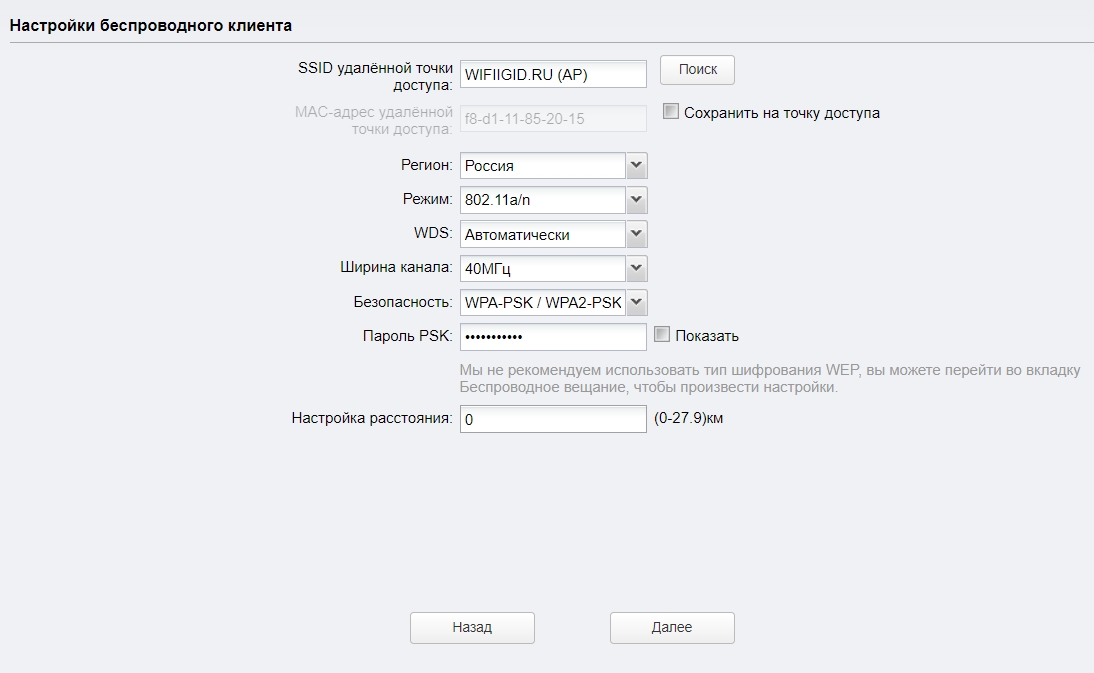
На следующем этапе нам нужно подключиться к вай-фай – для этого жмем по кнопке «Поиск». Находим нашу сеть, и вводим «Пароль PSK». Для первичной настройки держите оба устройства на расстоянии не более 5 метров.
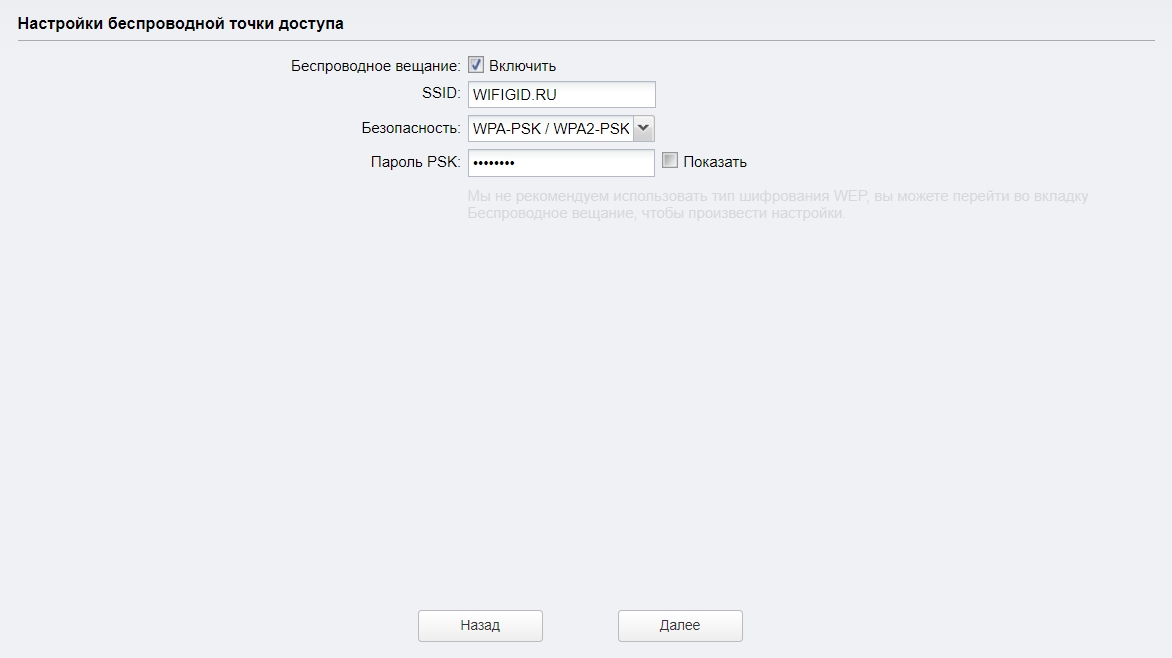
Если вы используете режим моста, то нам нужно ввести самостоятельные настройки Wi-Fi сети с именем и паролем. Можно также вообще выключить вещание, тогда интернет будет раздаваться только по проводу.
Точка доступа с маршрутизатором
В данном режиме TP-Link CPE510 работает как обычный роутер – подключается к кабелю провайдера и раздает интернет по вай-фай.

Как видите, аппарат поддерживает только три типа подключения: динамический, статический IP и PPPoE. Берем договор от провайдера, где указаны определённые данные, которые нужны для коннекта к интернету.
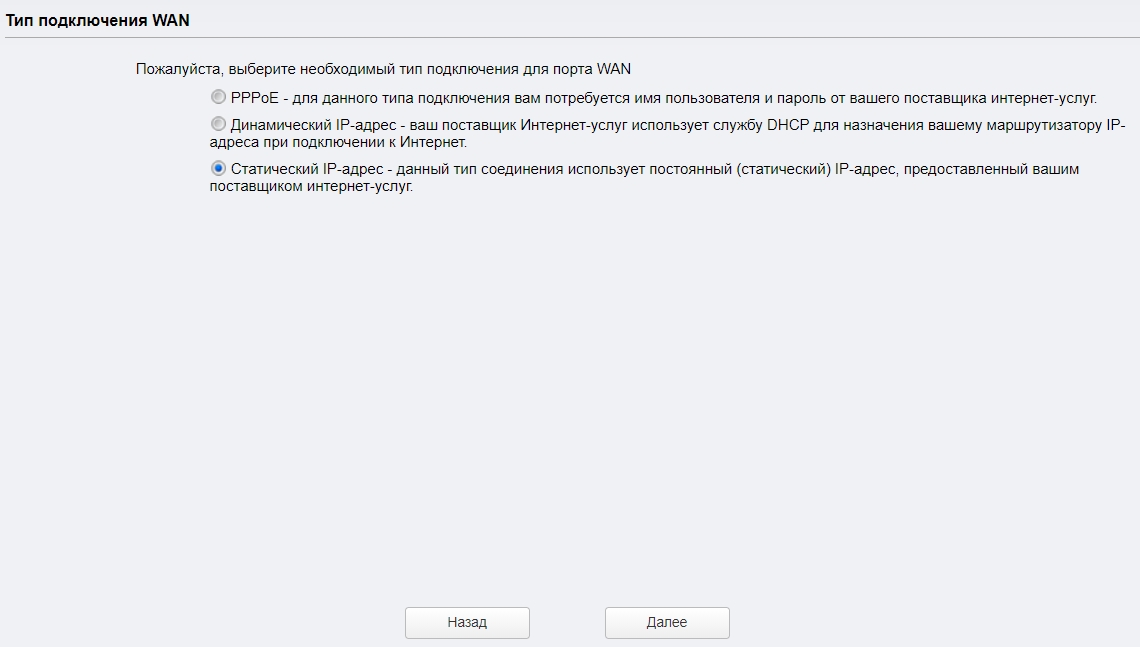
Вводим эти данные.
В конце останется настроить вай-фай. Ставим настройки как на картинке ниже.

Беспроводной клиент (WISP)
В данном подключении точка доступа подключается к WISP-антенне провайдера и уже потом раздает вай-фай на свои устройства.

Для подключения к интернету нужно будет указать тип подключения и ввести данные. Если в договоре по этому поводу ничего нет, то указываем «Динамический IP-адрес».

С помощью «Поиска» подключаемся к сети провайдера, введя пароль.

И в самом конце вводим настройки своей локальной Wi-Fi сети, которую вы будете использовать. Интернет также будет раздаваться по LAN портам.

ШАГ 5: Боевая установка
Все прошлые манипуляции мы выполняли в домашних условиях. Теперь я расскажу про подключение точки доступа в боевых. Смотрите, оба порта на устройстве экранированы, и не просто так.
Для установки нам понадобится кронштейн. Если вы используете две точки доступа, то вам нужно установить их так, чтобы они были четко направлены друг на друга. Особенно это касается режима моста, повторителя, клиента. Лучше устанавливать максимально высоко таким образом, чтобы на пути радиоволны было как можно меньше препятствий. Напоминаю, что любые препятствия глушат сигнал. Особенно это касается толстых стен и металлических преград.
Так как у разных моделей CPE разный показатель коэффициента усиления, то и размер луча разный.
| CPE210 | CPE220 | CPE510 | CPE520 | |
| Горизонтальная ширина (в градусах) | 70 | 45 | 45 | 50 |
Подключение аналогичное, как мы и делали все в самом начале, но будут пару отступлений.
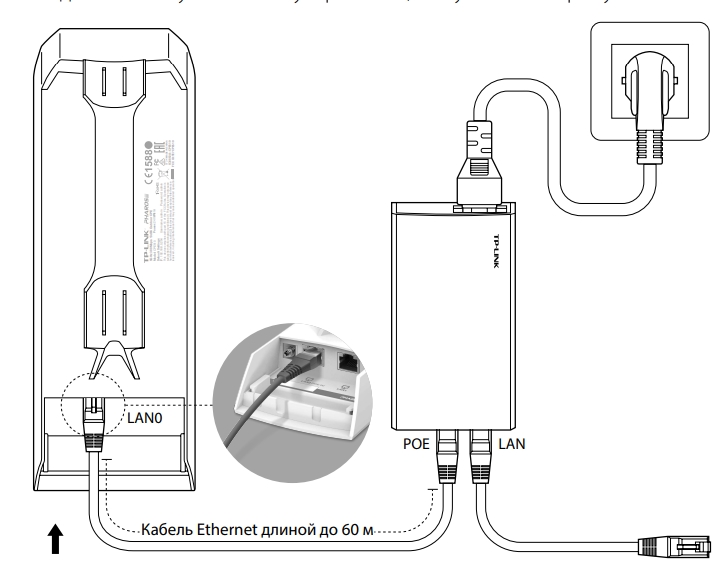
Для подключения к LAN0 от POE In нужно использовать кабель с заземлением категории 5E или выше. Также желательно, чтобы он был экранированным. Но земля будет работать только в том случае, если инжектор подключен к розетке с землей.
На кронштейн антенну можно прикрутить стяжками. После подключения к антенне обязательно закройте нижнюю часть с портами специальной крышкой. Кабель питания должен быть не больше 60 метров.
Но есть и второй способ – подключить обычный кабель и использовать провод заземления, подключив его от терминала заземления к основной земле.
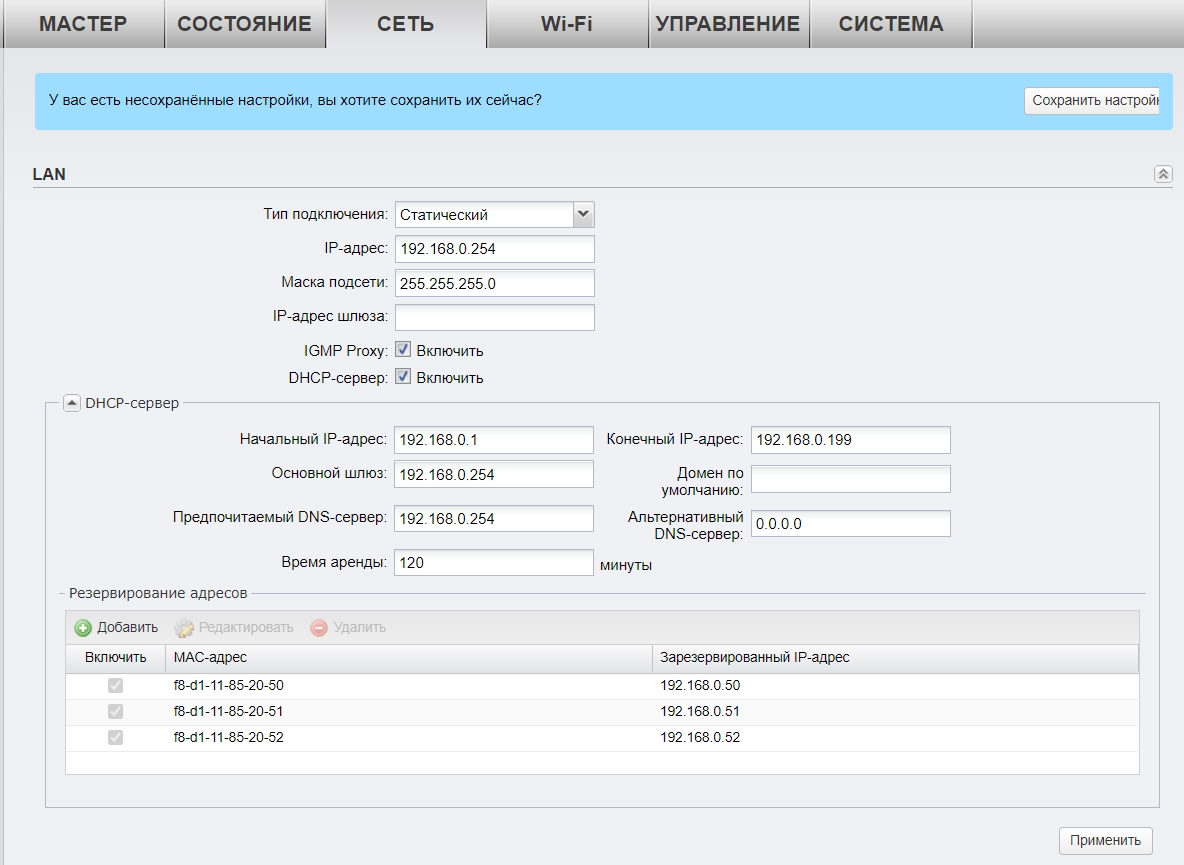
Настройка DHCP
В разделе «Сеть» можно более детально установить IP-адрес устройства. Если вы подключаетесь к основному роутеру, или другой точке доступа с включенным DHCP-сервером, то можно в типе подключения установить «Динамическое» получение IP.
В режиме клиента, ретранслятора (усилителя) или Моста можно будет вручную ввести IP, маску и шлюз. Тут также можно включить DHCP-сервер для своих устройств. В режиме усилителя его включать не стоит. Ниже можно зарезервировать IP-адреса для локальных устройств.
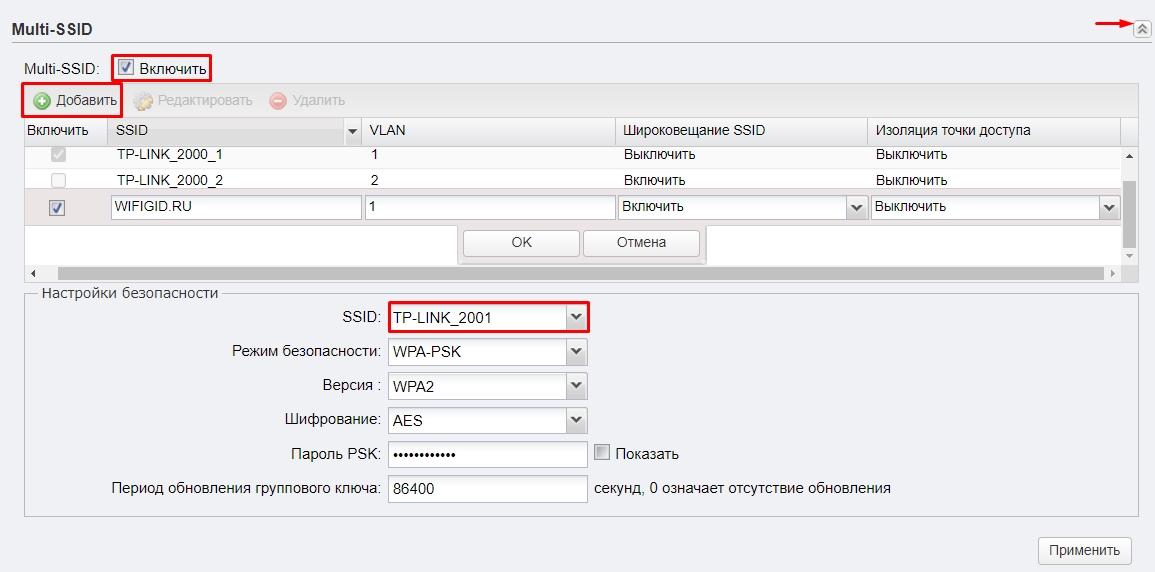
Мульти SSID (Несколько Wi-Fi сетей)
Если у вас большое предприятие, то вы в теории можете разделить несколько отделов, подключив их к разным Wi-Fi сетям.
- Для этого переходим в «Wi-Fi».
- Включаем «Multi-SSID».
- Нажимаем по кнопке «Добавить».
- Вводим название в поле «SSID». Указываем номер VLAN – разные VLAN это как бы разные сети, которые не могут контактировать друг с другом. Широковещание «SSID» – это видимость сети в эфире. Если выключить эту функцию, то сеть станет невидимой, а подключаться к ней нужно будет вручную, вводя имя и пароль. Изоляция точки доступа – это функция, которая изолирует клиентов друг от друга, то есть они не видят друг друга в сети. Эта функция нужна для открытых точек доступа, чтобы избежать взлома одного клиента другим.
- Нажимаем «ОК».
- Ниже выбираем «SSID». Указываем режим безопасности, версию, тип шифрования и вводим пароль.
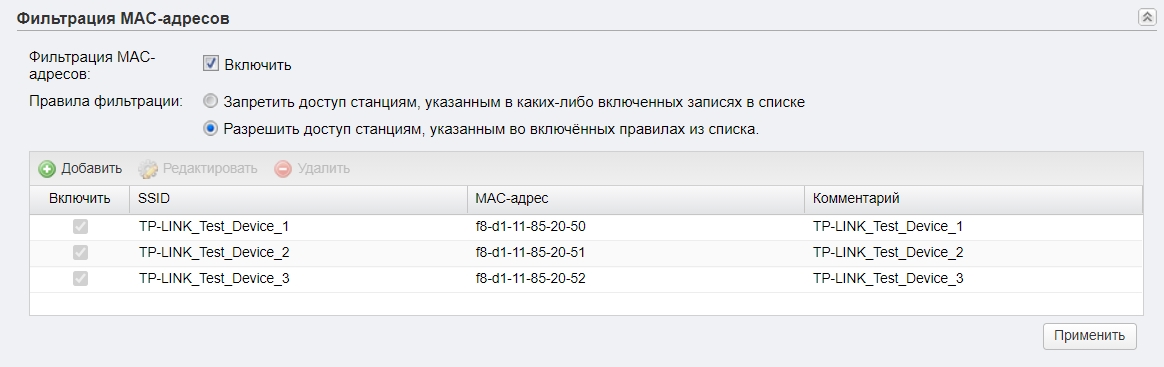
Фильтрация MAC-адресов
Также находится в разделе «Wi-Fi». Позволяет создать белый или черный список устройств, которым можно или запрещено подключаться к беспроводной сети. Максимально увеличивает безопасность, так как по определенным правилам сторонние устройства, даже зная пароль, не смогут подключиться к сети.
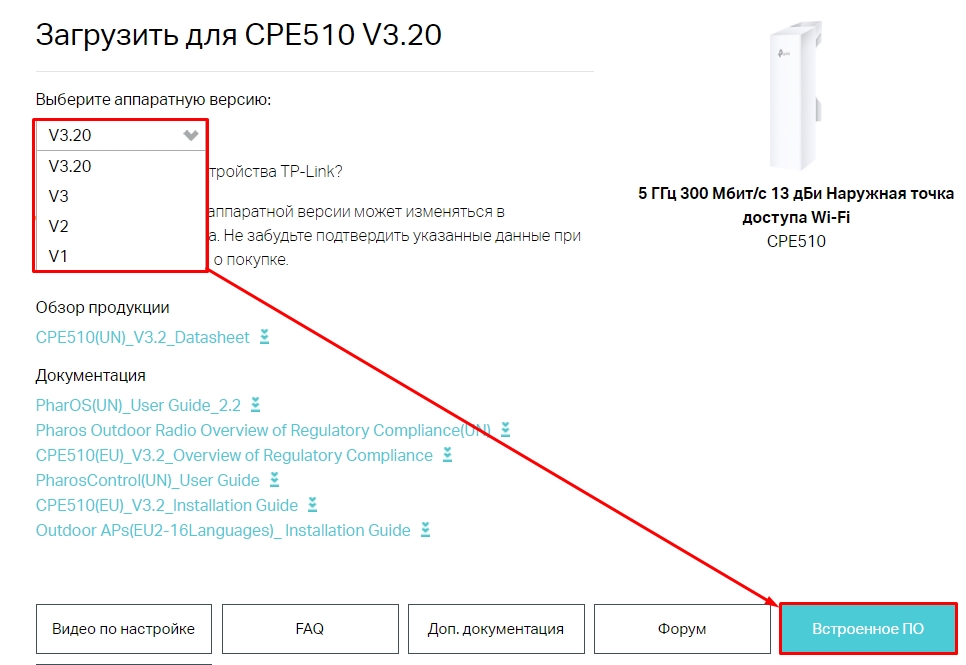
Обновление прошивки
ВНИМАНИЕ! Обновлять прошивку можно только при подключении по проводу.
- Заходим на официальную страницу аппарат.
- Выбираем свою аппаратную версию – её можно подсмотреть на этикетке на корпусе.
- Нажимаем по разделу «Встроенное ПО».
- Пролистываем ниже и скачиваем самую свежую прошивку.
- Переходим в «Систему», листаем до подраздела «Обновление встроенного ПО», нажимаем «Обзор», выбираем файл с прошивкой. Если вы до этого скачали архив, то обязательно его разархивируйте.
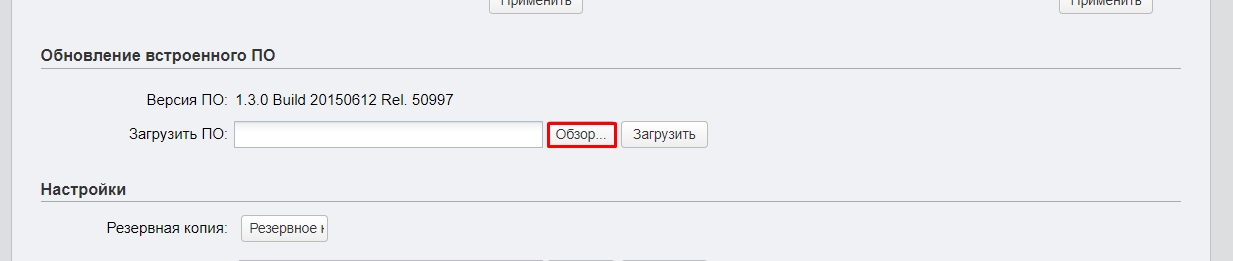
- Кликаем по кнопке «Загрузить» и ждем.
Характеристики и сравнение с CPE220 и CPE210
| CPE510 | CPE220 | CPE210 | |
| MIMO | 2х2 | ||
| Мощность (дБи) | 13 | 12 | 9 |
| Антенна (дБи) | 13 | 12 | 9 |
| Dual Ethernet | нет | есть | нет |
| Частота | 5 ГГц | 2,4 ГГц | |
| Максимальная скорость | До 300 Мбит в секунду | ||
| Ширина канала | 5/10/20/40 МГц | ||
| Питание | Passive PoE 24 В | ||
| Защита от статического удара | 15 кВ | ||
| Защита от ударов молнии | 6 кВ | ||
| Заземление | есть |
Эмулятор
Ссылка на эмуляторы
Руководство пользователя
Видео

For TP—LINK Pharos Series Products
REV1.0.0
1910011048
User Guide

CONTENTS
Chapter 1 Overview ………………………………………………………………………………………………………… 1
Introduction ……………………………………………………….…………………………………………………………………………………………………. 1
System Requirements …………………………..……………………………………………………….……………………………………………………. 1
Getting Started ………………………………………………………………………….…………………………………………………………………………. 1
Navigation ……………………………………………………….……………………………………………………….…………………………………………… 3
Chapter 2 Operation Modes …………………………………………………………………………………………….. 4
Access Point …………………………………………………………………………………………………………………………………………….……………. 4
Client……………………………………………….………………………………………………………………………………………………………….………….. 6
Repeater (Range Extender) ……………………………………………………………..…………………………………………………………………. 7
Bridge ……………………………………………..…………………………………………………….……………………………………………………………….. 8
AP Router …………………………………………..………………………………………………………………………………………………………………….. 8
AP Client Router (WISP Client) ……………………………..…………………………………………………….……………………………………… 9
Chapter 3 Quick Setup Guide ………………………………………………………………………………………….10
Access Point …………………………………………………………………………………………………………………………………………….………….. 10
Client……………………………………………….………………………………………………………………………………………………………….………… 12
Repeater (Range Extender) ……………………………………………………………..……………………………………………………………….. 14
Bridge ……………………………………………..…………………………………………………….……………………………………………………………… 17
AP Router …………………………………………..………………………………………………………………………………………………………………… 20
AP Client Router (WISP Client) …………………………….……………………………………………………..……………………………………. 22
Chapter 4 Status Tab ………………………………………………………………………………………………………27
Status Information ……………………………………………………………………………………………………………………………………………... 28
Monitor ……………………………………………………….……………………………………………………….………………………………………………. 32
Chapter 5 Network Tab …………………………………………………………………………………………………..37
WAN ………………………………….…………………………………………………….……………………………………………………………………………. 38
LAN ………………………..……………………………………………………………………………………………………………………………………………… 44
Forwarding …………………………..……………………………………………………….……………………………………………………….……………. 46
Security …………………………..……………………………………………………….……………………………………………………….………………….. 50
Access Control …………………………………………………………………………………………………………………………………………….………. 52
Static Routing …………………………………………………………………………………………………………………………………………….……….. 53
Bandwidth Control ……………………………………………………………………….……………………………………………………………………. 54
I

IP&MAC Binding ………………………………………………………………..…………………………………………………….…………………………. 55
Chapter 6 Wireless Tab ……………………………………………………………………………………………………57
Wireless Basic Settings ……………………………………………………………………………..……………………………………………………….. 58
Wireless Client Settings …………………………..……………………………………………………….……………………………………………….. 60
Wireless AP Settings ……………………………………………………………………..……………………………………………………………………. 61
Multi—SSID ……………………………………………………….…………………………………………………………………………………………………… 64
Wireless MAC Filtering …………………………..……………………………………………………….…………………………………………………. 65
Wireless Advanced Settings ……………………………………………………….……………………………………………………….……………. 66
Chapter 7 Management Tab ……………………………………………………………………………………………68
System Log ……………………………………………………..…………………………………………………….…………………………………………….. 69
Miscellaneous …………………………………………………………………………………………………………………………………………….……….. 70
Ping Watch Dog …………………………..…………………………………………………….……………………………………………………………….. 71
Dynamic DNS ……………………………………………………………………………………………………………………………………………………… 72
Web Server ………………………………………………………………………………………………………………………………………………………….. 73
SNMP Agent …………………………………………………………………………………………………………………………….………………………….. 74
SSH Server ……………..…………………………………………………….……………………………………………………………………………………… 75
RSSI LED Thresholds …………………………..……………………………………………………….……………………………………………………… 76
Chapter 8 System Tab ……………………………………………………………………………………………………..77
Device ……………………………………..…………………………………………………….……………………………………………………………………… 78
Location ……………………………………………………….……………………………………………………….……………………………………………… 78
User Account ……………………………………………………………………………………………………………………………………………………….. 78
Time Setting …………………………………………………………………………………………………………………………….………………………….. 79
Firmware Update …….………………………………………………………………………………………………………….……………………………… 81
Configuration …………………………………………………………………………………………………………………………….……………………….. 82
Chapter 9 Tools List ………………………………………………………………………………………………………..83
Ping ……………………….…………………………………………………….……………………………………………………………………………………….. 83
Traceroute ……………………………………………………….……………………………………………………….………………………………………….. 84
Speed Test ………………………………………………………….…………………………………………………….………………………………………….. 84
Survey ……………………………………………………………….………………………………………………………………………………………………….. 86
Spectrum Analysis ……………………………………………………………………………………………………………………………………………... 87
Appendix A: Pharos MAXtream TDMA …………………………………………………………………………………88
Appendix B: Glossary …………………………………………………………………………………………………………89
II

Chapter 1 Overview
Chapter 1 Overview
Introduction
is TP—LINK’s next generation outdoor product series dedicated to long—distance outdoor
wireless networking solutions.
is a powerful Web—based operating system, which is integrated into all Pharos series
products.
New features of Pharos series products are listed as follows:
Provides User—friendly UI design.
TP—LINK Pharos MAXtream (Time—Division—Multiple—Access) technology improves product
performance in throughput, capacity and latency, which are ideal for Point—to—multipoint applications.
Supports multiple operation modes: Access Point, Client, Repeater (Range Extender), Bridge, AP
Router and AP Client Router (WISP Client).
Provides system—level optimization for long—distance wireless transmission.
Supports adjustable transmit power by 1dBm from 0 to 27dBm/500mW.
Supports selectable bandwidth of 5/10/20/40MHz.
Supports easy antenna alignment with Wireless Signal Indicators on Web interface.
Provides Throughput Monitor, Spectrum Analyzer, Speed Test and Ping tools.
Supports discovery and management via Pharos Control application.
System Requirements
Operating system:
Microsoft Windows XP, Windows Vista, Windows 7, Windows 8, Linux, or Mac OS X
Web Browser:
Google Chrome, Safari, Firefox, and Apple Safari. IE browsers are not recommended.
Getting Started
To access the PharOS Configuration Interface, perform the following steps:
1. Configure the Ethernet adapter on your computer with a static IP address on the 192.168.0.x subnet
(for example, IP address: 192.168.0.100 and subnet mask: 255.255.255.0).
2. Launch your Web browser. Enter the default IP address of your device in the address field. Press Enter
(PC) or Return (Mac).
For Example, enter 192.168.0.254 to access the PharOS.
— 1 —
Chapter 1 Overview
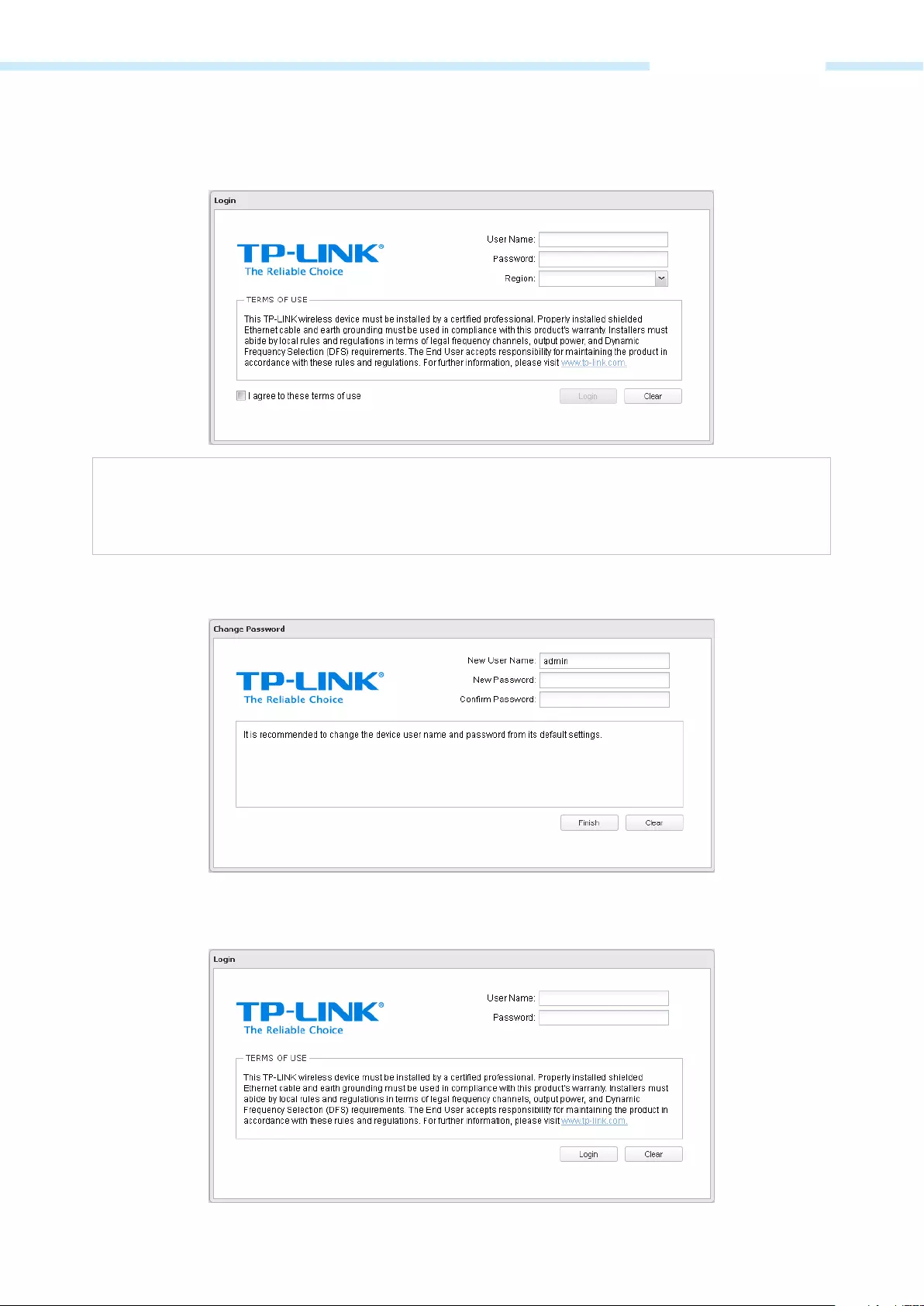
3. Upon initial login, please enter admin in the Username and Password fields, and select the
appropriate region from the Region drop—down lists. Check the box next to I agree to these terms of
use, and click Login.
NOTE:
Ensure you select a correct Region to comply with local laws. Incorrect settings may
regulations.
4. We recommend you change the device’s user name and password from its default settings for
network security. Enter and confirm new user name and password, then click Finish.
5. For subsequent logins, you only need to enter the user name and password that you have set to log
in.
— 2 —
Chapter 1 Overview
Navigation
The PharOS Web Interface contains six main tabs, each of which provides a Web—based management page
to configure the specific parameters of the Pharos series products.
Quick Setup
On Quick Setup Guide, you can quickly configure your device through the step—by—step Quick Setup
Wizard.
Status
The Status Tab displays a summary of the link status information, current values of the basic configuration
settings (depending on the operating mode), network settings and information, and traffic statistics.
Network
The Network Tab configures the function of WAN, LAN, forwarding, security, access control, static routing,
bandwidth control and IP&MAC binding.
Wireless
On The Wireless Tab, you can configure the related wireless parameters in different modes.
Management
The Management Tab configures system management services: System Log, Miscellaneous, Ping Watch
Dog, and Dynamic Domain Name System (DDNS). Web server, Simple Network Management Protocol
(SNMP), SSH server, RSSI LED Thresholds are also available.
System
The System Tab controls system maintenance routines, device customization, location management, user
account management, firmware update, Time setting and configuration backup.
Tools
The Tools list provides some useful tools including Ping, Traceroute, Speed Test, Survey and Spectrum
Analysis.
— 3 —

Chapter 2 Operation Modes
Chapter 2 Operation Modes
The Pharos series products support six modes to satisfy user’s diversified network requirements including
Access Point mode, Client mode, Repeater (Range Extender) mode, Bridge mode, AP Router mode and AP
Client Router (WISP Client) mode. This chapter introduces typical usage scenarios of each mode. You can
choose the desired scenario according to your needs, and refer to the Installation Guide for hardware
connection instruction and Chapter 3 Quick Setup Guide for software configuration.
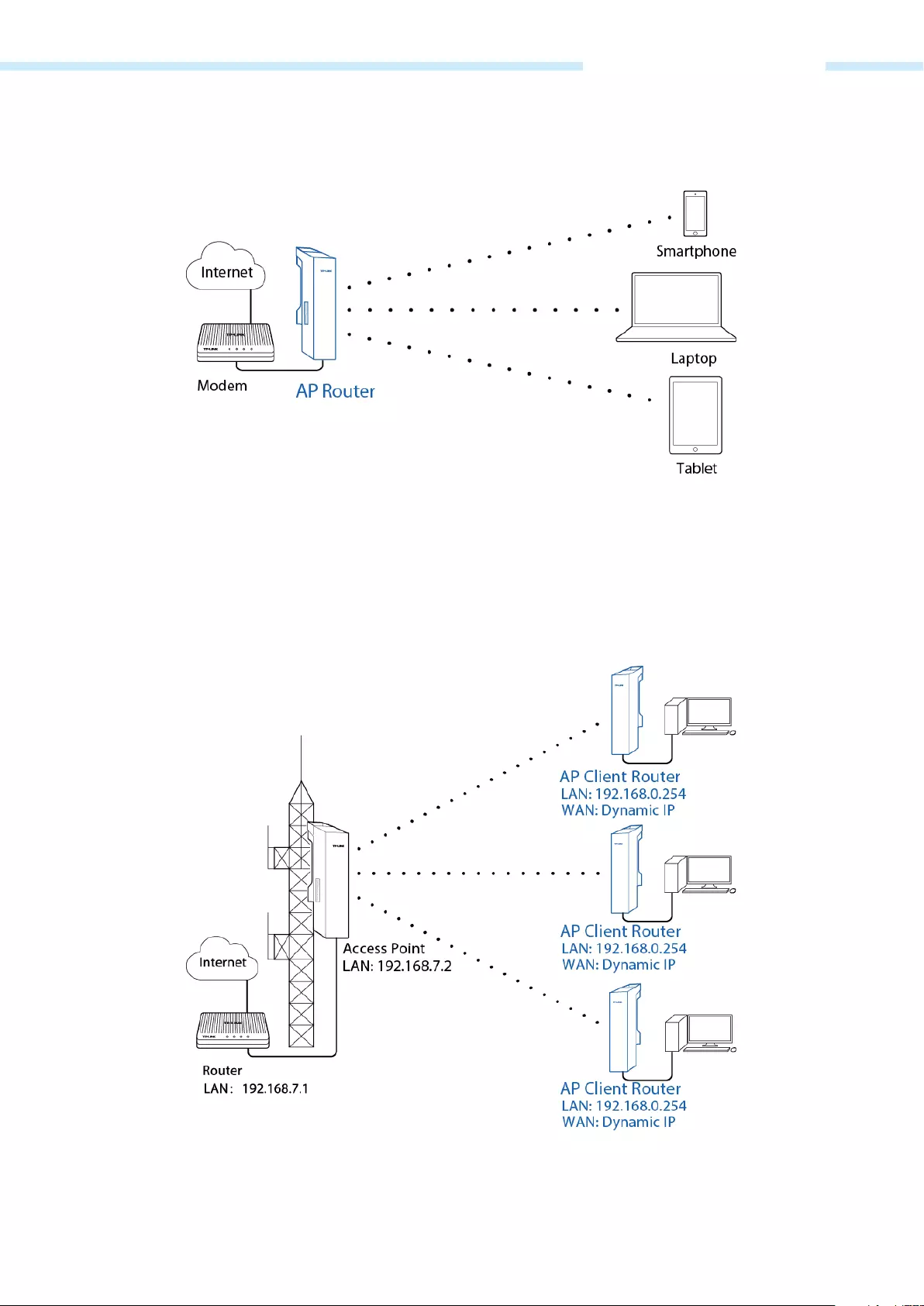
Access Point
In AP mode, the device acts as a central hub and provides wireless access point for wireless clients, thus
the AP mode is very applicable to the following three scenarios. Meanwhile, Multi—SSID function can be
enabled in this mode, providing four wireless networks with different SSIDs and passwords.
Scenario 1
Network requirements: Establish wireless network coverage in the campus, community, industrial park or
public places to provide wireless access points for wireless users.
The device in the network: With the access to campus network or local area network, the device in AP
mode provides the wireless access point based on the existing wired local area network for wireless clients,
such as smart phones, laptops and tablets.
Advantages: Increase wireless access points and enrich the access ways of local area network.
Network diagram:
Scenario 2
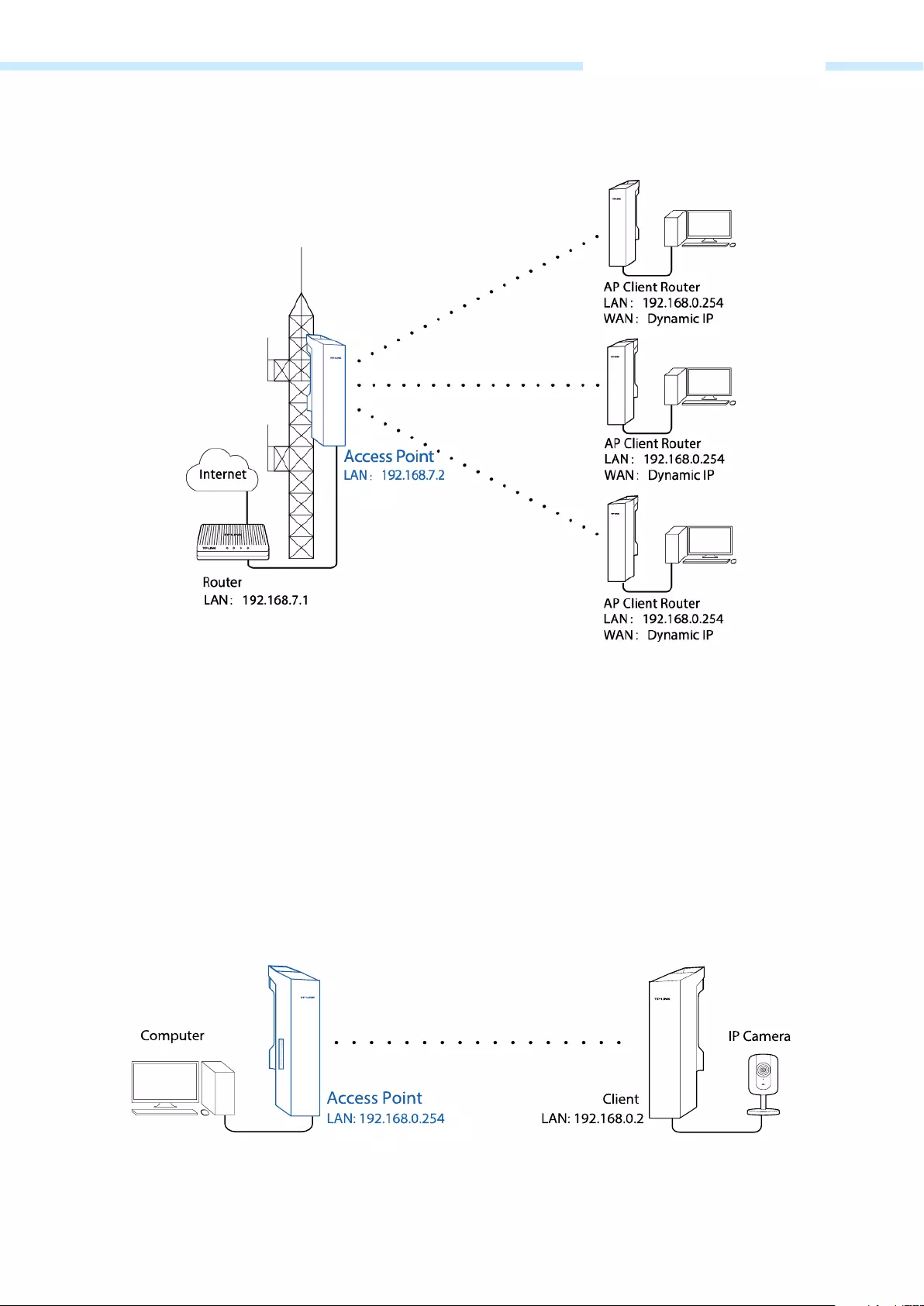
Network requirements: Establish the network coverage in the remote areas without long—distance cabling.
The device in the network: In the adjacent town covered by wired network, ISP (Internet Service Provider)
can put up a device in AP mode with the access to ISP network by connecting to ISP’s router to transform
wired signal into wireless one. The remote users can put up a device in AP Client Router mode to access
the Internet the AP device provides wirelessly.
— 4 —
Chapter 2 Operation Modes
Advantages: Transmit data wirelessly across a long distance and reduce the cabling cost.
Network diagram:
Scenario 3
Network requirements: Establish a point—to—point link for video monitor or combine two separate office
networks as one.
The device in the network: For video monitor, the device in AP mode connects to the monitoring
computer and the device in Client mode connects to IP Camera. For combining two separate office
networks as one, two devices in AP and Client mode respectively connect to the switches in two office
networks so as to connect two office networks.
Advantages: Establish a point—to—point WLAN across a long distance to achieve the connectivity between
two networks and avoid the cabling trouble.
Network diagram:
Video monitor
— 5 —

Chapter 2 Operation Modes
Internet sharing
Client
Network requirements: The most common usage scenario of Client is point—to—point networking with AP
for video monitor or combining two separate office networks. Please refer to Scenario 3 of Access Point
for detailed information.
The device in the network: In this mode, the device actually serves as a wireless adapter to receive the
wireless signal from root AP or Station. In the case, wired devices can access the network provided by root
AP or Station through connecting to Client.
Network diagram:
Video monitor
Internet sharing
— 6 —

Chapter 2 Operation Modes
Repeater (Range Extender)
The device in Repeater mode can extend wireless coverage of an existing wireless network to cover “dead”
spots, especially to eliminate signal—blind corners in a larger space. The SSID and encryption type of the
device should be the same as those of root AP.
Network requirements: Eliminate the wireless signal-blind areas and repeat wireless signal.
The device in the network: In a large campus or industrial park, the device in Repeater mode can reinforce
the wireless signal strength of the existing network and extend the network coverage to eliminate the
signal-blind areas. Remote data can be transmitted across a long distance beyond the transmission range.
Meanwhile, the wireless users can experience a wireless network roaming when moving around.
Network diagram:
Eliminate the wireless signal—blind areas
Repeat wireless signal
— 7 —

Chapter 2 Operation Modes
Bridge
Network requirements: Reinforce the wireless signal strength of the root AP device to eliminate the
wireless signal—blind areas. Meanwhile, the wireless users can use the SSID and encryption type different
from those of the root AP device to access the network.
The device in the network: Similar to the Repeater mode, the Bridge mode is used to reinforce the exiting
wireless signal. However, the very difference is that the Bridge has its own SSID and encryption type
different from those of root AP.
Network diagram:
Eliminate the wireless signal—blind areas
Bridge for wireless signal
AP Router
Network requirements: Establish the wireless network coverage in the campus, community, industrial park
or other public places and so on.
The device in the network: Similar to the home wireless router, the device in AP Router mode connects to
root ADSL/Cable Modem. The difference lies in that the coverage area of this device is wider. Smart
— 8 —
Chapter 2 Operation Modes
phones, laptops, and other wireless clients can share wide area network via the access to wireless network
this device provides.
Network diagram:
AP Client Router (WISP Client)
In AP Client Router mode, after accessing the wireless network provided by WISP, the device provides
wireless network service for downstream wireless clients. Meanwhile, the device allows wired devices,
such as desktop computer, to access it via LAN1 port or PoE adapter’s LAN port. In this way, all members of
a home user can share the Internet using one account applied from WISP.
— 9 —
Chapter 3 Quick Setup Guide
Chapter 3 Quick Setup Guide
Quick Setup wizard allows you to quickly configure your device step by step. Choose the suitable
operation mode according to your network environment and follow the step—by—step instructions.
Access Point
If Access Point is selected, click Next and take the following steps:
1. The LAN Settings page will appear as shown below. The default IP Address is 192.168.0.254 and the
default Subnet Mask is 255.255.255.0. You can change the IP Address and Subnet Mask on this page
when there is an IP conflict with other devices. We recommend you keep it by default. Click Next.
— 10 —
Chapter 3 Quick Setup Guide
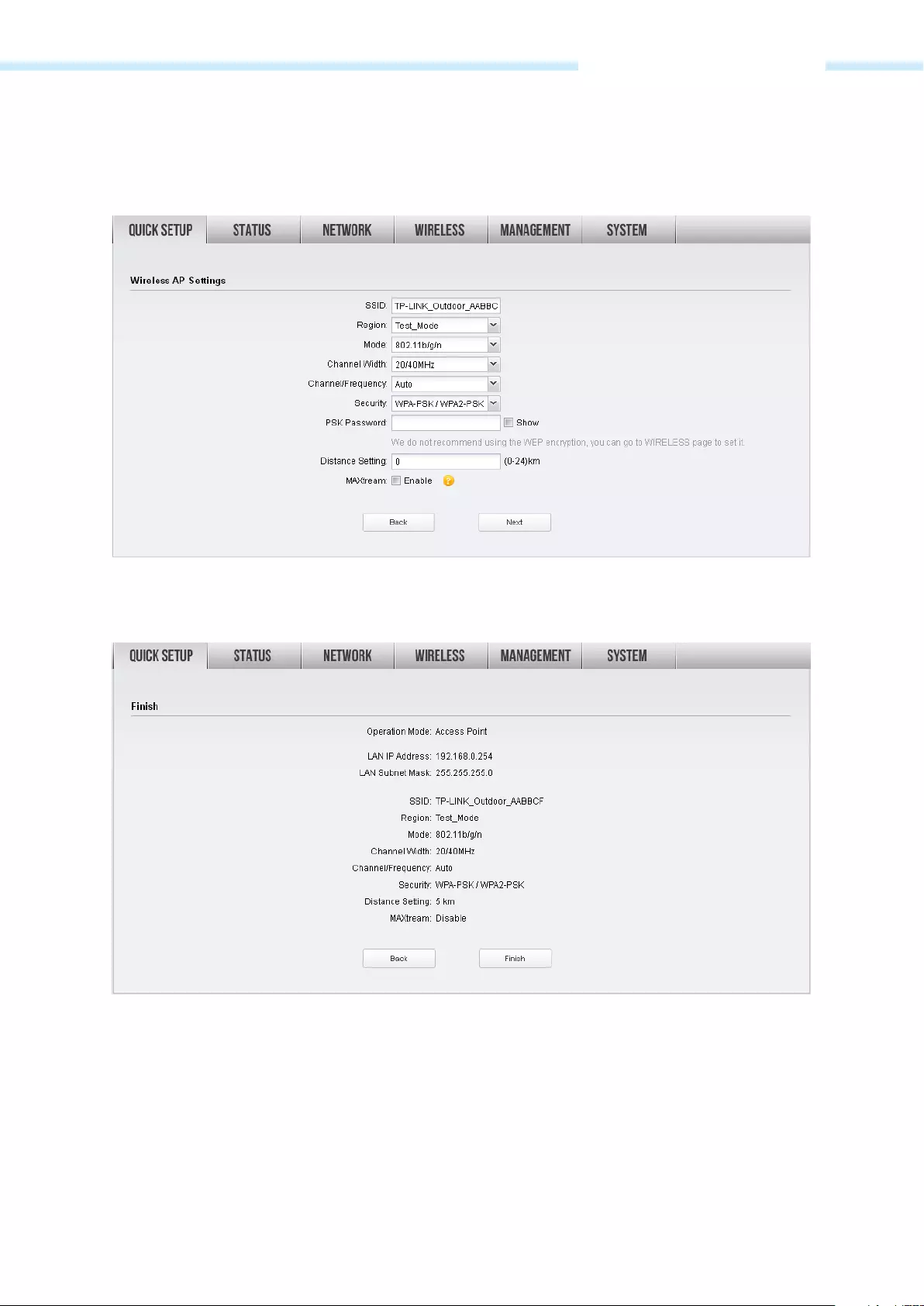
2. The Wireless AP Settings page will appear as shown below. Create an easy—to—remember name for
your wireless network. Select WPA—PSK/WPA2—PSK in the Security box and enter the PSK Password
below to prevent unauthorized access to your AP. Enter the distance between this device and the
furthest client in Distance Setting. Then click Next.
3. The Finish page will appear and display what you’ve configured previously. If you want to modify any
parameter, click Back to reconfigure it. If all are confirmed, click Finish to complete the configuration.
— 11 —
Chapter 3 Quick Setup Guide
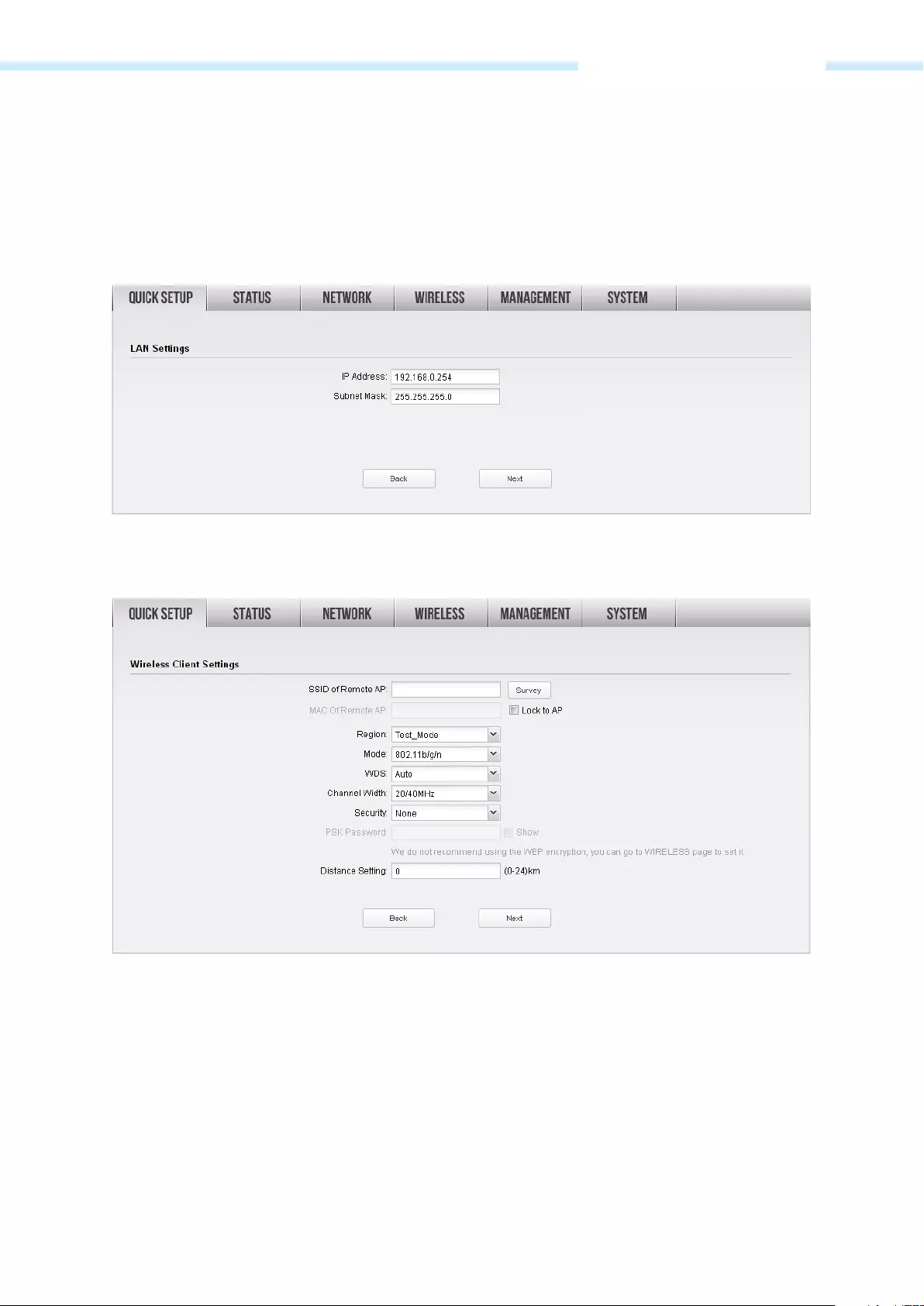
Client
If Client is selected, click Next and take the following steps:
1. The LAN Settings page will appear as shown below. The default IP Address is 192.168.0.254 and the
default Subnet Mask is 255.255.255.0. You can change the IP Address and Subnet Mask on this page
when there is an IP conflict with other devices. We recommend you keep it by default. Click Next.
2. The Wireless Client Settings page will appear as shown below. Click Survey to search for wireless
networks.
— 12 —
Chapter 3 Quick Setup Guide
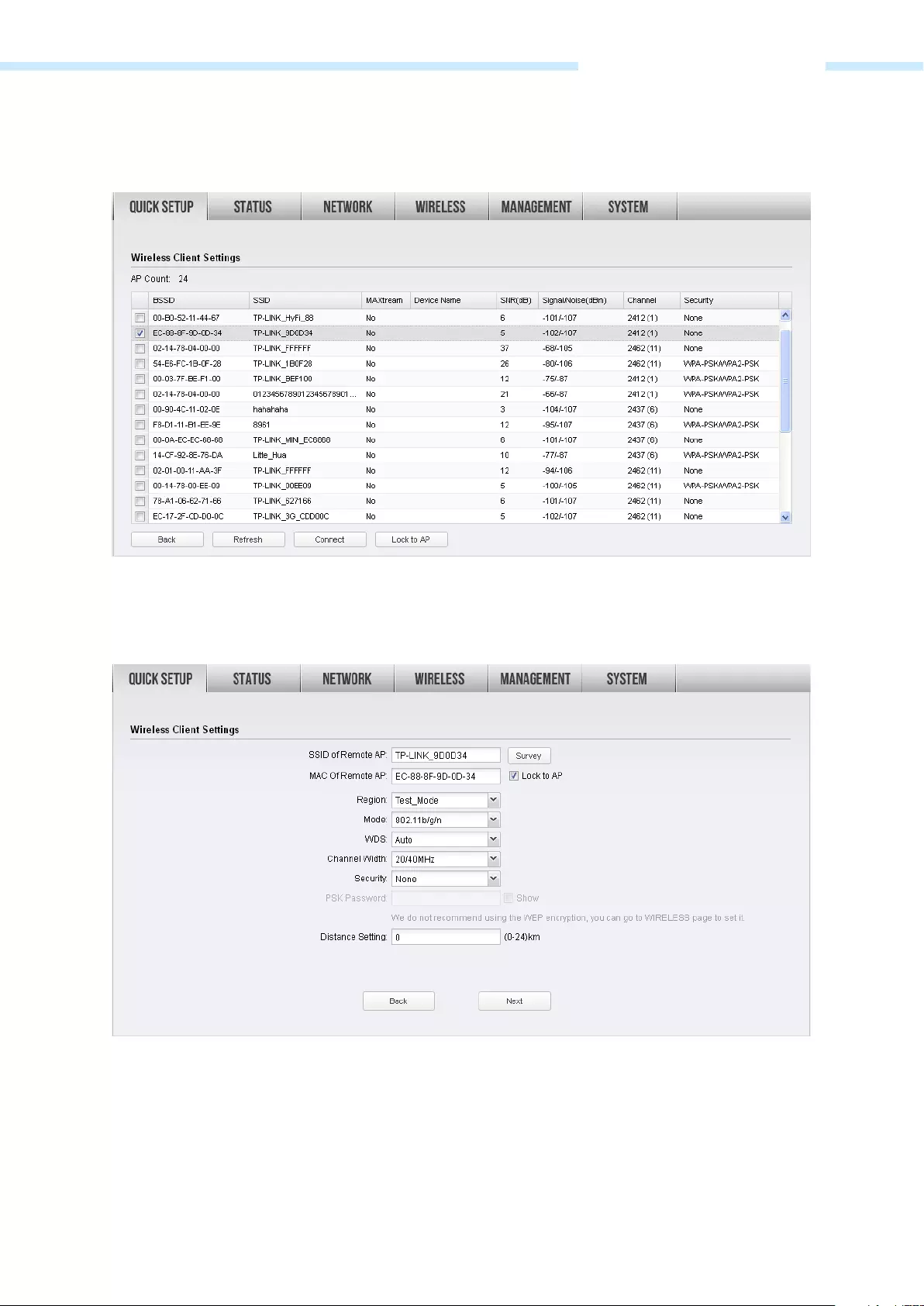
3. The AP list will appear as shown below. Select the desired wireless network and click Connect. It’s
possible that two or more networks use the same SSID in the AP list. Lock to AP can make the device
connect to the specified AP you had connected before the next time.
4. If the root AP needs password to be connected, you should select the same Mode, Channel Width
and Security type and enter the same PSK Password as entered on the root AP/router. Enter the
distance between this device and the root AP in Distance setting. Then click Next.
— 13 —
Chapter 3 Quick Setup Guide
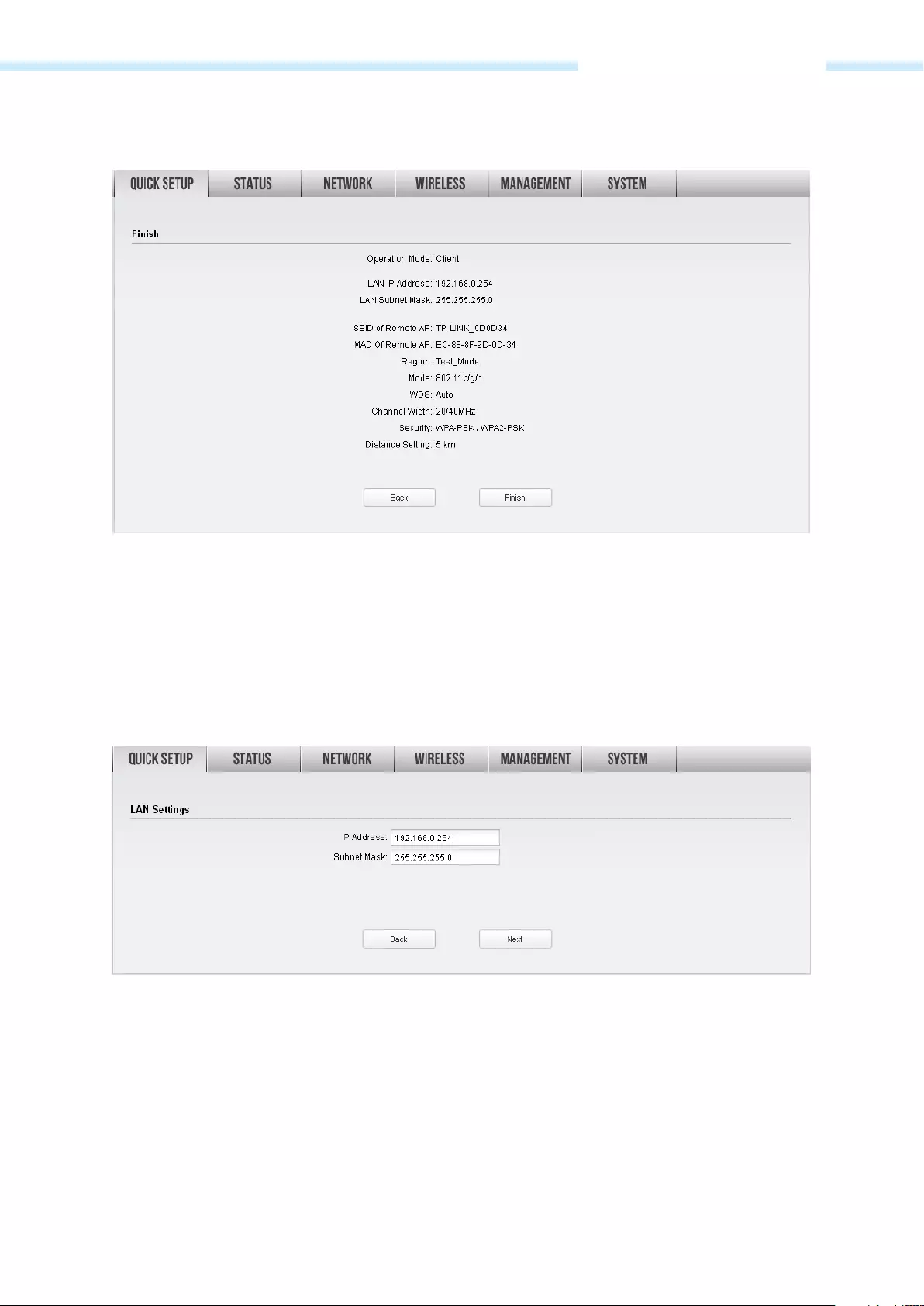
5. The Finish page will appear and display what you’ve configured previously. If you want to modify any
parameter, click Back to reconfigure it. If all are confirmed, click Finish to complete the configuration.
Repeater (Range Extender)
If Repeater (Range Extender) is selected, click Next and take the following steps:
1. The LAN Settings page will appear as shown below. The default IP Address is 192.168.0.254 and the
default Subnet Mask is 255.255.255.0. You can change the IP Address and Subnet Mask on this page
when there is an IP conflict with other devices. We recommend you keep it by default. Click Next.
— 14 —
Chapter 3 Quick Setup Guide
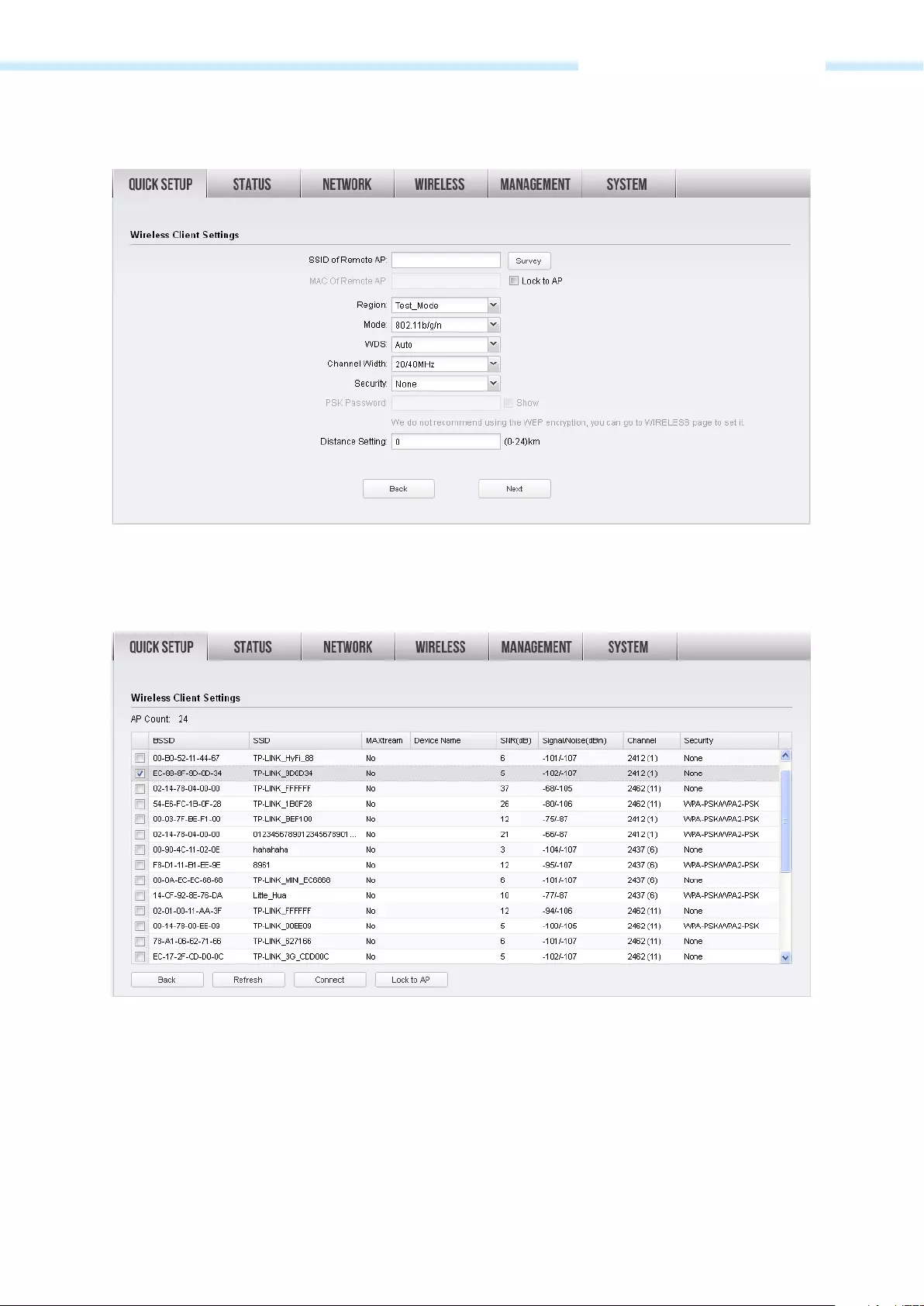
2. The Wireless Client Settings page will appear as shown below. Click Survey to search for wireless
networks.
3. The AP list will appear as shown below. Select the desired wireless network and click Connect. It’s
possible that two or more networks use the same SSID in the AP list. Lock to AP can make the device
connect to the specified AP you had connected before the next time.
— 15 —

Chapter 3 Quick Setup Guide
4. If the root AP needs password to be connected, you should select the same Mode, Channel Width
and Security type and enter the same PSK Password as entered on the root AP/router. Enter the
distance between this device and the root AP/router in Distance setting. Then click Next.
5. The Finish page will appear and display what you’ve configured previously. If you want to modify any
parameter, click Back to reconfigure it. If all are confirmed, click Finish to complete the configuration.
— 16 —

Chapter 3 Quick Setup Guide
Bridge
If Bridge is selected, click Next and take the following steps:
1. The LAN Settings page will appear as shown below. The default IP Address is 192.168.0.254 and the
default Subnet Mask is 255.255.255.0. You can change the IP Address and Subnet Mask on this page
when there is an IP conflict with other devices. We recommend you keep it by default. Click Next.
2. The Wireless Client Settings page will appear as shown below. Click Survey to search for wireless
networks.
— 17 —

Chapter 3 Quick Setup Guide
3. The AP list will appear as shown below. Select the desired wireless network and click Connect. It’s
possible that two or more networks use the same SSID in the AP list. Lock to AP can make the device
connect to the specified AP you had connected before the next time.
4. If the root AP needs password to be connected, you should select the same Mode, Channel Width
and Security type and enter the same PSK Password as entered on the root AP. Enter the distance
between this device and the root AP/router in Distance setting. Then click Next.
— 18 —
Chapter 3 Quick Setup Guide
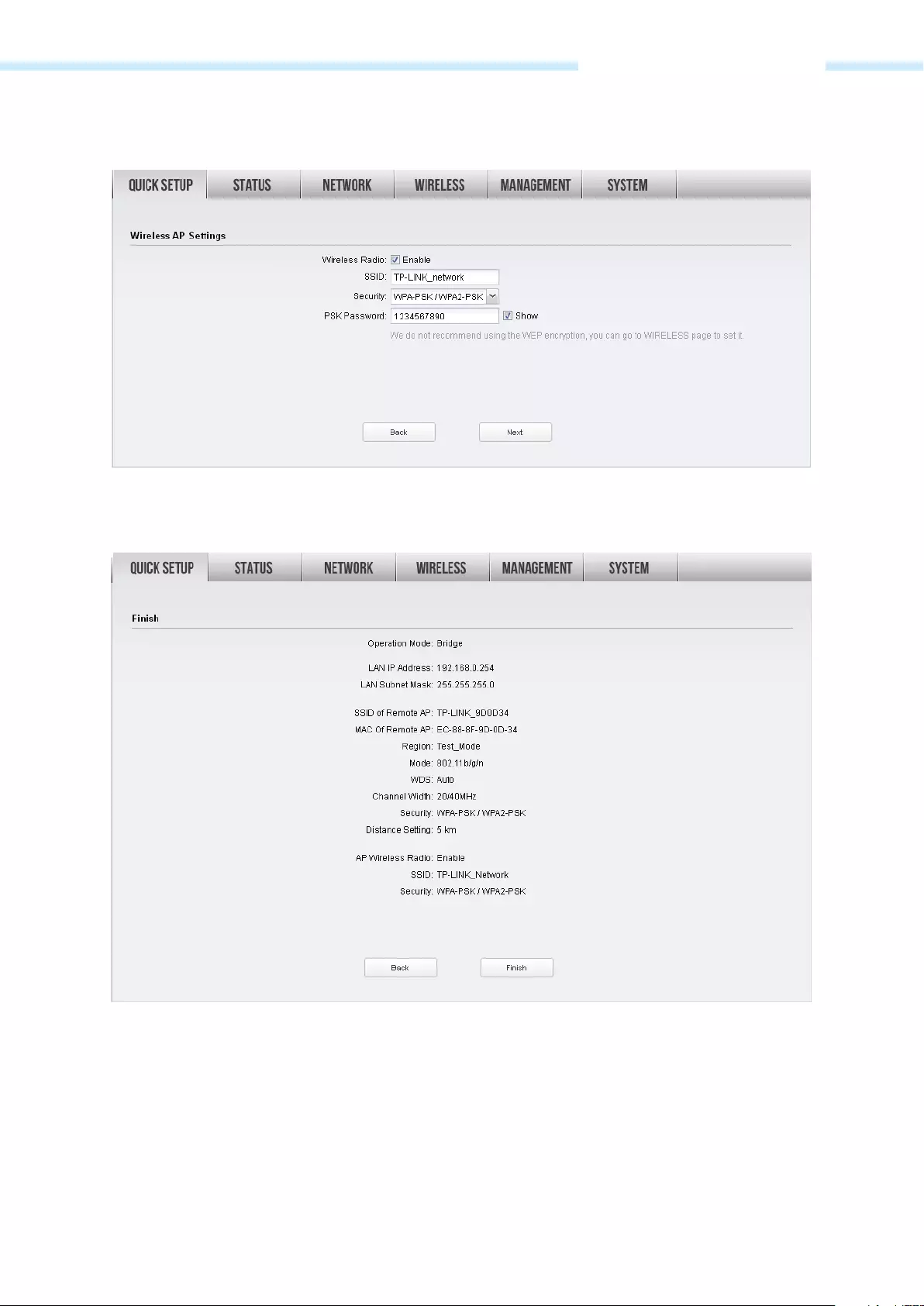
5. Create a new SSID and PSK password for the local wireless network. The wireless AP settings for the
local network will be set the same as your root AP by default. Click Next.
6. The Finish page will appear and display what you’ve configured previously. If you want to modify any
parameter, click Back to reconfigure it. If all are confirmed, click Finish to complete the configuration.
— 19 —

Chapter 3 Quick Setup Guide
AP Router
If AP Router is selected, click Next and take the following steps:
1. The WAN Connection Type page will appear as shown below. Choose the suitable WAN connection
type, and then click Next.
2. The router supports three popular ways PPPoE, Dynamic IP and Static IP to connect to the Internet.
To make sure the connection type your ISP provides, please refer to the ISP.
PPPoE — If your ISP delivers Internet through phone line and provides you with username and
password, you should choose this type. Under this condition, you should fill in both User Name and
Password that the ISP supplied, and then click Next to proceed. Please note that these fields are case—
sensitive.
Dynamic IP — For this connection, Your ISP uses a DHCP server to assign your router an IP address for
connecting to the Internet. You don’t need to configure any parameters, Click Next to proceed.
— 20 —
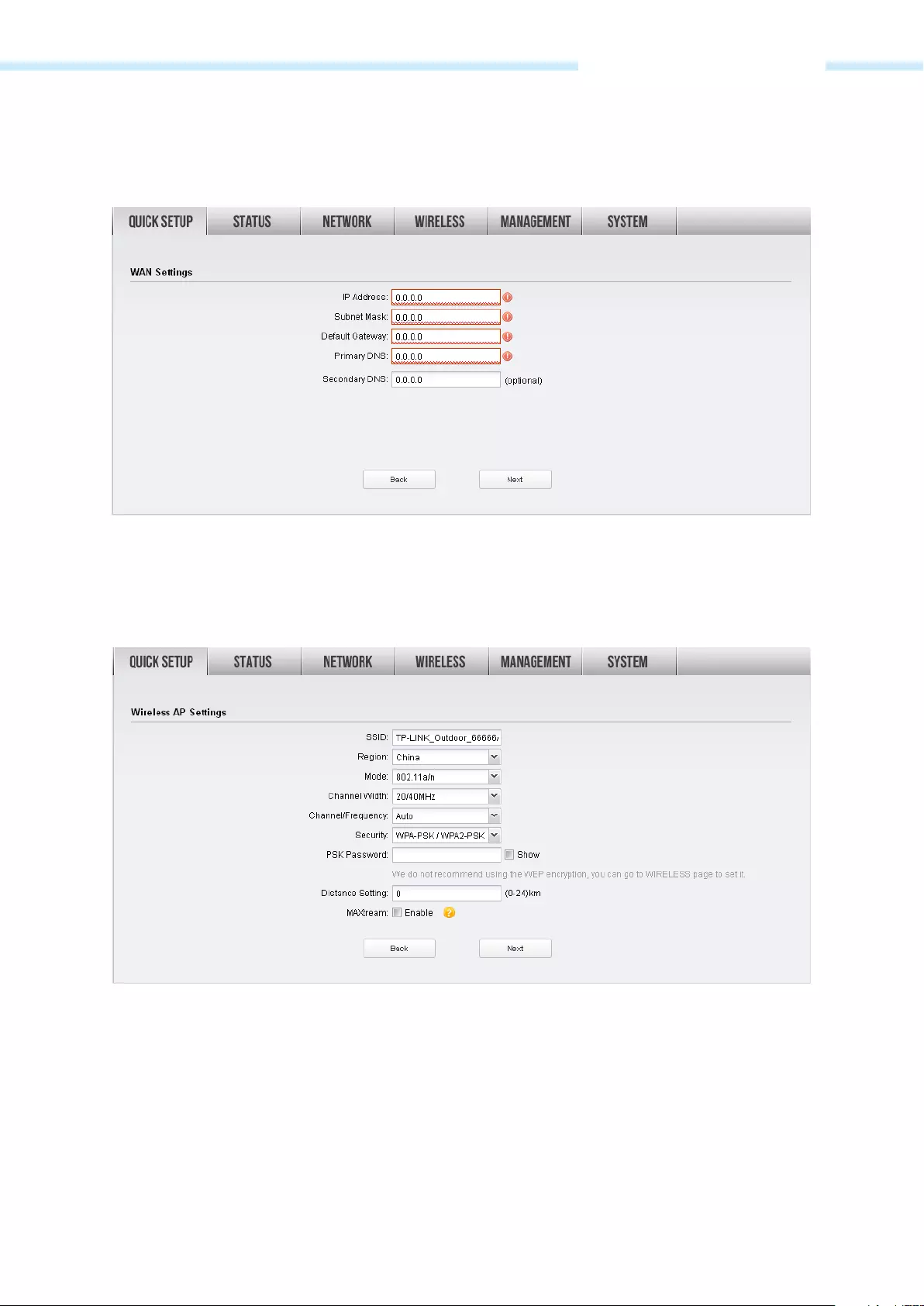
Chapter 3 Quick Setup Guide
Static IP — This type of connection uses a permanent, fixed (static) IP address that your ISP assigned. In
this type, you should fill in the IP address, Subnet Mask, Default Gateway, and DNS IP address
manually, which are specified by your ISP. Then click Next to proceed.
3. After configuring WAN connection type, the Wireless AP Settings page will appear as shown below.
Create an easy—to—remember name for your wireless network. Select WPA—PSK/WPA2—PSK in the
Security box and enter the PSK Password below to prevent unauthorized access to your AP. Enter the
distance between this device and the furthest client in Distance Setting. Then click Next.
— 21 —
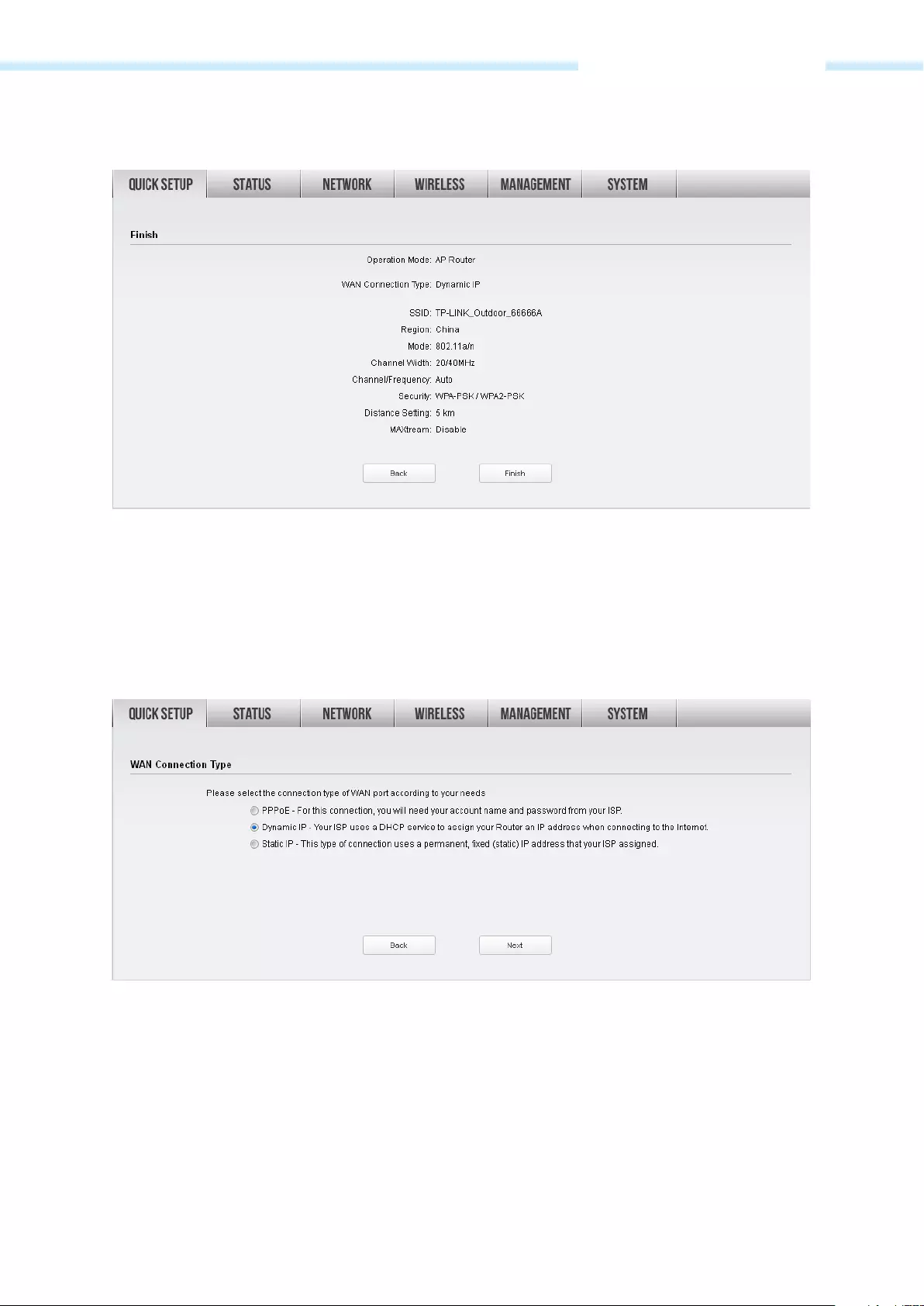
Chapter 3 Quick Setup Guide
4. The Finish page will appear and display what you’ve configured previously. If you want to modify any
parameter, click Back to reconfigure it. If all are confirmed, click Finish to complete the configuration.
AP Client Router (WISP Client)
If AP Client Router (WISP Client) is selected, click Next and take the following steps:
1. The WAN Connection Type page will appear as shown below. Choose the suitable WAN connection
type, and then click Next.
2. The router supports three popular ways PPPoE, Dynamic IP and Static IP to connect to the Internet.
To make sure the connection type your ISP provides, please refer to the ISP.
— 22 —

Chapter 3 Quick Setup Guide
PPPoE — If your ISP delivers Internet through phone line and provides you with username and
password, you should choose this type. Under this condition, you should fill in both User Name and
Password that the ISP supplied, and then click Next to proceed. Please note that these fields are case—
sensitive.
Dynamic IP — For this connection, Your ISP uses a DHCP server to assign your router an IP address for
connecting to the Internet. You don’t need to configure any parameters, Click Next to proceed.
Static IP — This type of connection uses a permanent, fixed (static) IP address that your ISP assigned. In
this type, you should fill in the IP address, Subnet Mask, Default Gateway, and DNS IP address
manually, which are specified by your ISP. Then click Next to proceed.
— 23 —
Chapter 3 Quick Setup Guide
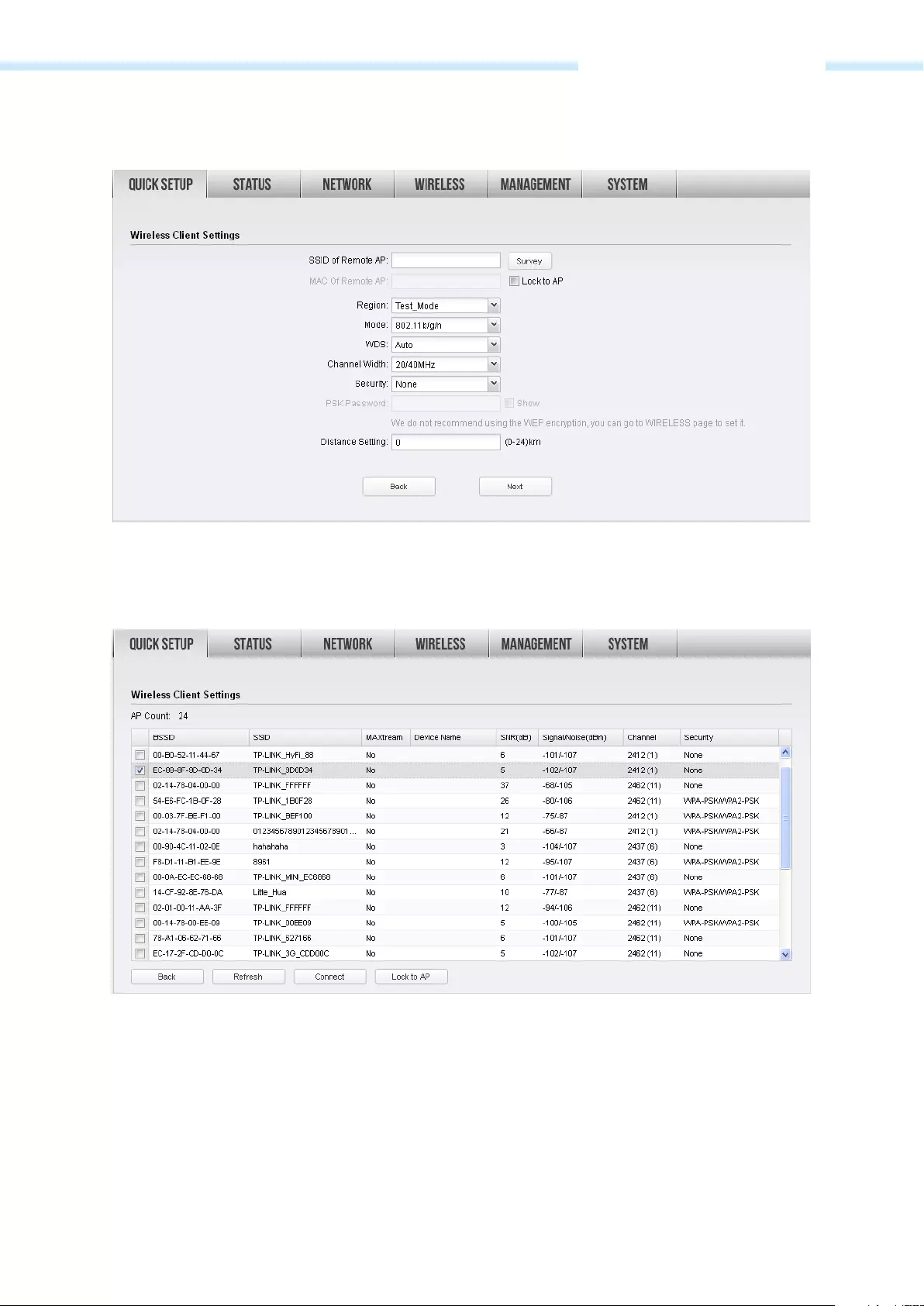
3. After configuring WAN connection type, The Wireless Client Settings page will appear as shown
below. Click Survey to search for wireless networks.
4. The AP list will appear as shown below. Select the desired wireless network and click Connect. It’s
possible that two or more networks use the same SSID in the AP list. Lock to AP can make the device
connect to the specified AP you had connected before the next time.
— 24 —

Chapter 3 Quick Setup Guide
5. If the root AP needs password to be connected, you should select the same Mode, Channel Width
and Security type and enter the same PSK Password as entered on the root AP/router. Enter the
distance between this device and the root AP/router in Distance setting. Then click Next.
6. Create a new SSID and PSK password for the local wireless network. The wireless AP settings for the
local network will be set the same as your root AP by default. Click Next.
— 25 —
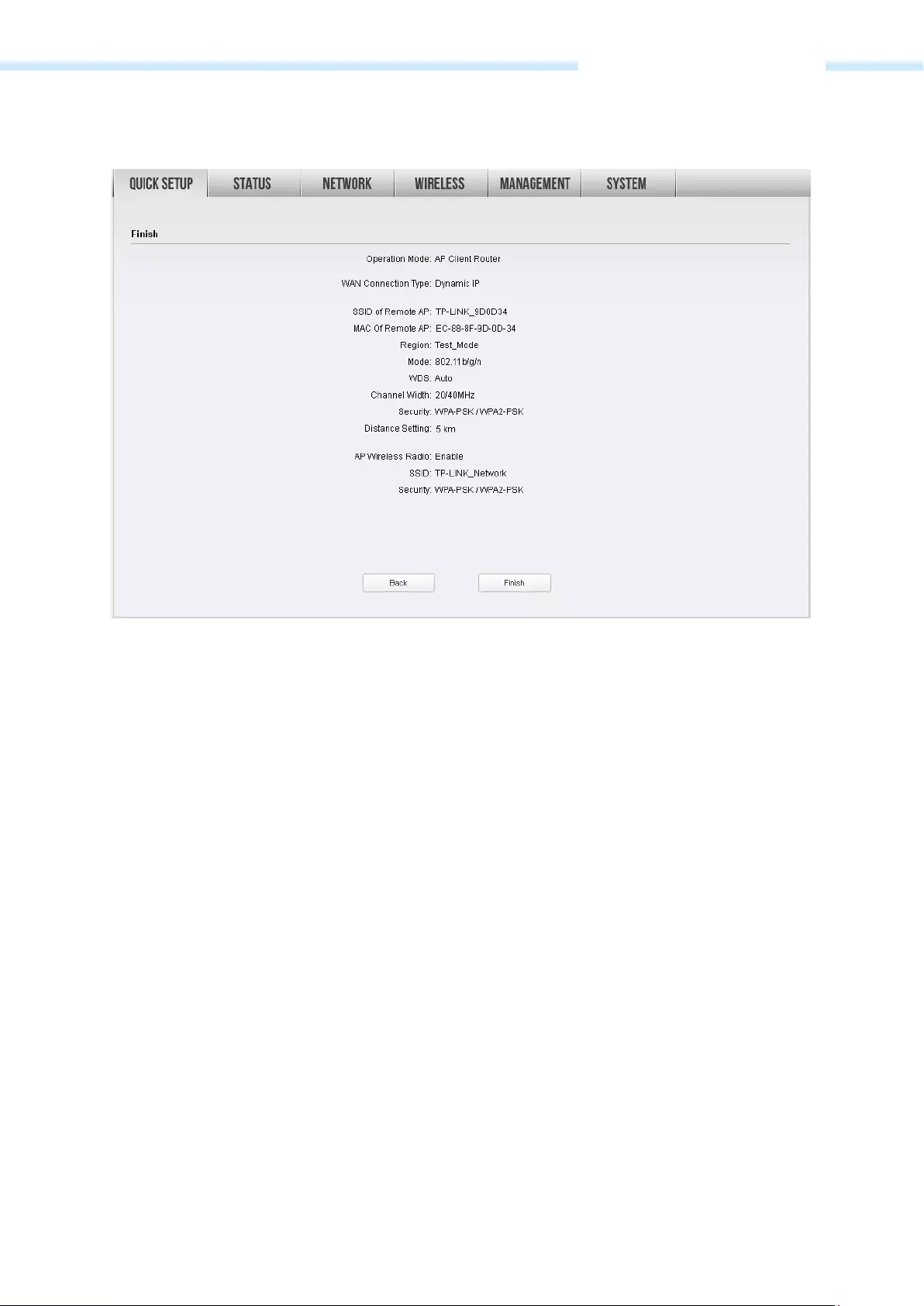
Chapter 3 Quick Setup Guide
7. The Finish page will appear and display what you’ve configured previously. If you want to modify any
parameter, click Back to reconfigure it. If all are confirmed, click Finish to complete the configuration.
— 26 —

Chapter 4 Status Tab
Chapter 4 Status Tab
The Status tab displays a summary of the link status information, current values of the basic configuration
settings (depending on the operating mode), network settings and information, and traffic statistics.
— 27 —
Chapter 4 Status Tab
Status Information
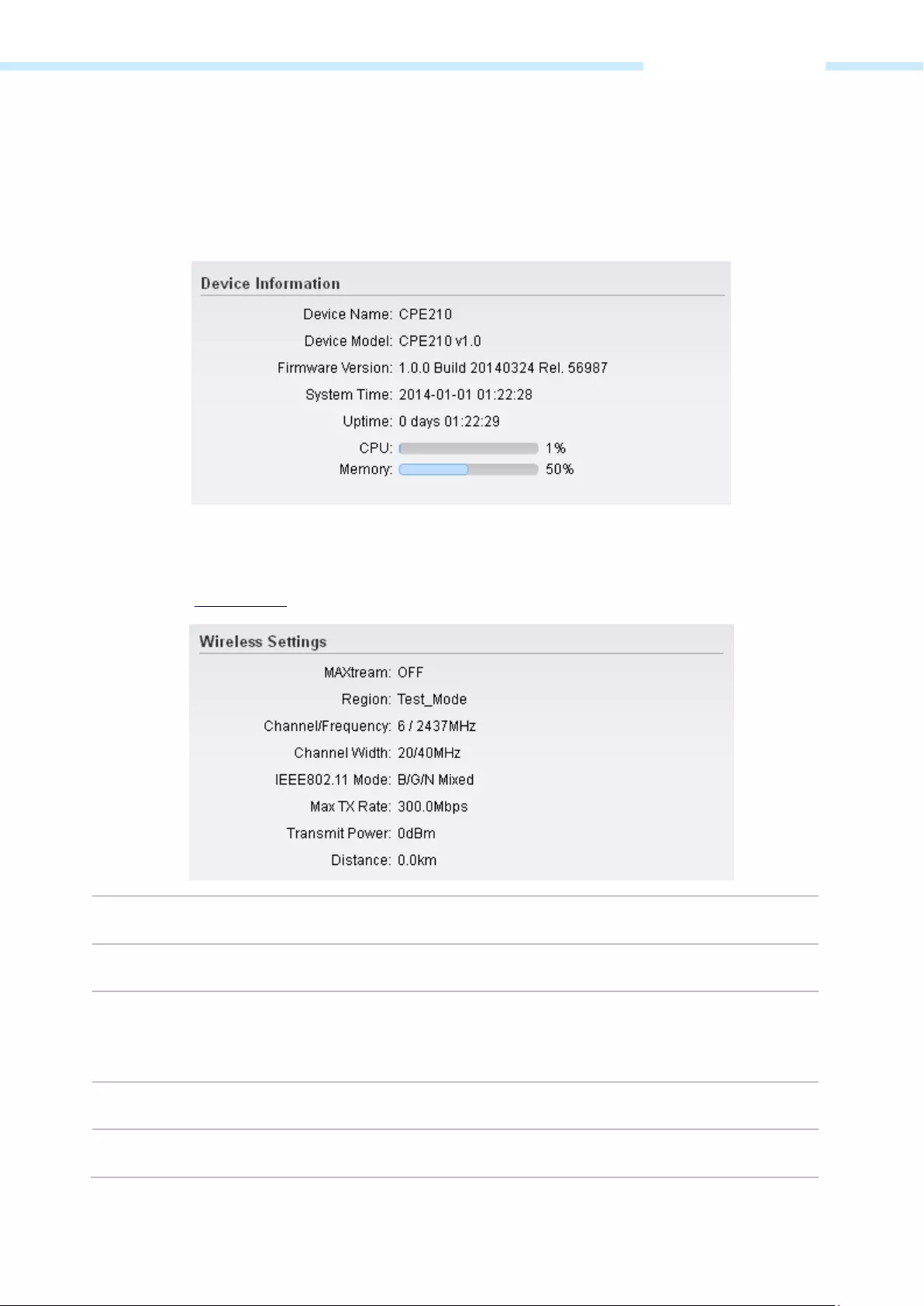
Device Information
Device information displays the customizable name, model, firmware version, system time, uptime, CPU
and memory of the device.
Wireless Settings
Wireless settings display the relative wireless parameters of the current device. You can change the
parameters in Wireless tab.
MAXtream Displays whether the MAXtream function is ON.
Region Displays the region you’ve selected.
Channel/Frequency Displays
the channel number and corresponding operating frequency. The device
uses the channel and radio frequency specified to transmit and receive data. Valid
channel and frequency ranges will vary depending on local regulations.
Channel Width Displays the spectral width of the radio channel used by the device.
IEEE802.11 Mode Displays the radio standard used for operation of your device.
— 28 —

Chapter 4 Status Tab
Max TX Rate Displays the data rate at which the device should transmit wireless packets.
Transmit Power Displays the current transmit power of the device.
Distance Displays the wireless coverage distance where the client devices can be placed
from the AP to get good wireless performance. You can change the value in
Wireless Advanced Settings.
Wireless Signal Quality
Status of wireless signal quality displays the parameters of the received wireless signal in the modes of
Client, Repeater (Range Extender), Bridge and AP Client Router. The parameters here is not applicable for
other two modes.
Signal Strength Displays the received wireless signal strength of the root AP.
Noise Strength Displays the received environmental noise from wireless interference
operating frequency.
SNR Signal to Noise Ratio, the power ratio between the received wireless signal strength
and the environmental noise strength. Gener
ally, in order to achieve the best
performance, users need to adjust the antenna to get the best SNR.
Transmit CCQ Displays the wireless Client Connection Quality (CCQ). CCQ refers to the ratio of
current effective transmission bandwidth and the theoretically maximum available
bandwidth. CCQ reflects the actual link condition.
Radio Status
Radio status shows the MAC address, SSID, security mode and connected station number of the enabled
AP. If the Client mode is enabled, the information of MAC address, security mode, WDS, root AP BSSID, root
AP SSID, TX rate, RX rate and connection time of the client will also be displayed.
— 29 —

Chapter 4 Status Tab
AP Displays whether
the AP function is Enabled or Disabled. It is enabled in Access
Point, Repeater, Bridge, AP Router and AP Clien
t Router modes and disabled in
Client mode by default.
MAC Address Displays the MAC address of AP interface or client interface.
SSID Displays the wireless network name (SSID).
Security Mode Displays the security mode you’ve chosen for your wireless network. There are
three security modes: WPA—PSK, WPA and WEP. None means that no security mode
is selected and all the hosts are allowed to access the wireless network.
Connected Station Displays the number of the connected stations.
Client Displays whether the Client function is Enabled or Disabled. It is enabled in Client,
Repeater, Bridge and AP Client Router modes and disabled in Access Point and AP
Router modes by default.
WDS Displays whether the Wireless Distribution System (WDS) is enabled or not.
Root AP BSSID Displays the basic service set identification (MAC address) of root AP.
Root AP SSID Displays the wireless network name of root AP.
TX Rate Displays the data rate at which the device transmits wireless packets.
— 30 —

Chapter 4 Status Tab
RX Rate Displays the data rate at which the device receives wireless packets.
Connection Time Displays the amount of time the device has been connected to the root AP.
LAN
It displays the relative LAN parameters of the current device. You can change the parameters in Network
Tab.
MAC Address Displays the MAC address of the device.
IP Address Displays the IP address of the device.
Subnet Mask Displays the Subnet Mask of the LAN.
Port Displays the current status of the LAN Ethernet port connections
Maximum transmission rate of the plugged port.
WAN
It displays the relative WAN parameters of the current device. You can change the parameters in Network
Tab.
Connection Type Displays the WAN connection type of the device.
MAC Address Displays the MAC address of the device’s WAN port.
IP Address Displays the IP address of the device’s WAN port.
— 31 —
Chapter 4 Status Tab
Subnet Mask Displays the Subnet Mask of the WAN.
Default Gateway Displays the default gateway.
DNS Server Displays the current DNS IP address.
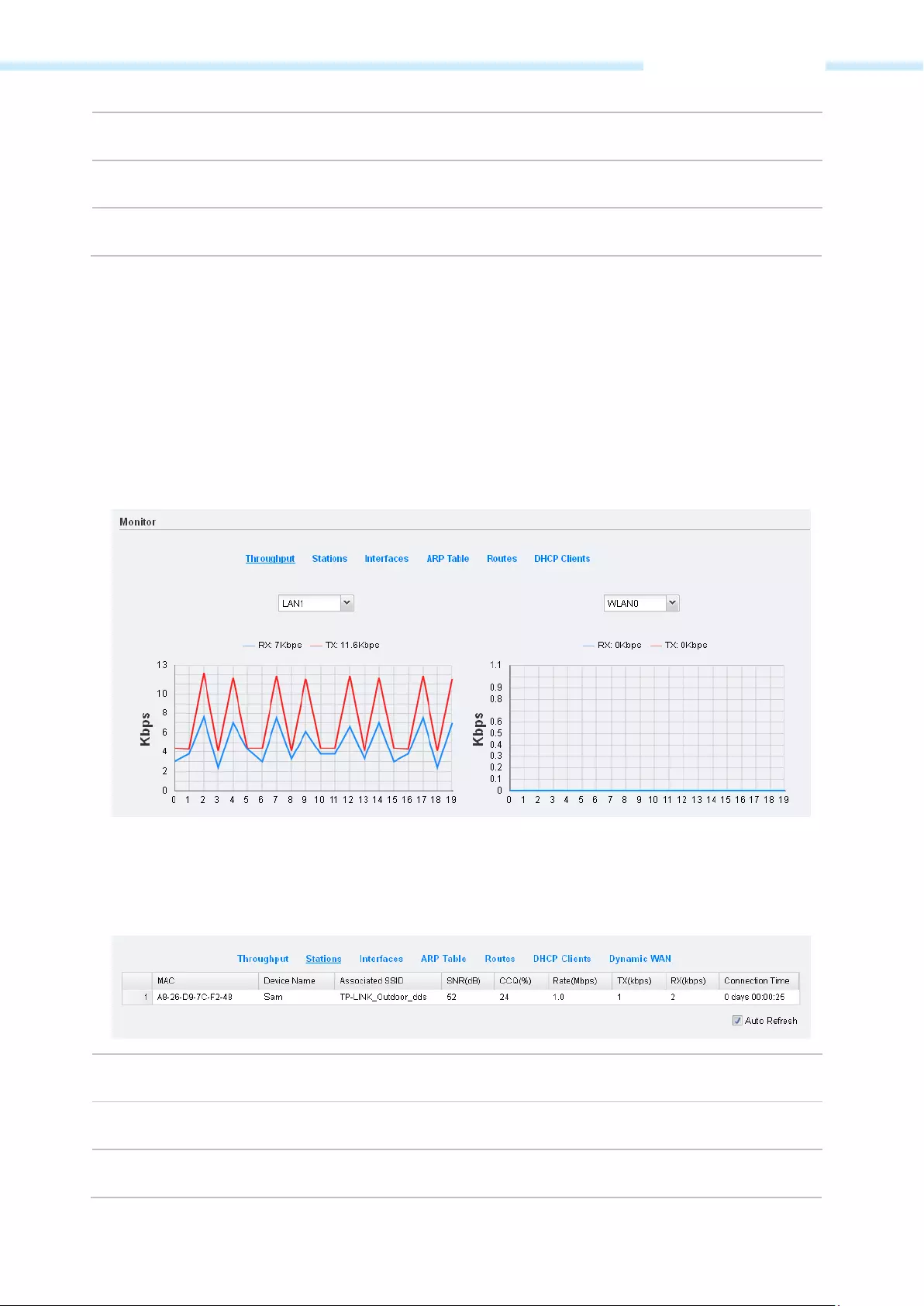
Monitor
The monitor displays the data changes of throughput, Stations, Interfaces, ARP table, Routes, DHCP Clients
and Dynamic WAN of the device.
Throughput
Throughput displays the current data traffic on the interfaces of LAN, WLAN and BRIDGE in both graphical
and numerical form. You can choose the specific interface to monitor from the drop—down list above the
chart.
Stations
In the modes with the AP function enabled, you can monitor the information of all the stations that are
connected to the device.
MAC Displays the MAC address of the station.
Device Name Displays the station’s host name.
Associated SSID The SSID that the station connected to.
— 32 —
Chapter 4 Status Tab
SNR (dB) Signal to Noise Ratio, the power ratio between the rece
strength and the environmental noise strength. Generally, in order to achieve
the best performance, users need to adjust the antenna to get the best SNR.
CCQ (%) Displays the wireless Client Connection Quality (CCQ) of the station.
Rate (Mbps) Displays the station’s data rates of the last transmitted packets.
RX (kbps) Displays the station’s average data rates of the received packet
connection time.
TX (kbps) Displays the station’s average data rates of the transmitted packets over the
connection time.
Auto Refresh If Auto Refresh is checked, parameters in the table will refresh automatically.
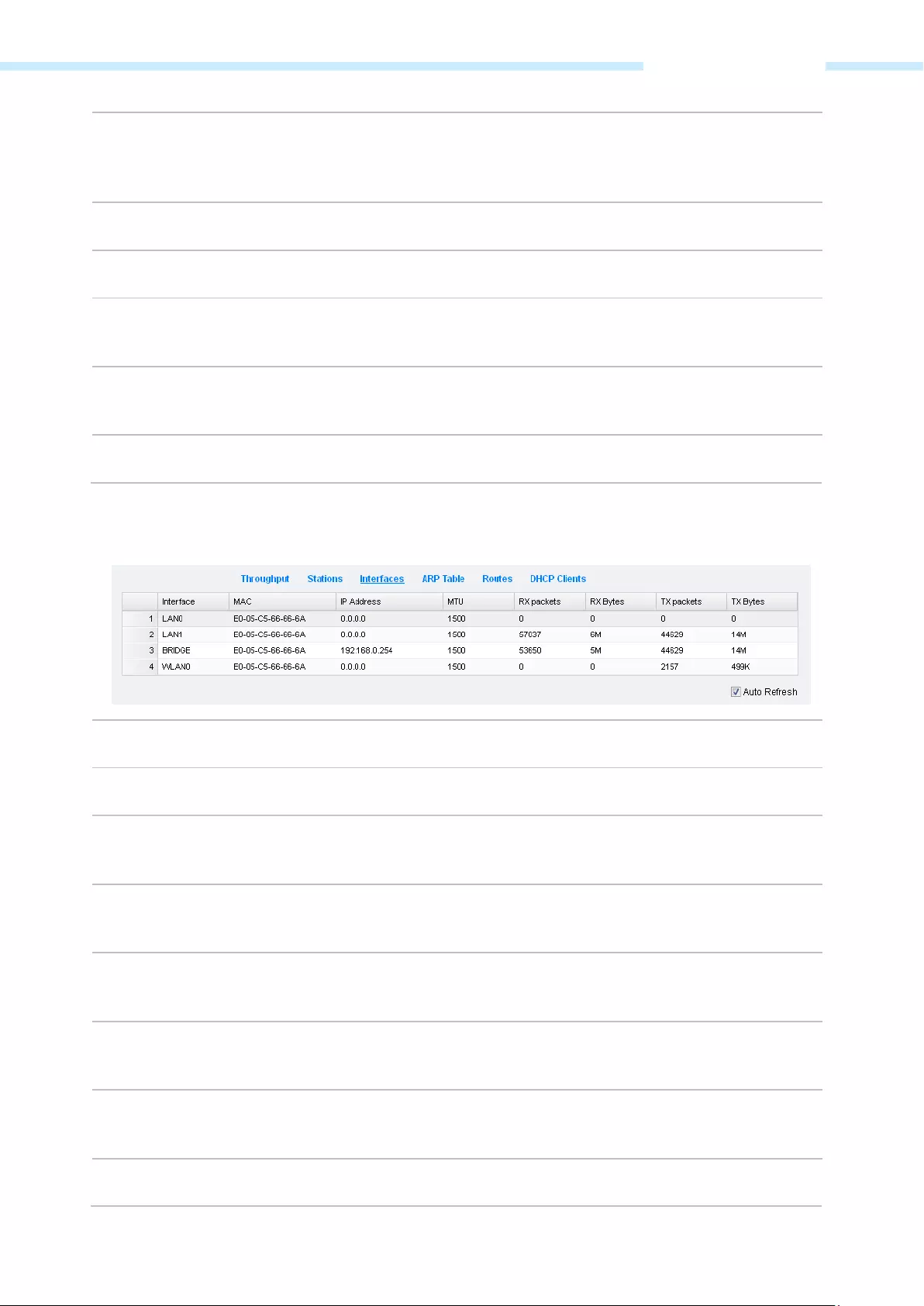
Interfaces
The table displays the relevant information of each interface including MAC, IP address, etc.
MAC Displays the MAC address of the interface.
IP Address Displays the IP address of the interface.
MTU Displays the Maximum Transmission Unit (MTU), which is the maximum packet
size (in bytes) that a network interface can transmit.
RX packets Displays the total amount of packets received by the interface after the device is
powered on.
RX Bytes Displays the total amount of data (in bytes) received by the interface after the
device is powered on.
TX packets Displays the total amount of packets transmitted by the interface after the device
is powered on.
TX Byte Displays the total amount of data (in bytes) transmitted by the interface after the
device is powered on.
Auto Refresh If Auto Refresh is checked, parameters in the table will refresh automatically.
— 33 —

Chapter 4 Status Tab
ARP table
Lists all the entries of the Address Resolution Protocol (ARP) table currently recorded on the device. ARP is
used to associate each IP address to the unique hardware MAC address of each device on the network.
IP Address Displays the IP address assigned to a network device.
MAC Displays the MAC address of the device.
Interface Displays the interface that connects to the device.
Auto Refresh If Auto Refresh is checked, parameters in the table will refresh automatically.
Routes
List all the entries in the system routing table. PharOS examines the destination IP address of each data
packet traveling through the system and chooses the appropriate interface to forward the packet to.
Routing depends on static routing rules, which are registered in the system routing table. Static routes to
specific hosts, networks, or the default gateway are set up automatically according to the IP configuration
of all the Interfaces.
Destination Displays the IP address of the destination device or destination network.
Gateway Displays the IP address of the appropriate gateway.
Subnet Mask Displays the Subnet Mask of the destination device.
Interface Displays the interface that the destination device is on.
Auto Refresh If Auto Refresh is checked, parameters in the table will refresh automatically.
DHCP Clients
DHCP Clients display the current information of the clients including client names, MAC addresses, IP
addresses assigned by the device’s DHCP server and their lease time.
— 34 —

Chapter 4 Status Tab
Client Name Displays the device name of the client.
MAC Address Displays the client’s MAC Address.
IP Address Displays the IP address assigned to the client.
Lease Time Displays
the time of the DHCP client leased. Before the time is up, DHCP client
will request to renew the lease automatically.
Auto Refresh If Auto Refresh is checked, parameters in the table will refresh automatically.
Dynamic WAN
NOTE:
This submenu is only available in AP router mode and AP client router (WISP Client) mode when the
WAN connection type is PPPoE, PPTP, L2TP or Dynamic.
Dynamic WAN displays the WAN connection status of your device.
Status Displays the WAN status is disconnected or connected.
IP Address Displays the IP address of the WAN.
Subnet Mask Displays the Subnet Mask of the WAN.
Gateway IP Displays the address of the gateway.
Primary DNS/Secondary DNS Displays the DNS IP address provided by your ISP.
Connection Uptime Displays the time that the latest WAN connection lasts.
— 35 —

Chapter 4 Status Tab
Auto Refresh If Auto Refresh is checked, parameters in the tab
automatically.
Click Obtain to gain the WAN IP address from DHCP server, and click Release to release the WAN IP
address.
— 36 —

Chapter 5 Network Tab
Chapter 5 Network Tab
On Network Tab, you can configure the parameters of WAN, LAN, Forwarding, Security, Access Control,
Static Routing, Bandwidth control and IP&MAC Binding.
If you’ve made any change of the parameters, please click Apply to make the configuration take effect.
There will be a blue bar at the top of the page to remind you to save the configuration. Click Save
Changes when you finish all settings, otherwise all the settings will be recovered to last saved settings at
reboot or power off.
— 37 —
Chapter 5 Network Tab
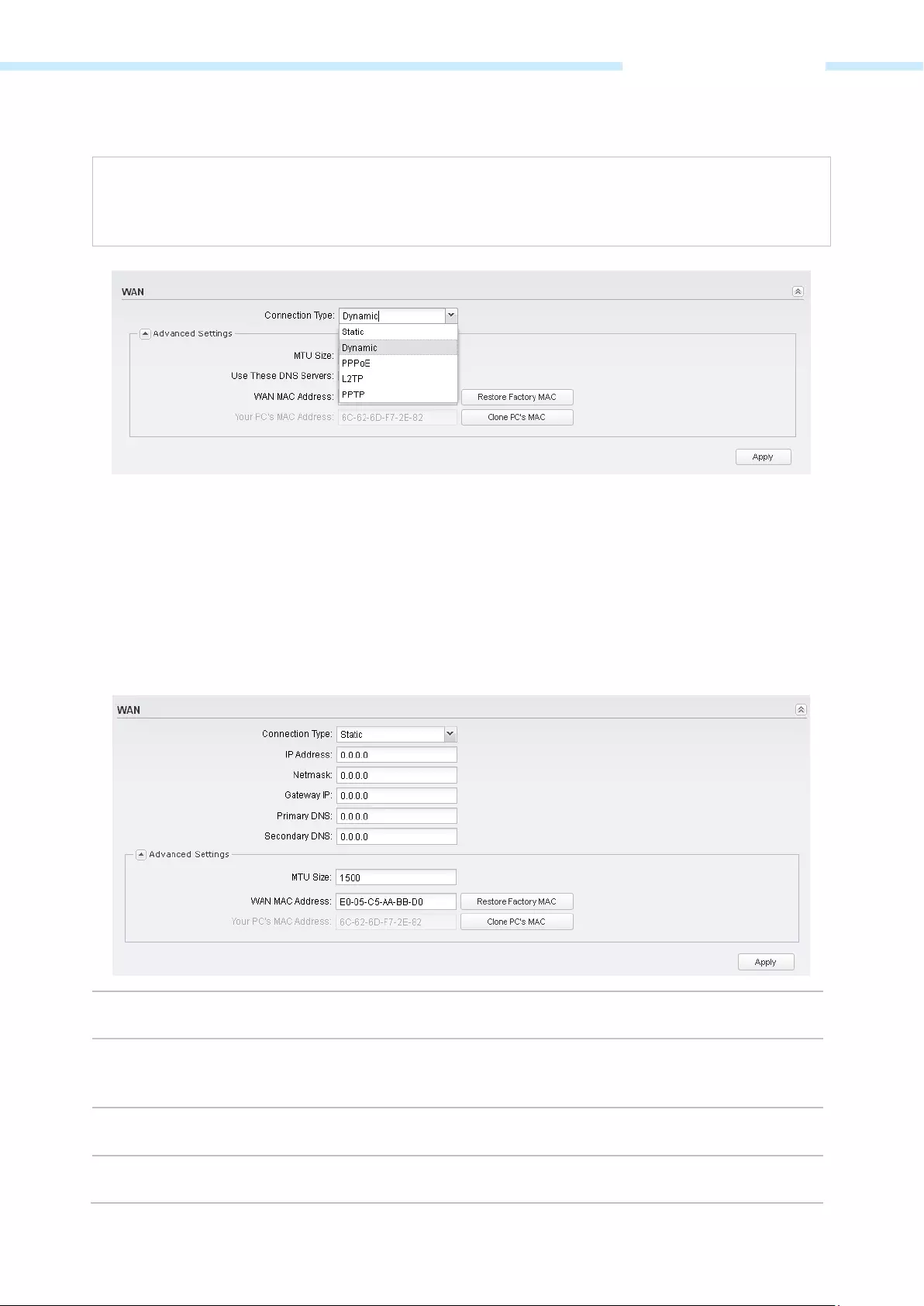
WAN
NOTE:
WAN submenu is only available on AP router mode and AP client router (WISP Client) mode.
There are five WAN connection types: Static, Dynamic, PPPoE, L2TP, and PPTP. Select the suitable one to
configure the IP parameters of the WAN on the screen below. If you are not sure of the connection type to
use, please consult your ISP.
Static
This connection type uses a permanent, fixed (static) IP address that your ISP assigned. In this type, you
should fill in the IP address, Netmask, Gateway IP, and DNS IP address manually, which are specified by
your ISP.
IP Address Enter the IP address provided by your ISP.
Netmask Enter the Netmask provided by your ISP.
Normally use 255.255.255.0 as the
netmask.
Gateway IP Enter the gateway IP address provided by your ISP.
Primary DNS Enter the DNS IP address provided by your ISP.
— 38 —
Chapter 5 Network Tab
Secondary DNS Enter alternative DNS IP address if your ISP provides.
MTU Size
The normal MTU (Maximum Transmission Unit) value for most Ethernet networks
is 1500 Bytes. For some ISPs you need to modify the MTU. But this is rarely
required, and should not be done unless you are sure it is necessary for your ISP
connection.
WAN MAC Address
This field displays the current MAC address of the WAN port. If your ISP requires
that you register the MAC address, please enter the correct MAC address into this
field. The format for the MAC Address is XX—XX—XX—XX-XX-
hexadecimal digit). Click Restore Factory MAC to restore the MAC address of
WAN port to the factory default value.
Your PC’s MAC Address This field displays the MAC address of the PC that is managing the router. Some
ISPs require that you should register the MAC address of your PC. If the MAC
address is required, you can click Clone PC’s MAC to set the WAN MAC address
the same as your management PC’s MAC.
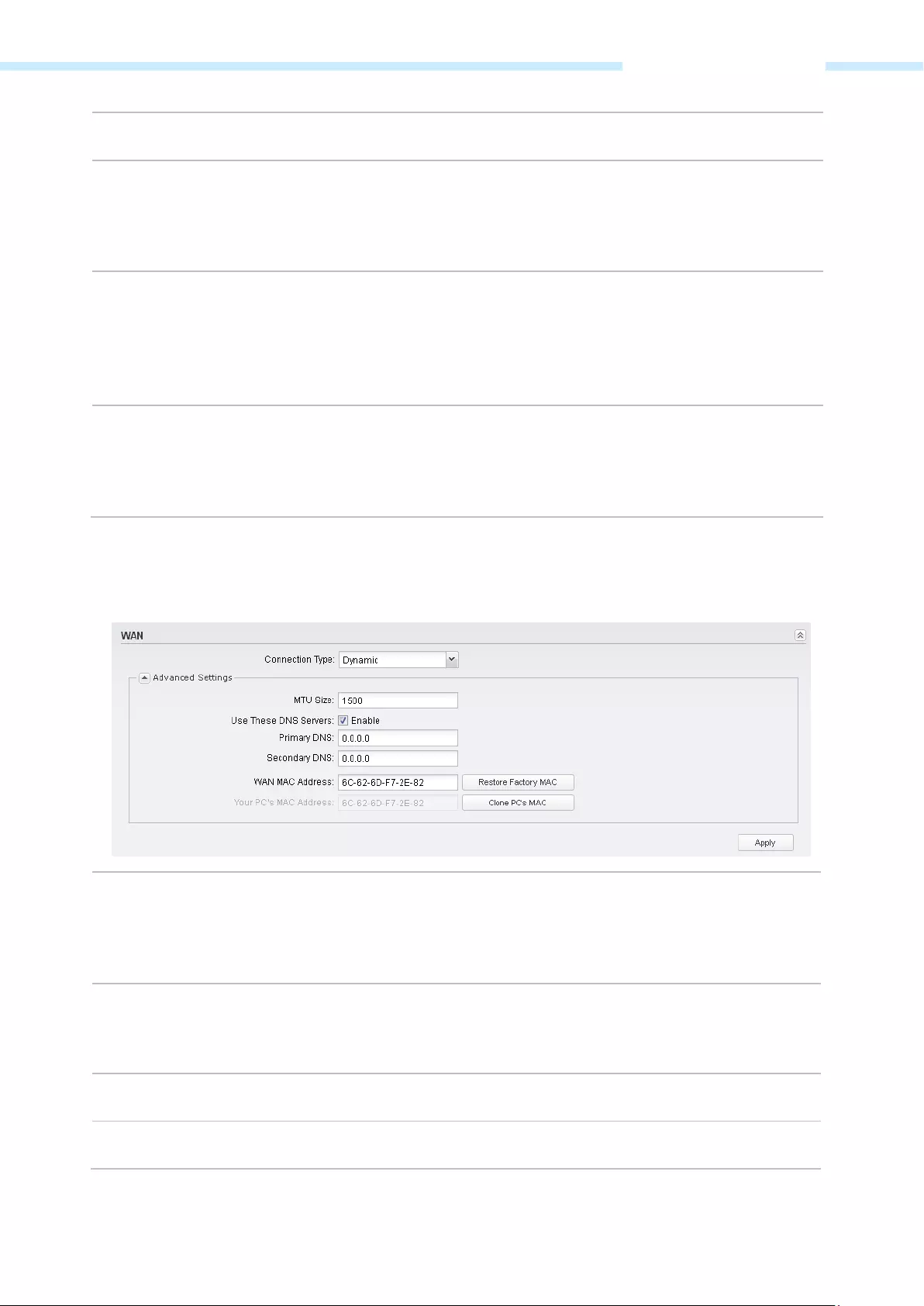
Dynamic
For this connection, Your ISP uses a DHCP server to assign your router an IP address for connecting to the
Internet. You don’t need to configure any parameters.
MTU Size The normal MTU (Maximum Transmission Unit) value for most Ethernet networks
is 1500 Bytes. For some ISPs you need to modify the MTU. But this is rarely
required, and should not be done unless you are sure it is necessary for your ISP
connection.
Use These DNS Servers
If your ISP gives you one or two DNS IP addresses, select Use These DNS Servers
and enter the Primary DNS and Secondary DNS into the correct fields. Otherwise,
the DNS servers will be assigned from ISP dynamically.
Primary DNS Enter the DNS IP address provided by your ISP.
Secondary DNS Enter another DNS IP address provided by your ISP.
— 39 —

Chapter 5 Network Tab
WAN MAC Address This field displays the current MAC address of the WAN port. If your ISP binds the
MAC address of your previous computer/router, please enter the correct MAC
address into this field. The format for the MAC Address is XX—XX—XX—XX—XX—XX (X is
any hexadecimal digit). Click Restore Factory MAC to restore the MAC address of
WAN port to the factory default value.
Your PC’s MAC Address This field displays the MAC address of the PC that is managing the router. Some
ISPs require that you should register the MAC address of your PC. If the MAC
address is required, you can click Clone PC’s MAC to set the WAN MAC address
the same as your management PC’s MAC.
PPPoE
If your ISP delivers Internet through phone line and provides you with username and password, you
should choose this type. Under this condition, you should fill in both User Name and Password that the ISP
supplied, please note that these fields are case—sensitive.
User Name/Password Enter the User Name and Password provided by your ISP. These fields are case—
sensitive.
Connection Mode Please choose the Connection mode.
On Demand —
You can configure the device to disconnect your Internet
connection after a specified period of inactivity (Idle Time). If your Internet
connection has been terminated due to inactivity, Connection on Demand
enables the device to automatically re—establish your connection when you
attempt to access the Internet again. The default Idle Time is 15 minutes. If
your Internet connection is expected to remain active all the time, enter 0 in
— 40 —

Chapter 5 Network Tab
the Idle Time field. Users those pay by time for their Internet access can
choose this mode to save their Internet—access fee.
NOTE: Sometimes the connection cannot be disconnected although you specify
a time to Idle Time (0~99 minutes) because some applications visit the Internet
continually in the background.
Automatic — Connect automatically after the device is disconnected. Users
those are charged a flat monthly fee can choose this mode.
Time—based —
You can configure the device to make it connect or disconnect
based on time. Enter the start time in From (HH:MM) for connecting and end
time in To (HH:MM) for disconnecting. Users those need to control the time
period of Internet access can choose this mode.
Manual —
You can configure the device to make it connect or disconnect
manually. After a specified period of inactivity (Idle Time), the device will
disconnect your Internet connection, and you must click Connect manually to
access the Internet again. If your Internet connection is expected to remain
active all the times, enter 0 in the Idle Time field. Otherwise, enter the desired
Idle Time in minutes you wish to use. Users those pay by time for their
Internet access can choose this mode to save their Internet—access fee.
Secondary Connection If your ISP provides an extra Connection type such as Dynamic/Static IP to
connect to a local area network, you can activate this secondary connection.
Disable —
The Secondary Connection is disabled by default, so there is PPPoE
connection only. This is recommended.
Dynamic IP — Use dynamic IP addres
s to connect to the local area network
provided by ISP.
Static IP —
Use static IP address to connect to the local area network provided
by ISP.
MTU Size
The default MTU (Maximum Transmission Unit) size is 1480 bytes, which is usually
appropriate. For some ISPs, you need modify the MTU. This should not be done
unless your ISP told you to.
Service Name/AC Name Do not change it unless your ISP told you to.
Detect Interval
The default value is 0. You can input the value between 0 and 120. The device will
det
ect Access Concentrator online every interval seconds. If the value is 0, it
means not detecting.
— 41 —

Chapter 5 Network Tab
Use ISP—Specified IP If your service provider give you an IP address along with the user name and
password, Enable «Use ISP—specified IP» and enter the IP ad
provided by your ISP.
Use These DNS Servers If the ISP specifies a DNS server IP address for you, Enable Use These DNS Server,
and fill the Primary DNS and Secondary DNS fields below. Otherwise, the DNS
servers will obtain automatically from ISP.
WAN MAC Address This field displays the current MAC address of the WAN port. If your ISP binds the
MAC address of your previous computer/router,
please enter the correct MAC
address into this field. The format for the MAC Address is XX—XX—XX—XX—XX—XX (X
is any hexadecimal digit). Click Restore Factory MAC to restore the MAC address
of WAN port to the factory default value.
Your PC’s MAC Address This field displays the MAC address of the PC that is managing the router. You can
click Clone PC’s MAC to set the WAN MAC address the same as your
management PC’s MAC.
Click Connect to connect immediately. Click Disconnect to disconnect immediately. You can check and
control the status of WAN connection on Monitor > Dynamic WAN page.
L2TP/PPTP
The configuration steps of these two WAN connections are the same. Take L2TP as an example to
introduce.
Server IP/Name Enter the server IP address or the domain name given by your ISP.
User Name/Password Enter the User Name and Password provided by your ISP. These fields are case—
sensitive.
Connection Mode On Demand —
You can configure the device to disconnect your Internet
connection after a specified period of inactivity (Idle Time). If your Internet
connection has been terminated due to inactivity, Connect on Demand
enables the device to automatically re—establish your connection when you
attempt to access the Internet again. The default Idle Time is 15 minutes. If
— 42 —

Chapter 5 Network Tab
your Internet connection is expected to remain active all the time, enter 0 in
the Idle Time field. Users those pay by time for their Internet access can
choose this mode to save their Internet—access fee.
NOTE:
Sometimes the connection cannot be disconnected although you specify
a time to Idle Time (0~99 minutes) because some applications visit the Internet
continually in the background.
Automatic — Connect automatically after the device is disconnected. Users
those are charged a flat monthly fee can choose this mode.
Manual — You can configure the device to make it
manually. After a specified period of inactivity (Idle Time), the device will
disconnect your Internet connection, and you must click Connect manually
to
access the Internet again. If you want your Internet connection to remain
active all the times, enter 0 in the Idle Time field. Otherwise, enter the desired
Idle Time in minutes you wish to use. Users
those pay by time for their
Internet access can choose this mode to save their Internet—access fee.
Secondary Connection If your ISP provides a Connection type such as Dynamic/Static IP to connect to a
local area network, you can activate this secondary connection.
Dynamic IP —
Use dynamic IP address to connect to the local area network
provided by ISP.
Static IP — Use static IP address to connect to the local area network provided
by ISP.
MTU Size The default MTU (Maximum Transmission Unit) size is 1460 bytes in L2TP and
1420 bytes in PPTP, which is usually fine. For some ISPs, you need modify the
MTU. This should not be done unless you are sure it is necessary for your ISP.
WAN MAC Address This field displays the current MAC address of the WAN port, which is used for
the WAN port. If your ISP requires that you register the MAC address, please enter
the correct MAC address into this field. The format for the MAC Address is XX—XX—
XX—XX—XX—XX (X is any hexadecimal digit). Click Restore Factory MAC to restore
the MAC address of WAN port to the factory default value.
Your PC’s MAC Address This field displays the MAC address of the PC that is managing the router. If the
MAC address is required, you can click Clone PC’s MAC to set the WAN MAC
address the same as your management PC’s MAC.
Click Connect to connect immediately. Click Disconnect to disconnect immediately. You can check and
control the status of WAN connection on Monitor > Dynamic WAN page.
— 43 —
Chapter 5 Network Tab
LAN
The display of this submenu is different in modes. The page of AP router mode and AP client router
(WISP Client) mode is shown as below. In these two modes, static is the only one connection type.
While the page of Access Point mode, Client mode, Repeater (Range extender) mode and Bridge mode
is shown as below. There are two connection types including dynamic and static.
— 44 —

Chapter 5 Network Tab
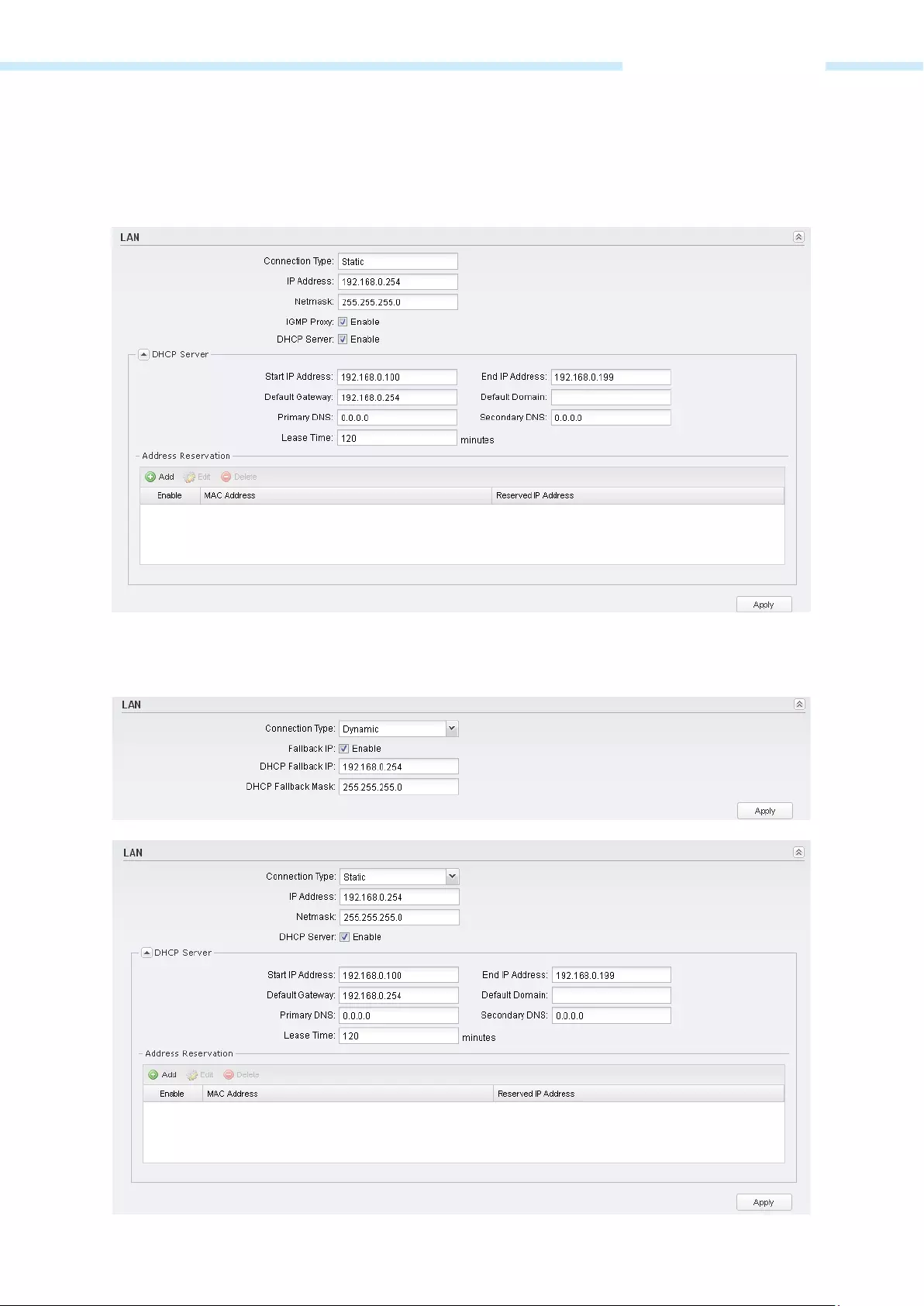
Connection type There is only one LAN Connection type Static in AP Router mode and AP Client
Router (WISP Client) mode. While there are Static and Dynamic of Connection
types in Access Point mode, Client mode, Repeater (Range Extender) mode and
Bridge mode.
IP Address Enter the IP address of your AP/router (factory default: 192.168.0.254).
Netmask Enter the Netmask provided by your ISP.
Normally use 255.255.255.0 as the
netmask.
IGMP Proxy IGMP
(Internet Group Management Protocol) works for IPTV multicast stream. If
you want to watch IPTV, please Enable it.
DHCP Server If the built—in DHCP server is expected to assign IP addresses to clients connected
to the wireless interface and LAN interface, please Enable it.
Fallback IP When Dynamic IP is selected as the connection type, you can enable this function.
The fallback IP will be used as the LAN IP when a DHCP server is not found.
DHCP Fallback IP Specify the IP address for the device to use if a DHCP server is not found.
DHCP Fallback Mask Specify the mask for the device to use if a DHCP server is not found.
Start IP Address
This field specifies the first address in the IP Address pool. 192.168.0.100 is the
default start IP address.
End IP Address
This field specifies the last address in the IP Address pool. 192.168.0.199 is the
default end IP address.
Default Gateway
Enter the IP address of the gateway for your LAN. The factory default setting is
192.168.0.254.
Default Domain Enter the domain name of your DHCP server. You can leave the field blank.
Primary DNS Enter the DNS IP address provided by your ISP. Please consult your ISP if you don’t
know the DNS value. The factory default setting is 0.0.0.0.
Secondary DNS Enter the IP address of alternative DNS server if your ISP provides two DNS servers.
The factory default setting is 0.0.0.0.
Lease Time Enter the amount time of the leased IP address assigned by the DHCP server.
Before the time is up, DHCP client will request to renew the lease automatically
and DHCP server would not assign this IP address to other clients.
— 45 —

Chapter 5 Network Tab
Address Reservation Address Reservation will enable you to specify a reserved IP address for a PC on the
local area network
, so the PC will always obtain the same IP address each time
when it starts up. Reserved IP addresses could be assigned to servers that require
permanent IP settings.
To Reserve IP addresses:
1. Click Add in the table of Address Reservation.
2. Enter the MAC address in the format of XX—XX—XX—XX—XX—XX and the IP
address in dotted—decimal notation of the station you want to add.
3. Click OK after finishing the configuration.
Select the added entries, you can edit or delete them.
Forwarding
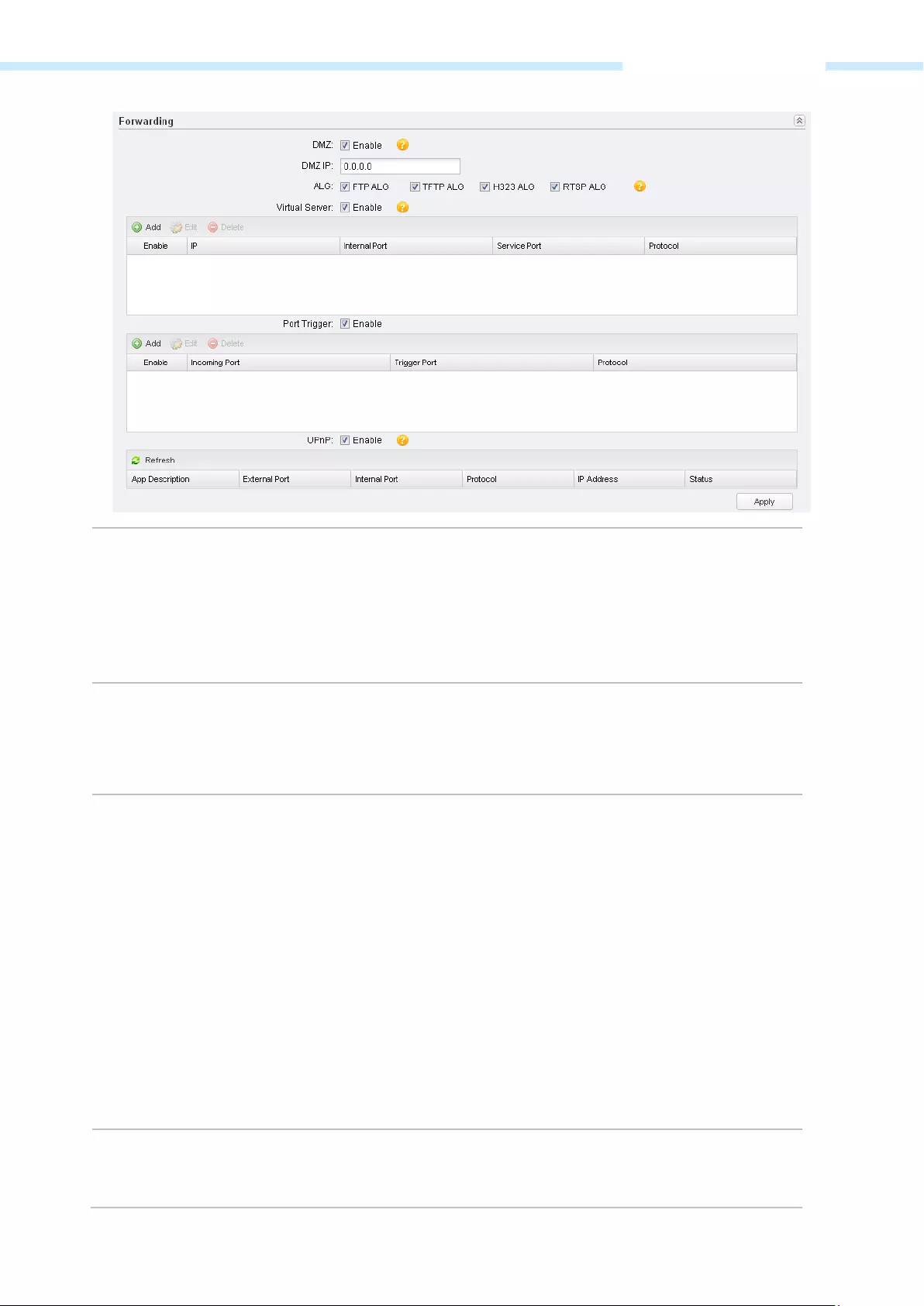
The Forwarding feature is available only in AP Router mode and AP Client Router (WISP Client) mode.
The IP address used on the Internet is public IP address, while IP address used on local area network is
private IP address. The hosts using private IP addresses cannot access the Internet directly and vice versa.
The hosts using private IP addresses visit Internet through NAT (Network Address Translation) technology.
NAT can transfer private IP addresses into public IP addresses to realize the communication from internal
hosts to external hosts.
If the hosts on the Internet want to visit the hosts on local area network, the forwarding function should be
used, including DMZ, Virtual server, Port triggering and UPnP.
— 46 —
Chapter 5 Network Tab
DMZ Check the Enable box to use the DMZ function. DMZ (Demilitarized Zone)
specifically allows one computer/device behind NAT to become
“demilitarized”, so all packets from the external network are forwarded to this
computer/device. The demilitarized host is exposed to the wide area network,
which can realize the unlimited bidirectional communication between internal
hosts and external hosts.
DMZ IP Specify the IP address of the local host network device. The DMZ host device
will be completely exposed to the external network. Any PC that was used for a
DMZ must have a static or reserved IP Address because its IP Address may
change when using the DHCP function.
ALG Common NAT only translates the address of packets at network layer and the
port number at transport layer but cannot deal with the packets with
embedded source/destination information in the application layer. Application
layer gateway (ALG) can deal with protocols with embedded
source/destinati
on information in the application payload. Some protocols
such as FTP, TFTP, H323 and RTSP require ALG (Application Layer Gateway)
support to pass through NAT.
FTP ALG — Allows FTP clients and servers to transfer data across NAT.
TFTP ALG — Allows TFTP clients and servers to transfer data across NAT.
H323 ALG — Allows Microsoft NetMeeting clients to communicate across
NAT.
RTSP ALG — Allows some media player clients to communicate with some
streaming media servers across NAT.
Virtual Server Check the Enable box to use the virtual server function. Virtual servers can be
used for setting up public services on your local area network, such as DNS,
Email and FTP. A virtual server is defined as a service port, and all requests from
— 47 —

Chapter 5 Network Tab
the Internet to this service port will be redirected to the LAN server. Virtual
Server function not only makes the users from I
nternet visit the local area
network, but also keeps network security within the intranet as other services
are still invisible from Internet. The LAN server must have a static or reserved IP
Address because its IP Address may change when using the DHCP function.
To use the virtual server:
1. Click Add in the table of Virtual Server.
2. Enter the IP Address of the PC providing the service application.
3. Enter the Internal Port number of the PC running the service application.
You can leave it blank if the Internal Port is the same as the Service Port, or
enter a specific port number.
4. Enter the numbers of external Service Port. You can type a service port or a
range of service ports (the format is XXX – YYY, XXX is the start port, YYY is
the end port). Internet users send request to the port for services.
5. Choose the one of the protocols used for this application: TCP, UDP, or
TCP/UDP.
6. Click OK after finishing the configuration.
Select the added entries, you can edit or delete them.
Port Trigger Check the Enable box to use the port trigger function. Due to the existence of
the firewall, some applications such as online games, video conferences, VoIPs
and P2P downloads need the device
to configure the forwarding to work
properly, and these applications require multiple ports connection, for single—
port virtual server cannot meet the demand. Port trigger function comes at this
time. When an application initiates a conne
ction to the trigger port, all the
incoming ports will open for subsequent connections.
Once configured, operation is as follows:
1.
A local host makes an outgoing connection to an external host using a
destination port number defined in the Trigger Port field.
2. The router records this connection, opens the incoming port or ports
associated with this entry in the Port Triggering table, and associates them
with the local host.
3. When necessary the external host will be able to connect to the local host
using one of the ports defined in the Incoming Port field.
— 48 —

Chapter 5 Network Tab
To use the port trigger:
1. Click Add in the table of Port Trigger.
2. Enter the Incoming Port for incoming traffic. The port or port range is used
by the remote system when it responds to the outgoing reque
response to one of these ports will be forwarded to the PC that triggered
this rule. You can input at most 5 groups of ports (or port section). Every
group of ports must be set apart with «,». For example, 2000—2038, 2050—
2051, 2085, 3010—3030.
3. Enter the trigger port for outgoing traffic. An outgoing connection using
this port will «Trigger» this rule.
4. Choose the one of the protocols used for this application: TCP, UDP, or
TCP/UDP.
5. Click OK after finishing the configuration.
Select the added entries, you can edit or delete them.
UPnP Check the Enable box to use the UPnP function. If you use applications such as
multiplayer gaming, peer—to—peer connections, or real—time communications
such as instant messaging or remote assistance (a feature in Windows XP), you
should enable the UPnP function. The Universal Plug and Play (UPnP) function
allows the devices, such as Internet computers, to access the local host
resources or devices as needed. Host in the local area network can
automatically open the corres
ponding ports on a router, and make the
application of external host access the resources of the internal host through
the opened ports. Therefore, the functions limited to the NAT can work
properly. Compared to virtual server and port triggering, the application of
UPnP does
n’t need manual settings. It is more convenient for some
applications required unfixed ports.
App Description – Displays the description provided by the application in
the UPnP request.
External Port – Displays the external port number that the router opened
for the service application.
Protocol — Displays which type of protocol is opened.
Internal Port – Displays the internal service port number of the local host
running the service application.
IP Address — Displays the IP address of the local host which initiates the
UPnP request.
Status — Enabled
means that port is still active. Otherwise, the port is
inactive.
— 49 —

Chapter 5 Network Tab
Security
The Security function is available only in AP router mode and AP client router (WISP Client) mode.
Stateful Packet Inspection (SPI) is a firewall that keeps track of the state of network connections (such as
TCP streams, UDP communication) traveling across it. The firewall is programmed to distinguish legitimate
packets for different types of connections. Only packets matching a known active connection will be
allowed to pass through by the firewall and others will be rejected. SPI Firewall is enabled by factory
default.
SPI Firewall Check the Enable box to use the SPI Firewall function. If forwarding rules are
enabled at the same time, the device will give priority to meet forwarding
rules.
Ping WAN Ping Forbidden: The default setting is disabled. If enabled, the
device will not reply the ping request originates from Internet.
LAN Ping Forbidden: The default setting is disabled. If enabled, the device
will not reply the ping request originates from local network.
VPN A VPN is created by establishing a virtual point—to—point connection through
the use of dedicated connections, virtual tunneling protocols, or traffic
encryptions. Through VPN you can access your private network over Internet. A
virtual private network connection across the Internet is similar to a wide area
network (WAN) link between sites. From a user perspective, the extended
network resources are accessed in the same way as resources available within
the private network.
When hosts in the local area network want to visit the
remote virtual private network using virtual tunneling protocols
corresponding VPN protocol should be enabled.
PPTP Passthrough — PPTP (Point—to—Point Tunneling Protocol) allows the
Point—to—Point Protocol (PPP) to be tunneled through an IP (Internet Protocol)
network. Check the box to allow PPTP tunnels to pass through the Device.
L2TP Passthrough — L2TP (Layer Two Tunneling Protocol) is the method
used to enable Point—to—Point connections via the Internet on the Layer
Two level. Check the box to allow L2TP tunnels to pass through the Device.
— 50 —

Chapter 5 Network Tab
IPSec Passthrough —
IPSec (Internet Protocol security) is a suite of
protocols f
or ensuring private, secure communications over IP (Internet
Protocol) networks, through the use of cryptographic security services.
Check the box to allow IPSec tunnels to pass through the Device.
DoS Protection DoS (Denial of Service) Attack is to occupy the network bandwidth maliciously
by the network attackers or the evil programs sending a lot of service requests
to the Host, which incurs an abnormal service or even breakdown of the
network. With DoS Protection function enabled, the device can analyze the
specific fields of the IP packets and distinguish the malicious DoS attack
packets. Upon detecting the packets, the device will discard the illegal packets
directly and limit the transmission rate of the legal packets if the over legal
packets may incur a breakdown of the network. The hosts sending these
packets will be added into the Blocked DoS Host List. The device can defend a
few types of DoS attack such as
ICMP_FLOOD, UDP_FLOOD and
TCP_SYN_FLOOD.
Packets Statistics Interval — Select a value between 5 and 60 seconds from
the drop—
down list. The default value is 10. The value indicates the time
interval of the packets statistics. The result of the statistic is
analysis by ICMP—Flood, UDP Flood and TCP—SYN Flood.
ICMP_FLOOD Attack Filter — Enter a value between 5 and 3600. The
default value is 50. When the current ICMP—FLOOD Packets number is
beyond the set value, the d
evice will start up the blocking function
immediately.
UDP_FLOOD Attack Filter — Enter a value between 5 and 3600. The default
value is 500. When the current UPD—FLOOD Packets number is beyond the
set value, the device will start up the blocking function immediately.
TCP—SYN—FLOOD Attack Filter — Enter a value between 5 and 3600. The
default value is 50. When the current TCP—SYN—FLOOD Packets numbers is
beyond the set value, the Device will start up the blocking function
immediately.
— 51 —

Chapter 5 Network Tab
Blocked DoS Host List Click Blocked DoS Host List to display the blocked DoS host table including
host IP and host MAC. Click Refresh to renewal the table list. Click Clear to
release all the blocked hosts. If you want to release one or some of the blocked
hosts, please select them and Click Unlock.
Access Control
The function of Access Control is available only in AP router mode and AP client router (WISP Client)
mode.
The function can be used to control the Internet activities of hosts in the local area network. For example,
the online time limit and the specified web stations to visit can be controlled by the filtering policy.
Access Control Check the Enable box to use the access control function.
Filtering Policy There are two filtering policies to control the Internet activities:
Allow
the packets specified by any enabled access control policy to pass
through the Device.
The hosts listed below are allowed to access the Internet under the rules. While
others are forbidden to access.
Deny
the packets specified by any enabled access control policy to pass
through the Device.
The hosts listed below are forbidden to access the Internet under the rules.
While others are allowed to access.
— 52 —
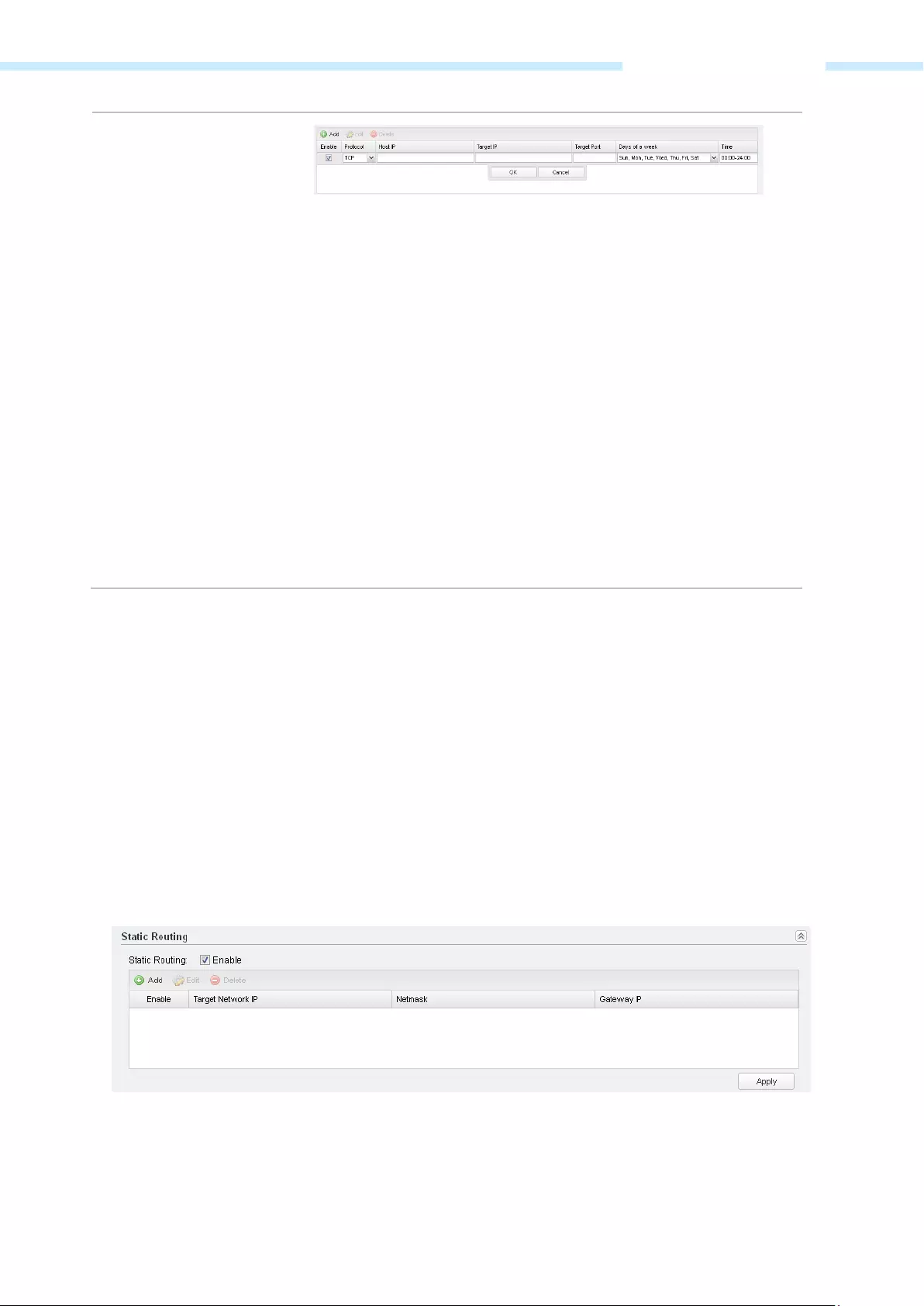
Chapter 5 Network Tab
To use the access control:
1. Click Add in the table to create control rules.
2. Choose one of the protocols from the drop—down list used for the target,
any of IP, TCP, UDP, or ICMP.
3. Enter the IP address or address range of the hosts that you need to control,
for example 192.168.0.12—192.168.0.25.
4. Enter the IP address or address range of the targets that you need to
control, for example 192.168.3.12—192.168.3.25.
5. Specify the port or port range for the target when protocol is TCP or UDP.
6. Select the certain day (days) for the rule.
7. Enter the time rule in HH:MM—HH:MM format, the default value is 00:00—
24:00.
8. Click OK after finishing the configuration.
Select the added entries, you can edit or delete them.
Static Routing
The function of Static Routing is available only in AP router mode and AP client router (WISP Client)
mode.
A static route is a pre—determined path that network information must travel to reach a specific host or
network. If static route is used properly in the network, it can decrease the network overhead and improve
the speed of forwarding packets.
Static routing is generally suitable for simple network environment, in which users clearly understand the
topology of the network so as to set the routing information correctly. When the network topology is
complicated and users are not so familiar with the topology structure, this function should be used with
caution or under the guidance of the experienced administrator.
— 53 —

Chapter 5 Network Tab
Static Routing Check the Enable box to use the static routing function.
To use the static routing:
1. Click Add to create a new static routing.
2. Enter the Target Network IP, the address of the network or host to be
visited. The IP address cannot be on the same network segment with the
device’s WAN or LAN port.
3. Enter the Netmask.
4. Enter the Gateway IP, the address of the gateway that allows for contact
between the Device and the network or host.
5. Click OK after finishing the configuration.
Select the added entries, you can edit or delete them.
Bandwidth Control
The function of Bandwidth Control is available only in AP router mode and AP client router (WISP
Client) mode.
Bandwidth control function is used to control the Internet bandwidth in the local area network. In the case
of insufficient bandwidth resources, enable the function to make the device allocate reasonable
bandwidth to the clients and achieve the purpose of efficient use of the existing bandwidth. Via IP
bandwidth control function, you can set the upper and lower limit in the bandwidth of the computer
network and guarantee a smooth sharing network.
Total Ingress Bandwidth The total download speed limited through the WAN port. The maximum value
of CPE510/CPE520/CPE210/CPE220 is 100,000kbps while
BS510/BS210/OAP210 is 1,000,000kbps.
Total Egress Bandwidth The total upload speed limited through the WAN port. The maximum value of
CPE510/CPE520/CPE210/CPE220 is 100,000kbps while
BS510/BS210/OAP210 is 1,000,000kbps.
— 54 —

Chapter 5 Network Tab
Bandwidth Control Check the Enable box to use the bandwidth control function.
To use the bandwidth control:
1. Click Add in the table of bandwidth control.
2. Enter the IP Range of the target hosts which need
bandwidth, for example 192.168.0.12—192.168.0.25.
3. Enter the Port Range through which the target hosts visit external server,
for example 1—63258.
4. Choose one of the protocols used for this application:
TCP/UDP.
5. Enter the minimum ingress, maximum ingress, minimum egress and
maximum egress of these IP addresses.
6. Click OK after finishing the configuration.
Select the added entries, you can edit or delete them.
IP&MAC Binding
We can effectively prevent ARP attack and IP embezzlement by enabling the IP&MAC binding. Within the
local network, the device transmits IP packets to the certain target identified by the MAC address.
Therefore, the IP and MAC address should be one—to—one correspondence and their corresponding
relations are maintained by the ARP table. ARP attack can use forged information to renewal the ARP table,
and destroy the corresponding relations between IP and MAC addresses, which would prevent the
communication between the device and the corresponding host. When the IP&MAC Binding function is
enabled, the IP and MAC relations in the ARP table won’t be expired and renewed automatically, which
effectively prevents the ARP attack.
Some functions such as access control and bandwidth control, are based on the IP addresses to identify
the access clients. The network administrator can allocate every client a static IP, according to which he
makes the access and bandwidth rules to control the clients’ online behavior and the bandwidth they’ve
used. Some illegal users may change the IP address in order to get higher Internet access. Enabling IP &
MAC binding function can effectively prevent the IP embezzlement.
NOTE:
After IP&MAC binding function is enabled, the IP bound to the MAC
cannot be used by other MACs.
However this MAC can use other IPs within the same segment, which are not bounded by other MACs, to
access the network.
— 55 —

Chapter 5 Network Tab
IP&MAC Binding Check the Enable box to use the IP&MAC binding function.
To use the IP&MAC Binding:
1. Click Add in the table of IP&MAC binding.
2. Enter the IP address and MAC address that you want to bind, for example
192.168.0.12, 00—23—5A—15—99—42.
The new added entry is enabled by
default.
3. Click OK after finishing the configuration.
Select the added entries, you can edit or delete them. Click Import to import
all the entries in Monitor > ARP Table. The imported entries are disabled by
default. You can select the certain entry and click Edit to enable it.
— 56 —

Chapter 6 Wireless Tab
Chapter 6 Wireless Tab
On Wireless Tab, you can configure the related wireless parameters in different modes. Please selectively
read the details according to the working mode of your device.
If you have made any change of the parameters, please click Apply to make the configuration take effect.
There will be a blue bar at the top of the page to remind you to save the configuration. Click Save
Changes when you finish all settings, otherwise all the settings will be recovered to last saved settings at
reboot or power off.
— 57 —

Chapter 6 Wireless Tab
Wireless Basic Settings
This section allows you to configure wireless basic settings, such as region, 802.11 mode, Transmit Power,
and data rates.
Region Select your region from the drop—down list and agree to the Terms of Use in the
pop—up window. Available frequency channels and maximum transmit power
may vary across different countries.
NOTE:
Ensure you select a certain country to comply with local laws. Incorrect
settings may cause interference. Limited to local law of the United States, the
checkbox of region is not selectable.
Mode Select the protocol standard used in the wireless network. With a frequency
band of 2.4GHz, CPE210/CPE220/BS210/OAP210 supports five wireless modes:
802.11b, 802.11g, 802.11n, 802.11b/g and 802.11b/g/n. You are recommended
to set the 11b/g/n mixed mode, and all of 802.11b, 802.11g and 802.11n wireless
stations can connect to the device. CPE510/CPE520/BS510 has a frequency band
of 5GHz, supporting 802.11a, 802.11n and 802.11a/n modes. We suggest to set
in 11a/n mode, allowing both 802.11a and 802.11n wireless stations to access
the device.
Channel Width Select the channel width of this device. Options include 5MHz, 10MHz, 20MHz
and 20/40MHz (this device automatically selects 20MHz or 40MHz, and 20MHz
will be used if 40MHz is not available). Users select corresponding channel
width according to whether their devices support it. According to IEEE 802.11n
standard, using a channel width of 40MHz can increase wireless throughput.
However, users may choose lower bandwidth due to the following reasons:
1. Increase the available number of channels within the
bandwidth.
2. To avoid interference from overlapping channels occupied by other devices
in the environment.
3. Lower bandwidth can concentrate higher transmit power, increasing
stability of wireless links over long distances.
4. Subject to the channel width of root AP in Client/ Bridge/ Repeater/ Client
Router operation modes.
— 58 —

Chapter 6 Wireless Tab
Max TX Rate Set the maximum transmit data rate.
Channel/Frequency S
elect the channel used by this device to improve wireless performance.
1/2412MHz refers to Channel 1 and the frequency is 2412MHz. This setting is
only available in the modes of Access Point and AP Router.
CPE210/CPE220/BS210/OAP210 is a device with a frequency of 2.4GHz and
CPE510/CPE520
/BS510 has a frequency of 5GHz. The channel number varies in
different regions. We highly recommend you use the Spectrum Analysis tool to
select a proper channel.
Antenna Gain Antenna Gain is only available in the page of BS210/BS510/OAP210. Enter the
antenna gain value according to the antennas and the value ranges from 0 to
30dBi.
DFS DFS is only available in devices working in 5GHz including CPE510, CPE520 and
BS510.
Dynamic Frequency Selection (DFS) is used for radar avoidance and is supported
by the novel IEEE 802.11h wireless local area network standard
settings may violate local regulations. It is recommended to enable the function
and choose Auto in the Channel/Frequency.
If the selected channel is DFS
channel, the device will start radar detection and avoid the channel used by
radar. If other channel is selected, there is no need to detect.
Transmit Power You can
use the slider or manually enter the transmit power value. The
maximum transmit power may vary among different countries or regions.
NOTE: In most cases, it is unnecessary to select maximum transmit power.
Selecting larger transmit power than needed may ca
use interference to
neighborhood. Also it consumes more power and will reduce longevity of the
device. Select a certain transmit power is enough
performance. You can use the Speed Test tool to find the best performance.
MAXtream This setting is only available in the modes of Access Point and AP Router.
MAXtream is a proprietary technology of TP—LINK for Wi—Fi system. It is based on
TDMA (Time Division Multiple Access) so that data streams are transmitted in
strict order. MAXtream aims to maximize throughput and minimize latency
especially in a multi—STAs circumstance. «Hidden nodes” problem can also be
eliminated with MAXtream enabled. W
e highly recommend you turn on
MAXtream in a large scale wireless deployment to achieve better performance.
— 59 —
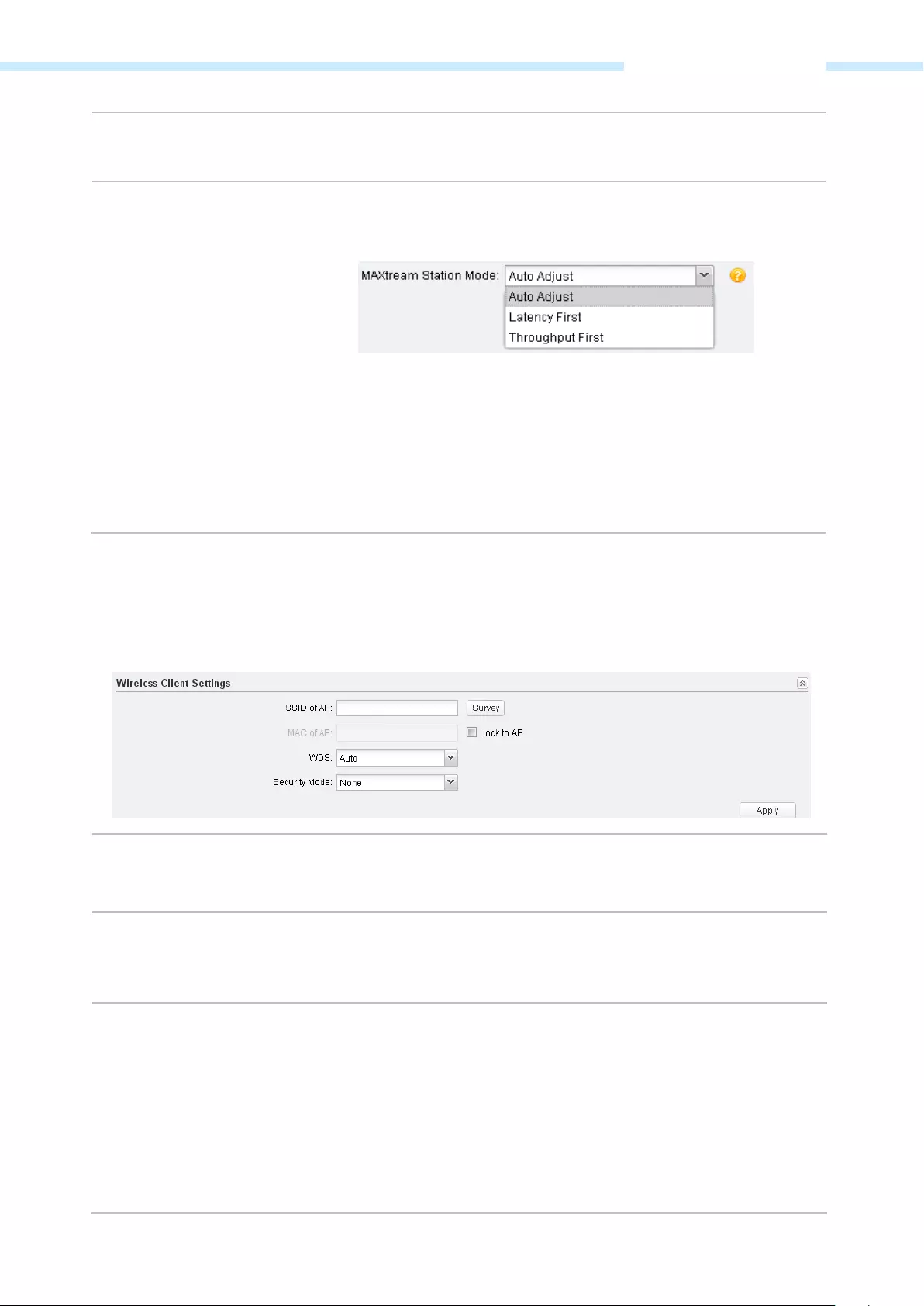
Chapter 6 Wireless Tab
NOTE: MAXtream Technology is only compatible with Pharos series products.
You cannot connect other Wi—Fi devices to an AP with MAXtream enabled.
MAXtream Station Mode This setting is available in Client and Bridge mode and in the AP Client Router
mode when the wireless AP settings is disabled.
For client devices connected to a root AP with MAXtream enabled, you can
choose “Latency First” or “Throughput First” mode to better fit your application.
For example, VoIP
has a high demand for low latency. If you need a good
experience for VoIP, you can select Latency First. Games and downloads ask for
high throughput. You should select Throughput First to guarantee the high
throughput for the games and downloads. Please choose Auto Adjust if you are
not sure or you have no special requirements.
Wireless Client Settings
When this device is configured in the modes of Client, Repeater, Bridge and AP Client Router, the function
of wireless client settings is available.
SSID of AP You can enter the SSID of the specific AP manually to connect to it or directly
survey all the APs around by clicking Survey.
MAC of AP Displays the MAC address of the root AP. It’s possible that two or more networks
use the same SSID in the AP list. Lock to AP can make the device connect to the
specified AP you had connected before the next time.
WDS WDS (Wireless Distribution System) is a communication system among multiple
wireless local area networks established
between APs through wireless
connection. In this system, only data frames with four address fields can be
transparently forwarded at the link layer. In a WDS network, it is necessary that
the root AP supports forwarding of data frames four address fields. If not, only
data frames with the ARP/IP/PPPOE protocol can be forwarded among APs.
Enable – Forward data frames to use four address fields.
Disable – Forward data frames to use three address fields.
— 60 —

Chapter 6 Wireless Tab
Auto – The system automatically detects whether root device supports data
frames with the format of three/four address fields, giving priority to the
format of four address fields. The selection of Auto is recommended.
Security Mode Select the security mode of this device. To access the wireless network of root
AP, the security mode should be set the same as that of root AP.
None — Select this option if the root AP has no encryption. At the moment, it’s
no need to enter a password to access the wireless network of root AP.
WPA—PSK — Select this option if the security mode of the root AP is WPA—PSK.
Enter the parameters including the version and encryption of WPA and PSK
key, which must coincide with those of the root AP.
WEP — Select this option if the security mode of the root AP is WEP. Enter the
parameters including authentication type, key format and WEP key, which
must coincide with those of the root AP.
Wireless AP Settings
Wireless AP settings are only available in the modes of Access Point, Bridge, AP Router, and AP Client
Router.
Wireless Radio Check the wireless radio box to enable this device to
wireless signal.
SSID Enter a character string no more than 32 characters to name
network. The default SSID is TP—
LINK_Outdoor_xxxxxx (xxxxxx is the last six
characters of the MAC address of this device). We suggest you to set an easy—to—
remember SSID to conveniently identify your wireless network.
Enable SSID Broadcast Check this option, AP will broadcast its SSID to hosts in the surrounding
environment, as thus hosts can find the wireless network identified by this SSID.
If SSID Broadcast is not enabled, hosts must enter the AP’s SSID manually to
connect to this AP.
Security Mode Select the security mode of wireless network. If all the hosts are allowed to access
the wireless network, please select None. For the safety of wireless network, you
are suggested to encrypt your wireless network. This device provides three
security modes: WPA (Wi—Fi Protected Access), WPA—PSK (WPA Pre—Shared Key)
and WEP (Wired Equivalent Privacy). WPA—PSK is recommended. Settings vary in
different security modes as the details is in the following introduction.
— 61 —

Chapter 6 Wireless Tab
Security Mode
You can select one of the following security modes:
1. WPA—PSK: Based on pre—shared key. It is characterized by higher safety and simple settings, which
suits for common households and small business. WPA—PSK has two versions: WPA—PSK and WPA2—
PSK.
Version Select one of the following versions:
Auto –Select WPA or WPA2 automatically based on the wireless station’s
capability and request.
WPA –Pre—shared key of WPA.
WPA2 –Pre—shared key of WPA2.
Encryption Select
the Encryption type, including Auto, TKIP, AES. The default setting is
Auto, which can select TKIP (Temporal Key Integrity Protocol) or AES
(Advanced Encryption Standard) automatically based on the wireless station’s
capability and request. AES is more secure than TKIP and TKIP is not supported
in 802.11n mode. We recommend you select AES as the encryption type.
PSK Password Configure the WPA—PSK/WPA2—
PSK password with ASCII or Hexadecimal
characters. For ASCII, the length should be between 8 and 63 characters with
combination of numbers, letters (case—
sensitive) and common punctuations;
for Hexadecimal, the length should be 64 characters (case—insensitive, 0—9, a—f,
A-F).
Group Key Update Period Specify the group key update period in seconds. The value can be either 0 or at
least 30, 0 means no update.
2. WPA: Based on Radius Server, WPA can assign different password for different users and it is much
safer than WPA—PSK. However, its maintenance costs much which is only suitable for enterprise users.
At present, WPA has two versions: WPA and WPA2.
— 62 —

Chapter 6 Wireless Tab
Version Select one of the following versions:
Auto –Select WPA or WPA2 automatically based on the wireless station‘s
capability and request.
WPA –Pre—shared key of WPA.
WPA2 –Pre—shred key of WPA2.
Encryption
Select the Encryption type, including Auto, TKIP, and AES. The default setting is
Auto, which can select TKIP (Temporal Key Integrity Protocol) or AES
(Advanced Encryption Standard) automatically based on the wireless station’s
capability and request. AES is more secure than TKIP and TKIP is not supported
in 802.11n mode. We recommend you select AES as the encryption type.
Radius Server IP Enter the IP address of the Radius Server.
Radius Port Enter the port that radius service uses.
Radius Password Set a password for the Radius Server. The password characters will be shown if
you check the box of show.
Group Key Update Period Specify the group key update period in seconds. The value can be either 0 or at
least 30, 0 means no update.
3. WEP: Based on the IEEE 802.11 standard, this encryption is less safe than the above two modes. The
WEP are not supported in 802.11n mode.
Auth Type Select the Auth type of the WEP security on the drop—down list. The default
setting is Auto, which can select Open System or Shared Key authentication
type automatically based on the wireless station’s capability and request.
Key Format Select Hex or ASCII. Hexadecimal format stands for any combination of
hexadecimal digits (0—9, a—f, A—F) in the specified length. ASCII format stands for
any combination of keyboard characters in the specified length.
Key Selected You can configure four keys in advance and select the present valid key.
— 63 —

Chapter 6 Wireless Tab
WEP Key Enter the WEP keys. The length and valid characters of the key are affected by
key type.
Key Type Select the WEP key length (64—bit, or 128—bit, or 152—bit) for encryption.
Disabled means this WEP key is not used.
64bit —You can enter 10 hexadecimal digits (any combination of 0—9, a—f, A—
F, and null key is not permitted) or 5 ASCII characters.
128bit —You can enter 26 hexadecimal digits (any combination of 0—9, a—f,
A-F, and null key is not permitted) or 13 ASCII characters.
152bit —You can enter 32 hexadecimal digits (any combination of 0—9, a—f,
A-F, and null key is not permitted) or 16 ASCII characters.
Multi—SSID
Multi—SSID is only available in Access Point mode.
This device can build up to four virtual wireless networks for users to access. When the Multi—SSID function
of the device is enabled, its VLAN function is enabled at the same time. It can work together with switches
supporting 802.1 Q VLAN and supports maximum four VLANs. The device adds different VLAN tag to the
clients which connect to the corresponding wireless network. The clients with different VLAN ID cannot
directly communicate with each other.
Clients connected to the device via cable don’t belong to any VLAN. Thus wired client can communicate
with all the wireless clients despite the VLAN settings.
Multi—SSID Check the Enable box to use the Multi—SSID function.
1. Click Add in the table of Multi—SSID.
2. Create a wireless network name (SSID), a string from 1 to 32 characters.
— 64 —

Chapter 6 Wireless Tab
3. Set the VLAN ID of wireless network identified by this SSID, and the value
ranges from 1 to 4094.
4. Select whether to broadcast this SSID or not.
5. Enable AP Isolation, the device would isolate the hosts within the same
wireless network. All the hosts cannot communicate with each other. The
default setting is Disable.
SSID Select the added SSID to configure its security mode.
Security Mode If all the hosts are allowed to access the wireless network, please select None.
For the safety of wireless network, you are suggested to encrypt your wireless
network. This device provides three security modes: WPA—PSK (Pre—Shared Key),
WPA (Wi—Fi Protected Access) and WEP (Wired Equivalent Privacy). WPA—PSK is
recommended. Please refer to Security Mode in the Wireless AP Settings section
for further information.
Wireless MAC Filtering
Wireless MAC Filtering function uses MAC addresses to determine whether one host can access the
wireless network or not. Thereby it can effectively control the user access in the wireless network. This
function is available in all modes except the client mode.
Wireless MAC Filtering Check the Enable box to use wireless MAC filtering function.
1. Click Add in the table of wireless MAC filtering.
2. Select the wireless network (SSID) that you need to filter. In AP mode, if
Multi—SSID is enabled, you should
set different filtering rules for each
SSID.
3. Enter the MAC address of the wireless host that you need to filter.
4. Enter the description information of this filtering rule in the Comment
filed.
— 65 —
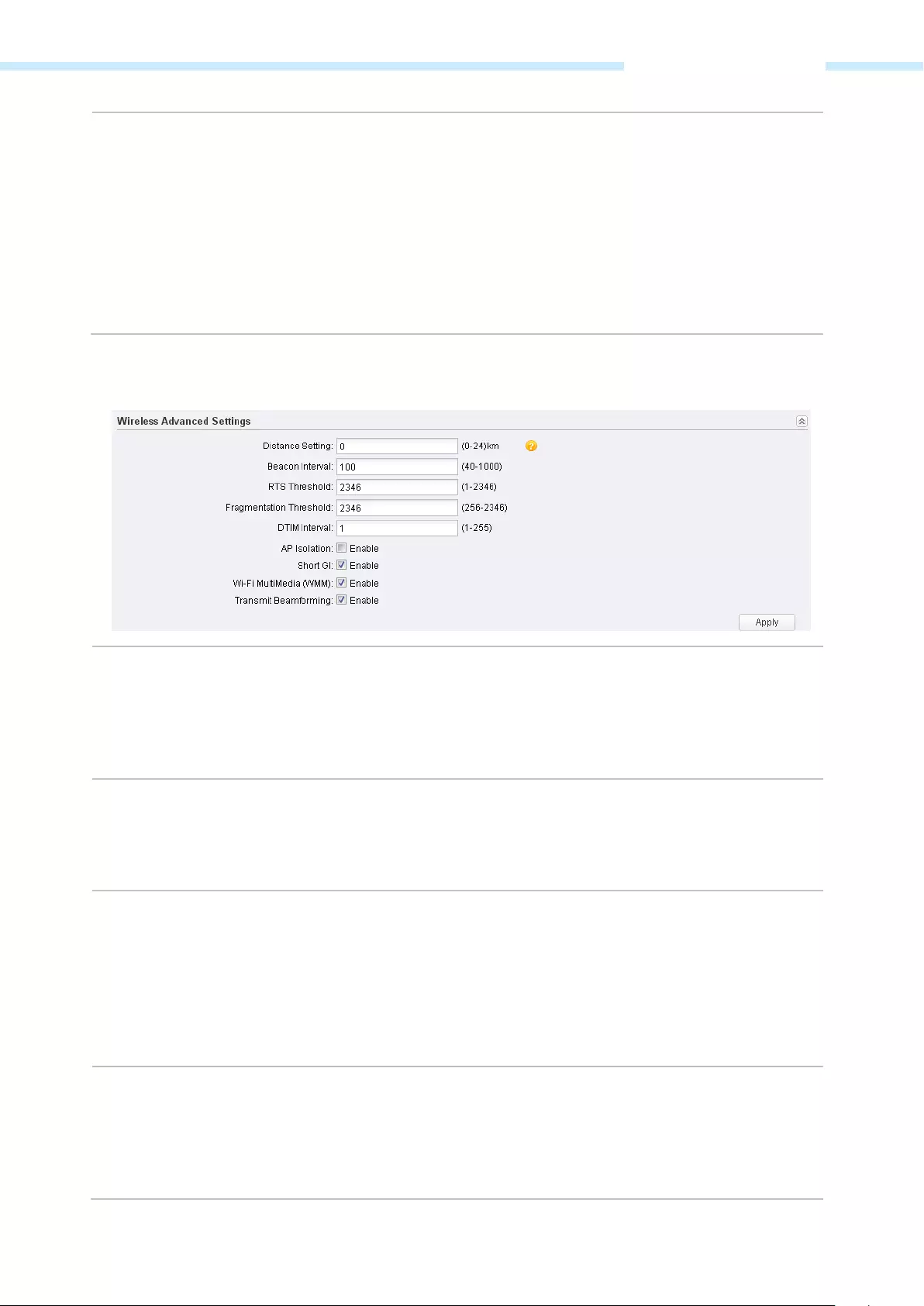
Chapter 6 Wireless Tab
Filtering Rules There are two filtering policies to control the MAC filtering:
Allow the stations specified by any enabled entries in the list to access.
The stations listed below are allowed to access the wireless network under
the rules. While others are forbidden to access.
Deny the stations specified by any enabled entries in the list to access.
The stations listed below are forbidden to access the wireless network under
the rules. While others are allowed to access.
Wireless Advanced Settings
Distance Settings E
nter the distance between AP and Station, which will influence the wireless
performance to a great extent. If this device serves as a client, please enter the
distance between this device and the root AP. If this device configured as an AP,
please enter the distance between the farthest client and this AP. The value is
limited to 0—24km.
Beacon Interval Beacons are transmitted periodically by the device to announce the presence of
a Wireless network for the clients.
Beacon Interval value determines the time
interval of the beacons sent by the device. You can specify a value from 40 to
1,000. The default value is 100.
RTS Threshold When the RTS threshold is activated, all the stations and APs follow the Request
to Send (RTS) protocol. When the station is to send packets, it will send a RTS to
AP to inform the AP that it will send data. After receiving the RTS, the AP notice
other stations in the same wireless network to delay their transmitting of data.
At the same time, the AP inform the requesting station to send data. The value
range is from 0 to 2346 bytes. The default value is 2346, which means that RTS is
disabled.
Fragmentation Threshold Specify
the fragmentation threshold for packets. If the size of the packet is larger
than the fragmentation threshold, the packet will be fragmented into several
packets. Too low fragmentation threshold may result
performance caused by the excessive packets. The recommended and default
value is 2346 bytes.
— 66 —

Chapter 6 Wireless Tab
DTIM Interval This value indicates
the number of beacon intervals between successive
Delivery Traffic Indication Messages (DTIMs) and this number is included in each
Beacon frame. A DTIM is contained in Beacon frames to indicate whether the
access point has buffered broadcast and/or multicast data for the client devices.
Following a Beacon frame containing a DTIM, the access point will release the
buffered broadcast and/or multicast data, if any exists. You can specify the value
between 1—255 Beacon Intervals. The default value is 1, indicating the DTIM
Interval is the same as Beacon Interval. An excessive DTIM interval may reduce
the performance of multicast applications.
We recommend you keep it by
default.
AP Isolation Enable AP Isolation to isolate all wireless stations connected to this device so
that they cannot communicate with each other. This function will be disabled if
WDS/Bridge is enabled.
Short GI Short GI is used to increase the throughput by reducing the guard interval time.
We recommend you enable this function.
Wi—Fi MultiMedia (WMM) After WMM is enabled, this device has the QoS function to
transmission of audio and video packets with high priority.
Transmit Beamforming Transmit Beamforming is a signal processing technique used in sensor arrays for
directional signal transmission. The beamformer controls precise adjustments of
each signal phase and amplitude to make the multi—path signals superpose
better to become one single strengthened signal at the recipient end so as to
effectively improve the signal quality, especially on long distance transmission.
— 67 —

Chapter 7 Management Tab
Chapter 7 Management Tab
On Management Tab, you can configure system management services: System Log, Miscellaneous, Ping
Watch Dog, and Dynamic Domain Name System (DDNS). Web server, Simple Network Management
Protocol (SNMP), SSH server, RSSI LED Thresholds are also available.
— 68 —

Chapter 7 Management Tab
If you have made any change of the parameters, please click Apply to make the configuration take effect.
There will be a blue bar at the top of the page to remind you to save the configuration. Click Save
Changes when you finish all settings, otherwise all the settings will be recovered to last saved settings at
reboot or power off.
System Log
System logs record the events and activities while the router is running. If a failure happens on the router,
System logs can help to diagnose the issue.
Open System Log Check system log by clicking Open and then appears the following popup page.
This page displays detailed system logs that can be sorte
ascending or descending order. Columns can be chosen from Time, Type, Level,
and Message.
Download to PC Enables users to download system logs to PC.
— 69 —

Chapter 7 Management Tab
Auto Mail Setting Enables users to mail system logs automatically. Click Setting and the following
page appears.
Set the receiving and sending mailbox address, server address, validation
information as well as the timetable for Auto Mail Feature.
From – Enter sender’s mail box address.
To – Enter the recipient’s address.
SMTP Server – Enter sender’s SMTP server.
Authentication — Most SMTP Server requires Authentication.
User Name – Sender’s mail account name.
Password – Sender’s mail account password.
Confirm Password –Re—enter your mail account password.
Check Auto Mail Feature box, you can set the device how and when to send
the log to the specified mailbox.
Miscellaneous
Discovery Enable the function to let TP—LINK Pharos Control software discover the device.
With its main function to centralize monitoring and managing network devices
in the network platform, Pharos Control is network management software
developed independently by TP—LINK and it currently supports Pharos series
products.
— 70 —

Chapter 7 Management Tab
PoE Passthrough When enabled, the device allows Power over Ethernet (PoE) power to pass from
LAN0 port to LAN1 port. Enable it if you want to supply power to other passive
PoE device by LAN1.
Ping Watch Dog
Ping Watch Dog sets the device to continuously ping a user—defined IP address (it can be the Internet
gateway, for example) to check the network connectivity. If there is a connection failure then the device
will automatically reboot.
Ping Watch Dog is dedicated to continuously monitoring the connectivity to a specific host using the Ping
tool. The Ping tool sends ICMP echo request packets to the target host and listens for ICMP echo response.
If the defined number of replies is not received, the tool reboots the device.
Ping Watch Dog Check the Enable box to use the function of Ping Watch Dog.
IP Address To Ping Specify the IP address of the target host to which the Ping Watch Dog Utility will
send ping packets.
Ping Interval Enter the time interval (in seconds) between two successive ping packets. The
default value is 300 seconds.
Startup Delay Enter the initial time delay (in seconds) from device startup to the first ICMP echo
requests sent by Ping Watch Dog. The default value is 300 seconds.
The Startup Delay value should be at least 60 seconds as the device’s initialization
takes a considerable amount of time.
Failure Count To Reboot Enter the fail count of ICMP echo request. If the device sends the specified count
of ICMP echo requests to the host and none of the corresponding ICMP echo
response packets is received, Ping Watch Dog will reboot the device. The default
value is 3.
— 71 —
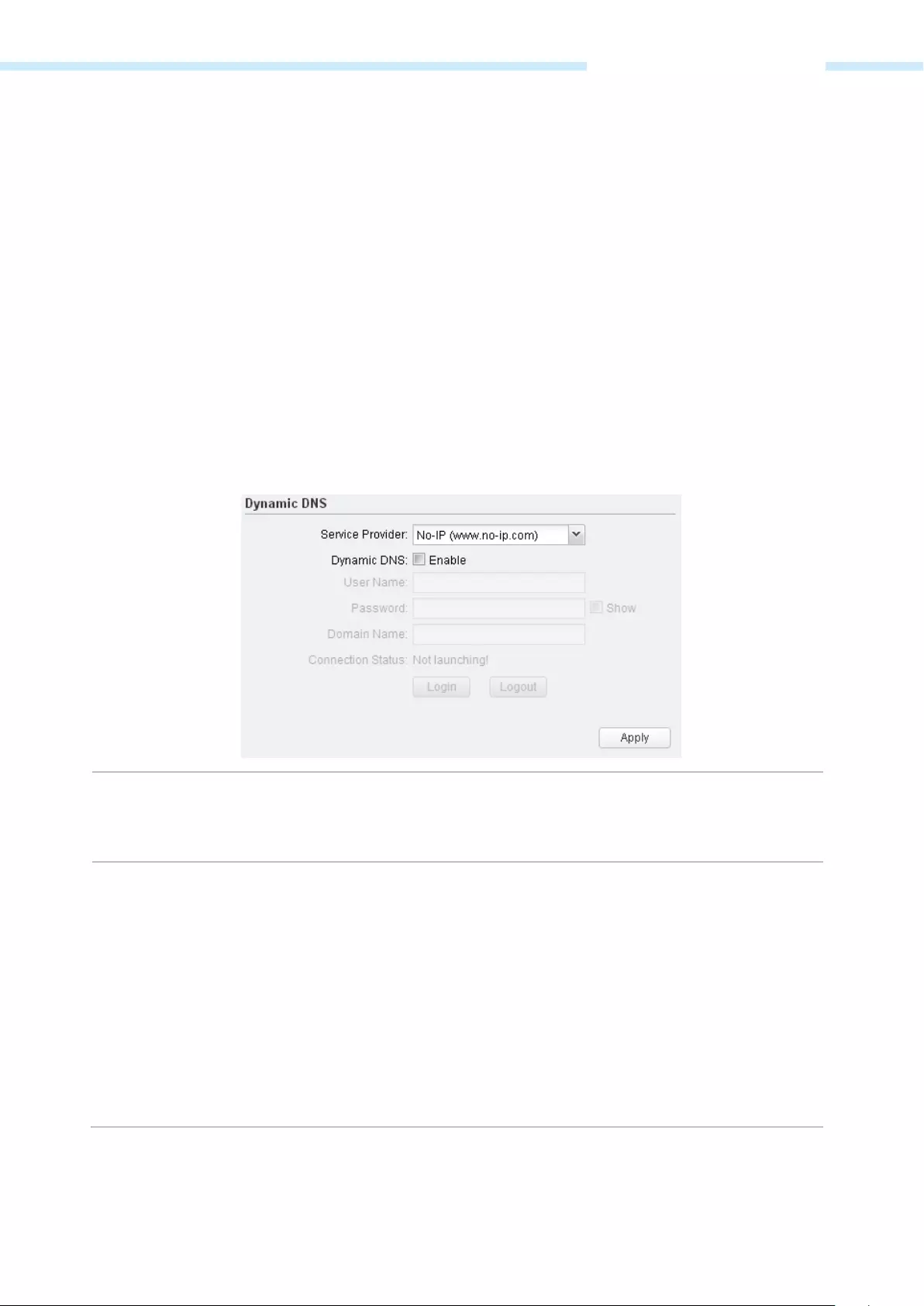
Chapter 7 Management Tab
Dynamic DNS
The main function of Dynamic DNS (DDNS) is mapping the fixed domain name to dynamic IP address.
When a device connects to the Internet through PPPoE or Dynamic IP, the WAN IP address it gets is not
fixed, which is inconvenient for the Internet users to access the servers in the local area network through IP
address. Dynamic DNS function allows users to access servers using a fixed domain name.
The DDNS server will establish a mapping table about the dynamic IP address and the fixed domain name.
When the WAN IP address of the device changes, it will make an update request to the specified DDNS
server, and then the DDNS server will update the mapping relation between the IP address and the
domain name. Therefore, whenever the WAN IP address changes, users on the Internet can still access the
servers in the local area network using a fixed, easy—to—remember domain name.
The DDNS function that serves as the client of DDNS service must work with DDNS server. Please register
an account to DDNS service provider (NO—IP, Dyndns or Comexe) before using this function.
Service Provider Select your DDNS service provider from the available DDNS service providers
including NO—IP (www.no—ip.com), Dyndns (www.dyndns.com) and Comexe
(www.comexe.net).
Dynamic DNS Check the Enable box to use the function.
User Name — Enter the user name of the DDNS account.
Password — Enter the password of the DDNS account.
Show — Check the box to display the password characters.
Domain Name —Enter a customized domain name. Even if your IP is
dynamic, other users on the Internet can still access your server via this
fixed domain name after enabling the DDNS function.
Connection Status —Displays the connection status between this device
and the DDNS server.
— 72 —

Chapter 7 Management Tab
Web Server
The Web Server function enables users to log in to the web management page to manage this device
remotely over the Internet.
Secure Connection (HTTPS) The Secure Connection (HTTPS) mode is enabled by default.
Secure Server Port Specify the server port that the Web server uses in the S
(HTTPS) mode, and the default is 443.
Server Port Specify the server port that the Web server uses in the HTTP mode, and the
default is 80.
Remote Login IP Address Configure the IP address that can remotely visit the web management page of
this device. Enter 0.0.0.0 to forbid any remote IP’s login. Enter 255.255.255.255 to
allow all the remote IP to visit.
Session Timeout Enter the maximum timeout before the session expires. Once a session expires,
you must log in again using the username and password.
MAC Authentication Enable this function to allow PCs with specific MAC addresses to access the web
management page. And then enter each MAC address in the MAC field. The
format for the MAC addresses is XX—XX—XX—XX—XX—XX. Only the PCs with the MAC
addresses listed can use the password to access the device’s web management
page and the others will be blocked. By default, the function is not enabled. All
the PCs in the local area network are allowed to access the devic
management page.
Click Add PC’s MAC, your PC’s MAC address will be added in the list above. Click
Apply to save your settings.
— 73 —
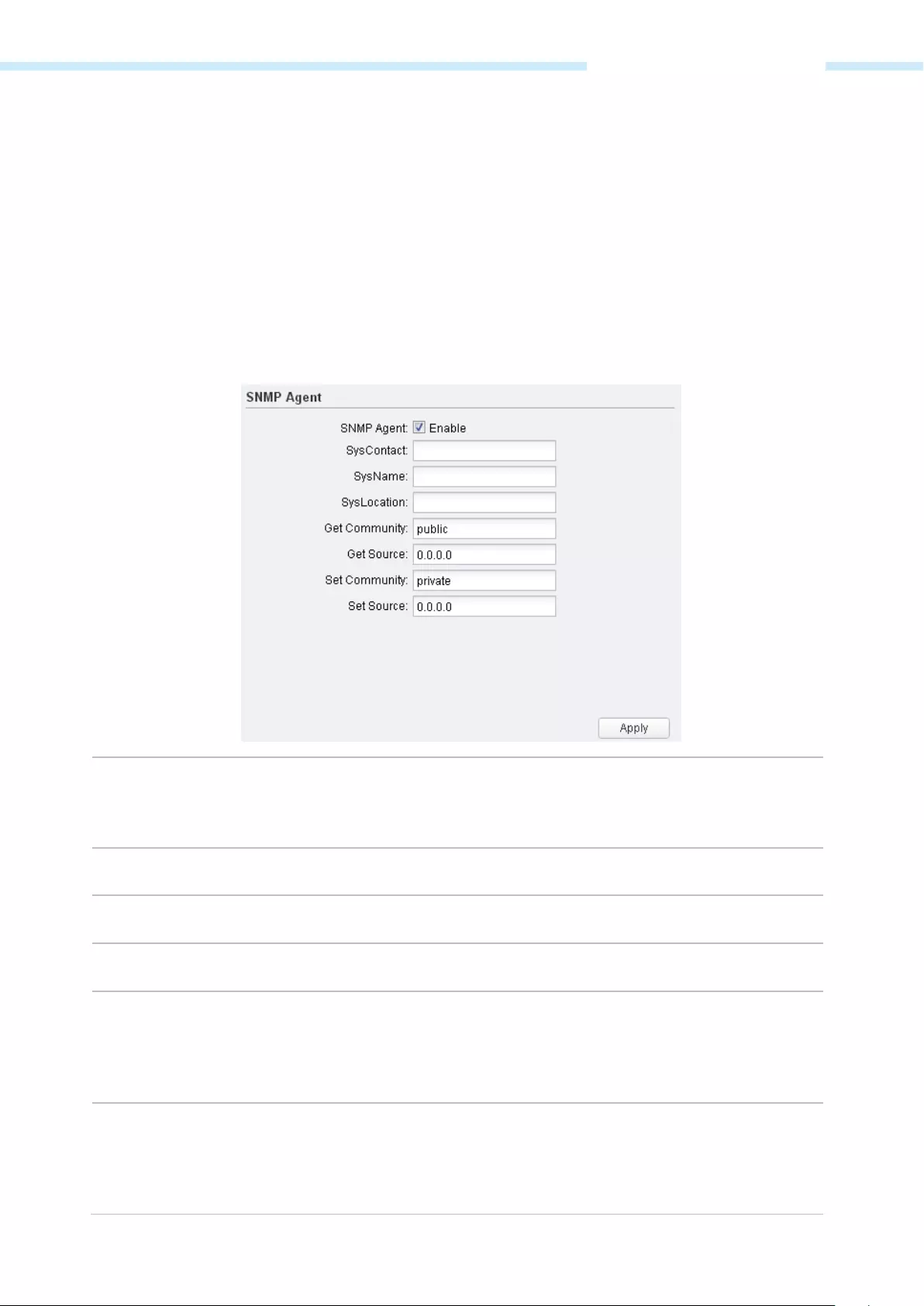
Chapter 7 Management Tab
SNMP Agent
You can get the traffic information and transmit condition by using the SNMP Agent function.
Simple Network Management Protocol (SNMP) is an application layer protocol that facilitates the
exchange of management information between network devices. Main functions of SNMP include
monitoring network performance, detecting and analyzing network error, configuring network devices,
and so on. Under the circumstance of network working normally, SNMP can play a part in statistics,
configuration and testing. When networks have troubles, SNMP can detect and restore these troubles.
Configuring this device as SNMP Agent, it can receive and process the management message from the
network management system.
SNMP Agent Enable
the SNMP Agent function and the SNMP Agent will gather the
information of this device and respond to information requests from one or
more management systems.
SysContact Enter the information of the contact person for this managed node.
SysName Enter an administratively—assigned name for this managed node.
SysLocation Enter the physical location of this managed node.
Get Community Community refers to a host group aiming at network management. Get
Community only has the read—only right of the device’s SNMP information. The
get community name can be considered as a password used to restrict the
access right of SMNP managers. The default name is public.
Get Source Defines the IP address (for example, 10.10.10.1) or subnet (
10.10.10.0/24) for management systems that can serve as Get Community to read
the SNMP information of this device. The default is 0.0.0.0, which means all hosts
can read the SNMP information of this device.
— 74 —

Chapter 7 Management Tab
Set Community Set Community has the read and write right of the device’s SNMP information.
Enter the community name that allows read/write access to the device’s SNMP
information. The community name can be considered as a password to restrict
the access right of SNMP managers. The default name is private.
Set Source Defines the IP address (for example, 10.10.10.1) or subnet (
10.10.10.0/24) for management systems that can serve as Set Community to
read and write the SNMP information of this device. T
which means all hosts can read and write the SNMP information of this device.
NOTE:
Defining community can allow management systems in the same community to communicate with the
SNMP Agent. The community name can be seen as the shared password of the network hosts group. Thus,
for the safety, we suggest modifying the default community name before enabling the SNMP Agent
service. If the field of community is blank, the SNMP Agent will not respond to any community name.
SSH Server
The SSH Server function allows users to log in and manage the device through SSH connection on the SSH
client software.
SSH (Secure Shell) is a security protocol established on application and transport layers. SSH—encrypted—
connection is similar to a telnet connection, but essentially the old telnet remote management method is
not safe, because the password and data transmitted with plain—text can be easily intercepted. SSH can
provide information security and powerful authentication when you log in this device remotely through
an insecure network environment. It can encrypt all the transmission data and prevent the information in
remote management from being leaked.
Server Port Enter the TCP/IP port of the SSH Server. The default port is 22.
SSH Login Enable the SSH Server function.
Remote Management Enable the function to let TP—LINK Pharos Control software manage the device
remotely.
— 75 —
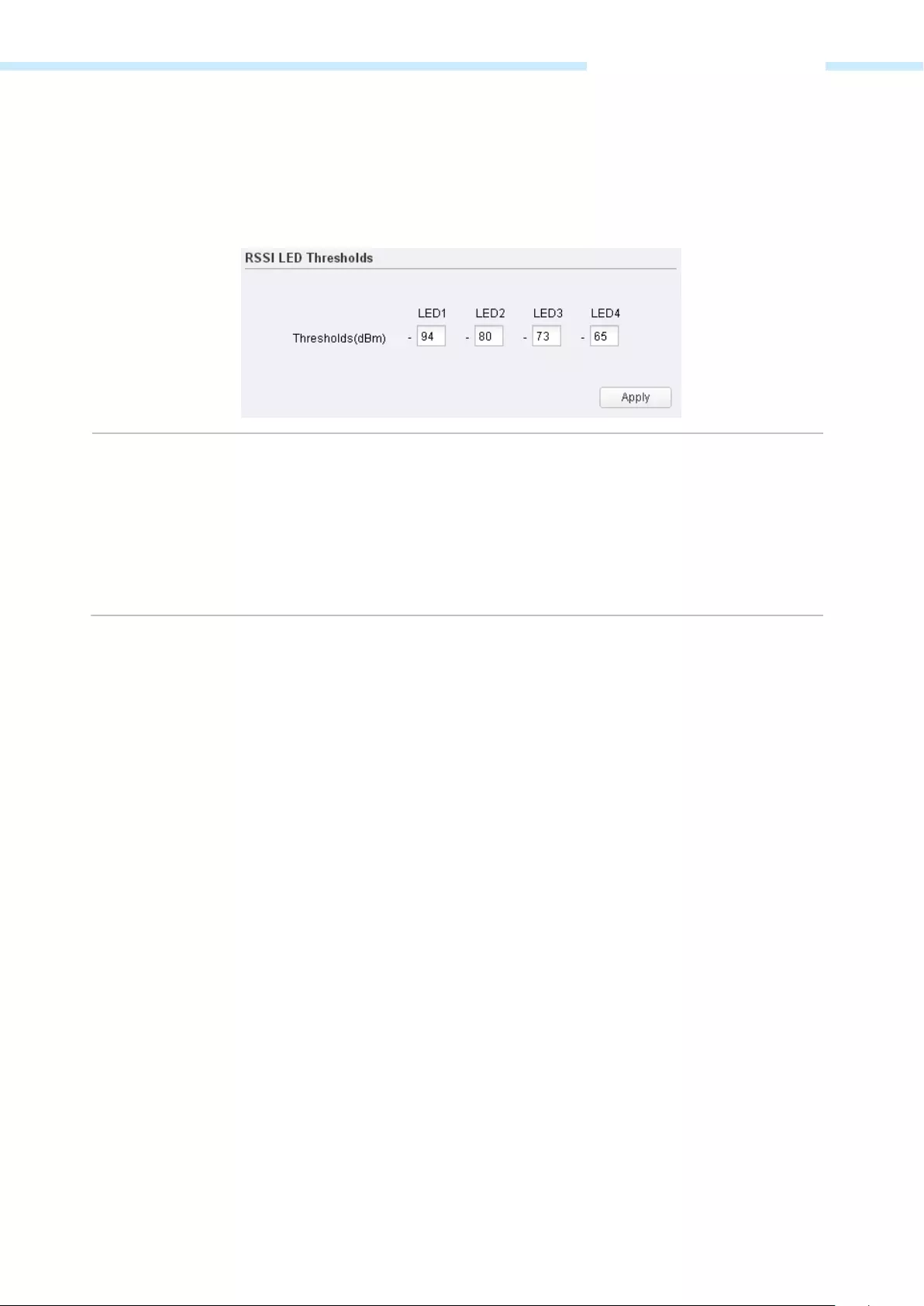
Chapter 7 Management Tab
RSSI LED Thresholds
You can configure the LEDs on the device to light up when received signal levels reach the values defined
in the following fields. This allows a technician to easily deploy a Pharos series product without logging
into the device (for example, for antenna alignment operation).
Thresholds (dBm) The specified LED
will light up if the signal strength reaches the values in the
field. For example, if the signal strength fluctuates around —63 dBm, then the
LED threshold values can be set to the following: —70, —65, —62, and —60. The
default values are set according to
the verified optimum values. We
recommend you keep it by default.
The default LED threshold values may vary among different product models in
terms of radio features. The figure above shows the default values of CPE210.
— 76 —
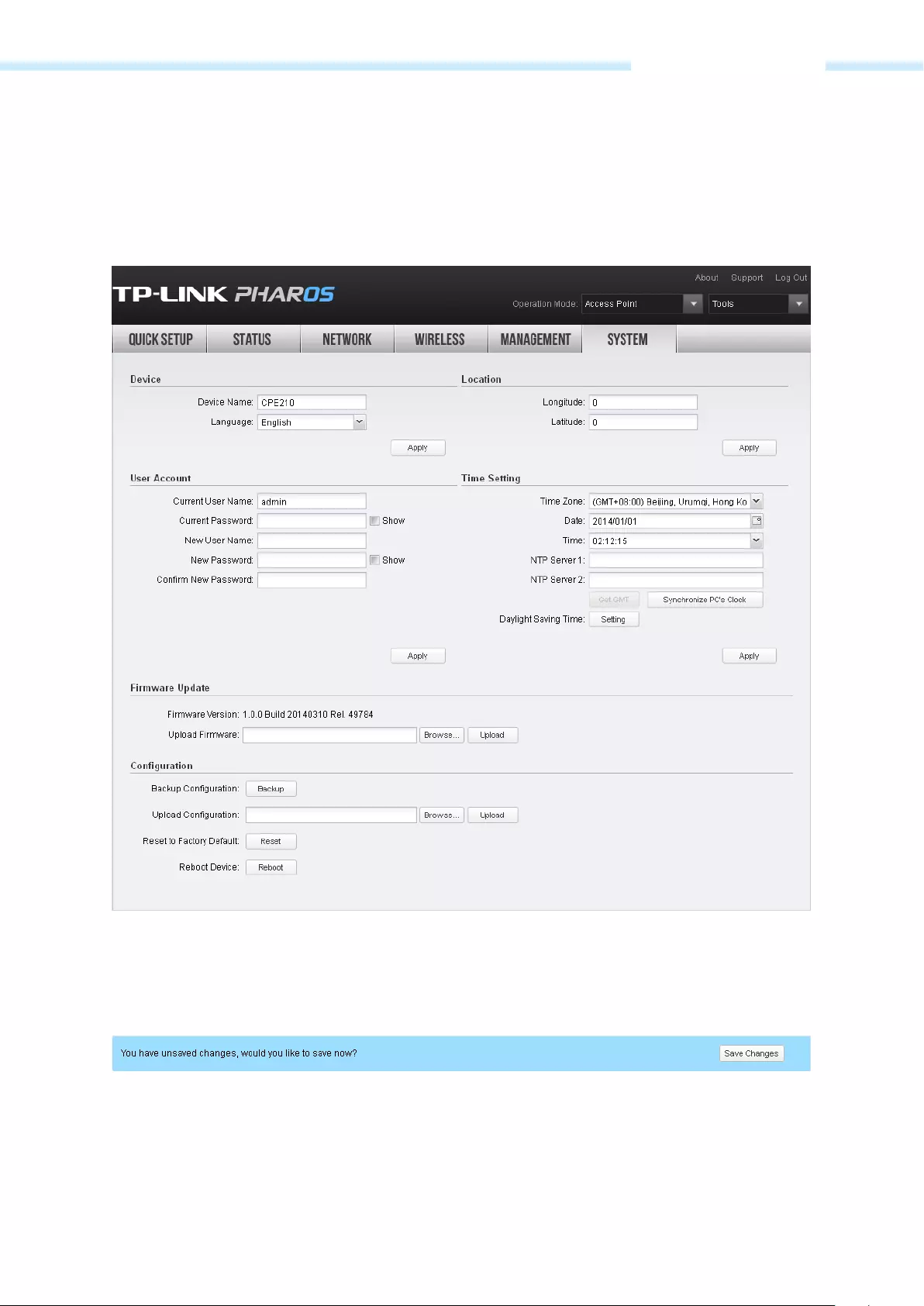
Chapter 8 System Tab
Chapter 8 System Tab
The System Tab controls system maintenance routines, device customization, location management, user
account management, firmware update, time setting and configuration backup.
If you have made any change of the parameters, please click Apply to make the configuration take effect.
There will be a blue bar at the top of the page to remind you to save the configuration. Click Save
Changes when you finish all settings, otherwise all the settings will be recovered to last saved settings at
reboot or power off.
— 77 —
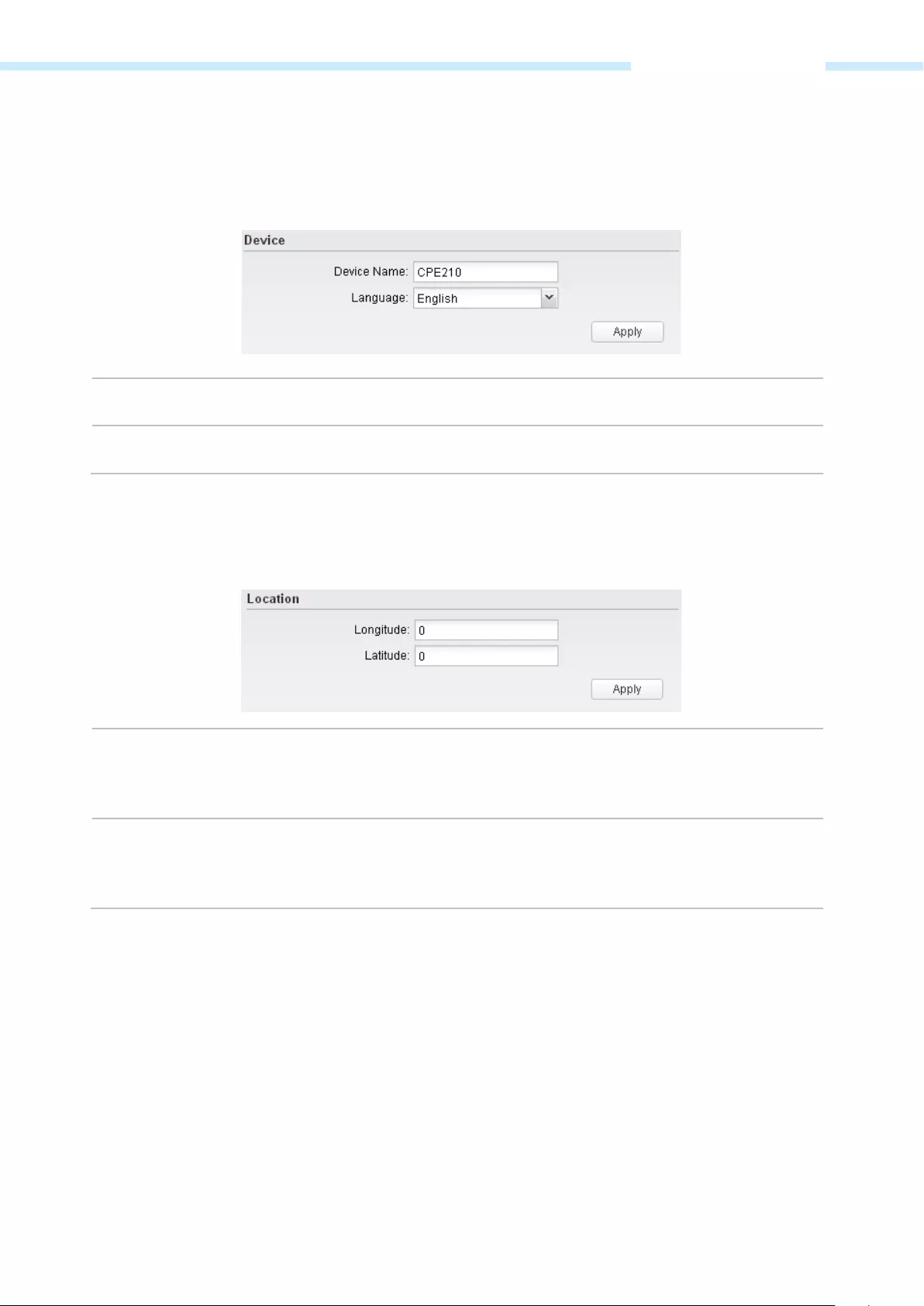
Chapter 8 System Tab
Device
The Device Name is the model of device by default. You can customize a new personal and easy—to—
remember name.
Device Name Customize the name of the device.
Language Displays the default language in the web management page is English.
Location
Longitude and latitude define the device’s coordinates.
Longitude Enter the longitude of the device’s location in decimal degree. The positive
number indicates the east longitude while the negative number indicates the
west longitude.
Latitude Enter the latitude of the device’s location in decimal degree. The positive
number indicates the north lat
itude while the negative number indicates the
south latitude.
User Account
You can change the user password to protect your device from unauthorized login. We recommend that
you change the default user password on the very first system setup.
— 78 —
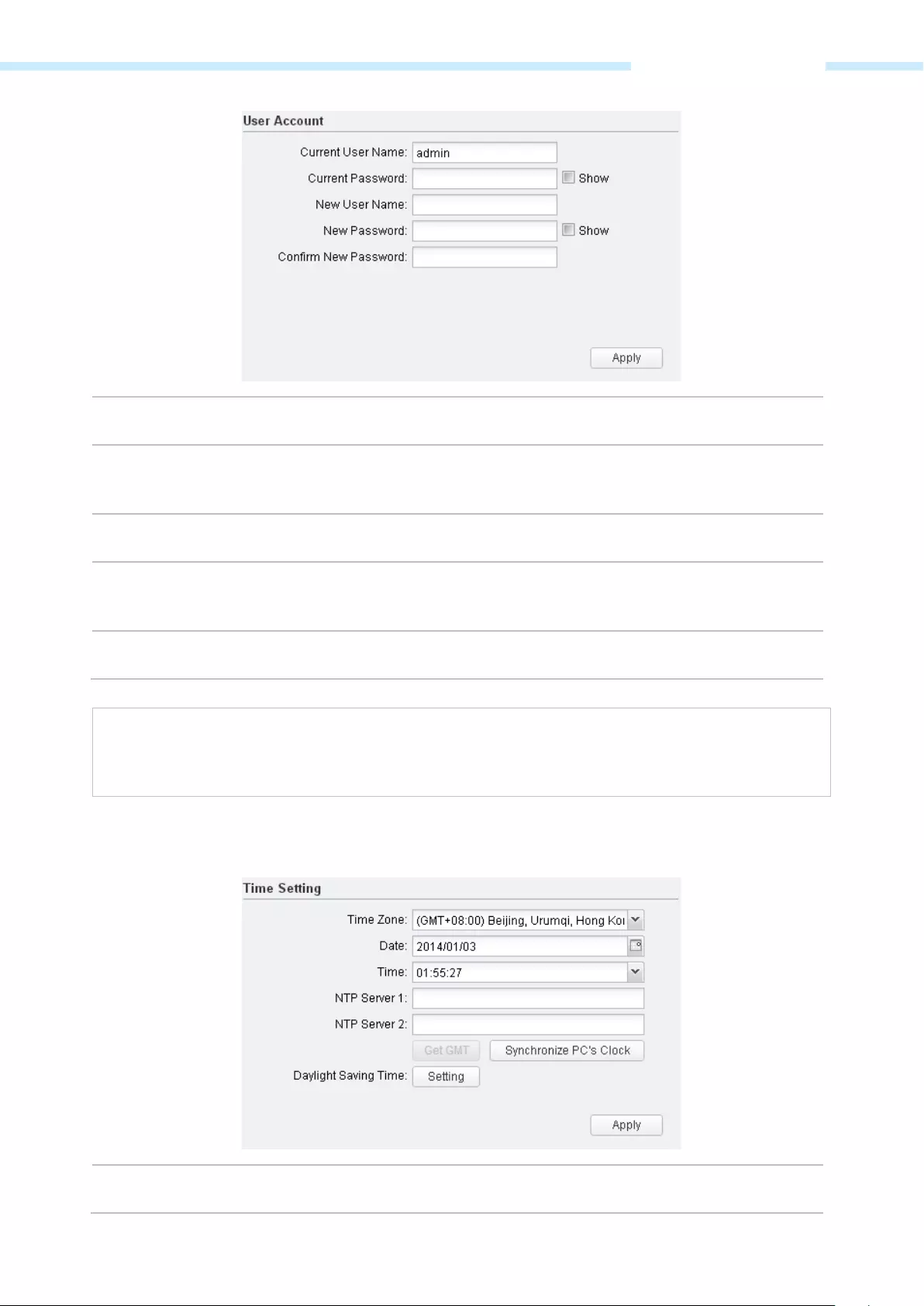
Chapter 8 System Tab
Current User Name Displays the current user name.
Current Password Enter the current password for the user account. Check the Show box to
display what you’ve entered.
New User Name Enter the new user name for the user account.
New Password Enter the new password for the user account. Check the Show box to display
what you’ve entered.
Confirm New Password Re—enter the new password for the user account.
NOTE:
The password is a string from 1 to15 alphanumeric characters or symbols.
Time Setting
Time Zone Select your local time zone from the drop—down list.
— 79 —

Chapter 8 System Tab
Date Specify the device’
s date. Click the calendar icon or manually enter the date in
the following format: YYYY/MM/DD. For e
xample, for November 25, 2013,
enter 2013/11/25 in the field.
Time Specify the device’s date. Select the time from the drop—down list or manually
enter the date in HH:MM:SS format.
NTP Server 1 Enter the primary NTP Sever address.
NTP Server 2 Enter an alternative NTP Server address.
Get GMT Click Get GMT to get GMT from the NTP server.
Synchronize PC’s Clock Date and time of the device can be synced with your PC’s system time.
Daylight Saving Time Click Setting to set the daylight saving time on the following page.
Daylight Saving Time
DST Status Check the Enable box to use the function.
Predefined Mode Select a predefined DST configuration.
USA: Second Sunday in March, 02:00 ~ First Sunday in November, 02:00.
European: Last Sunday in March, 01:00 ~ Last Sunday in October, 01:00.
Australia: First Sunday in October, 02:00 ~ First Sunday in April, 03:00.
New Zealand: Last Sunday in September, 02:00 ~ First Sunday in April, 03:00.
— 80 —
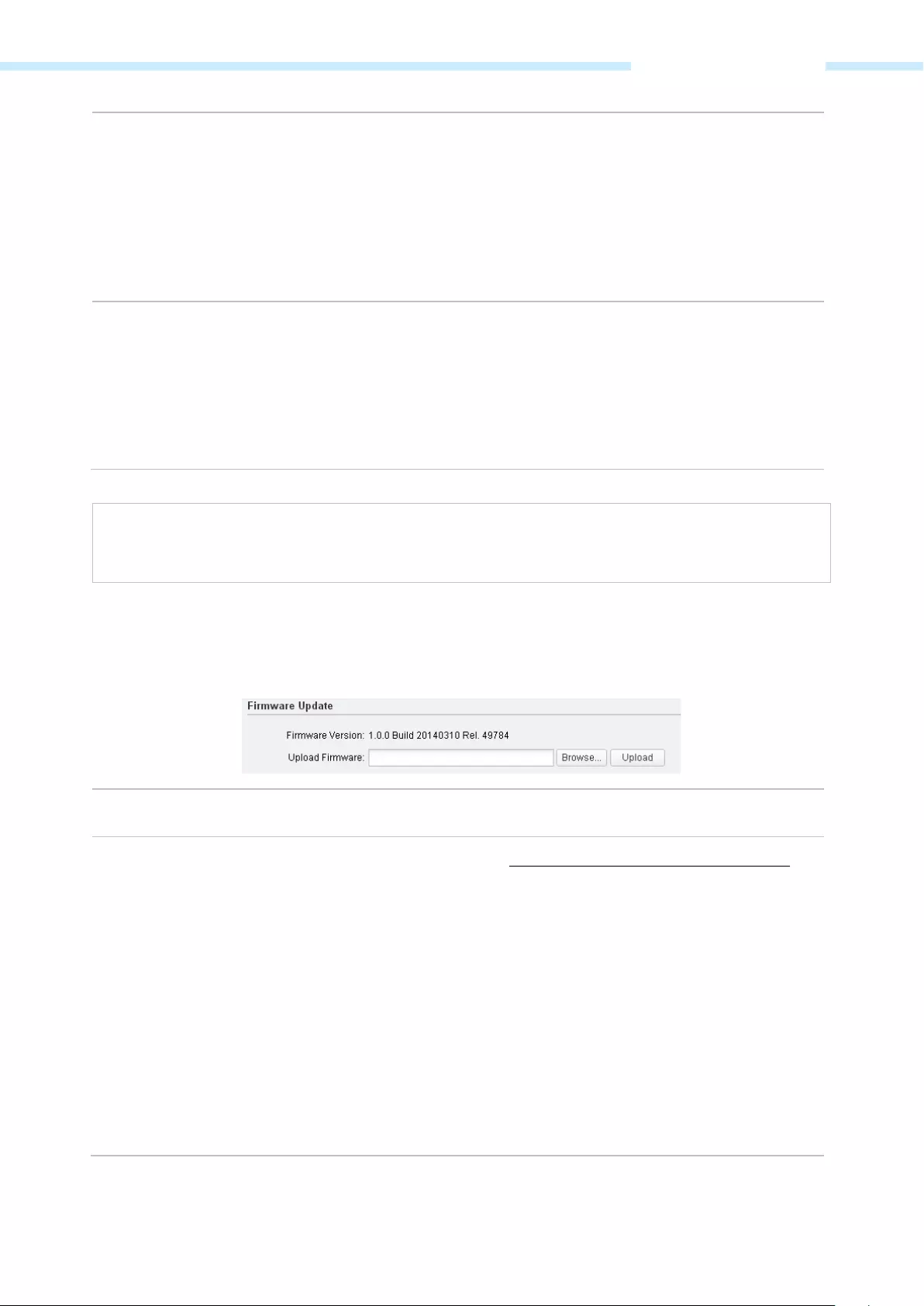
Chapter 8 System Tab
Recurring Mode Specify the DST configuration in recurring mode. This configuration is recurring
in use.
Time Offset: Specify the time offset in minutes when Daylight Saving Time
comes.
Start/End Time: Select the start time and end time of Daylight Saving Time.
The start time is the standard time, and the end time is the Daylight Saving
Time.
Date Mode Specify the DST configuration in Date mode. This configuration is one—off in use.
Time Offset: Specify the time adding in minutes when Daylight Saving Time
comes.
Start/End Time: Select the start time and end time of Daylight Saving Time.
The start time is the standard time, and the end time is the Daylight Saving
Time.
NOTE:
When the DST is enabled, the default daylight saving time is European in predefined mode.
Firmware Update
Firmware update can improve the function of the device.
Firmware version Displays the current firmware version.
Upload Firmware Please visit TP—LINK website www.tp-link.com/en/support/download/ to
download the latest firmware. The system configuration can be preserved while
the device is updated with a new firmware version. However, we recommend
that you back up current system configuration before updating the firmware.
Firmware update takes three steps:
1. Click Browse to locate the new firmware file.
2. Select the file and click Open. The new firmware to be uploaded is displayed
in the field.
3. Click Upload and there will be a pop—up page which gives you three options
of keeping your configurations or restoring to factory default after the
upgrade or just cancel the upgrade.
— 81 —

Chapter 8 System Tab
NOTE:
1. Please select the proper software version that matches your hardware to upgrade.
2. To avoid damage, please do not power off the device while upgrading.
3. After upgrading, the device will reboot automatically.
Configuration
The controls in this section manage the device configuration routines and the option to reset the device to
factory default settings.
The device configuration is stored in the plain text file. You can back up, restore, or update the system
configuration file.
Backup Configuration Click Backup to back up the current system configuration file.
Upload Configuration Click Browse to locate the new configuration file. Select the file and click Open,
then the new configuration to be uploaded is displayed in the field. Click
Upload to upload the new configuration to the device. We recommend that
you back up your current system configuration before uploading the new
configuration.
Reset to Factory Default Resets the device to the default settings. This option will reboot the device,
and all factory default settings will be restored. It’
s recommended that you
back up your current system configuration before resetting the device to its
defaults.
Reboot Device Initiates a full reboot cycle of the device. The system configuration stays the
same after the reboot cycle completes. Any changes that have not been
applied will be lost.
NOTE:
1. After backing up, the device will reboot automatically.
2. To avoid damage, please don‘t turn off the device while uploading.
3. You are suggested to back up the configuration before upgrading.
— 82 —

Chapter 9 Tools
Chapter 9 Tools List
This device provides some useful tools including Ping, Traceroute, Speed Test, Survey and Spectrum
Analysis.
Ping
Ping test function is used to test the connectivity and reachability between the device and the target host
so as to locate the network malfunctions.
Destination IP/Domain Enter the IP address of the destination node for Ping test. Click Start, the
device will send Ping packets to test the network connectivity and reachability
of the host and the results will be displayed in the list below.
Packet Count Enter the number of packets to be sent during the testing. It can be 1 to 50 and
the default is 4.
Ping Timeout Enter a time value to wait for a response. It can be 100—2000 milliseconds. The
default value is 800 milliseconds.
— 83 —

Chapter 9 Tools
Packet Size Enter the number of data bytes to be sent. It can be 4—472 bytes and the
default is 64.
Traceroute
Tracertroute function is used to tracks the route packets taken from source on their way to a given target
host. When malfunctions occur in the network, you can troubleshooting with traceroute utility.
Destination IP/Domain Enter the destination IP address or the Domain name. Click Start, the device
will send Tracert packets to the target host and the results will be displayed in
the list below.
Traceroute Max TTL Set the maximum number of hops (max TTL to be reached) in the path to reach
the target (destination). The default is 5.
Speed Test
Speed Test tool is used for testing the throughput between two Pharos products in the same network. The
test requires one of the two devices to be set as a server and the other as a client. The client launches the
test request to the server and the server respond to it. The test result will display on the page of the client.
— 84 —
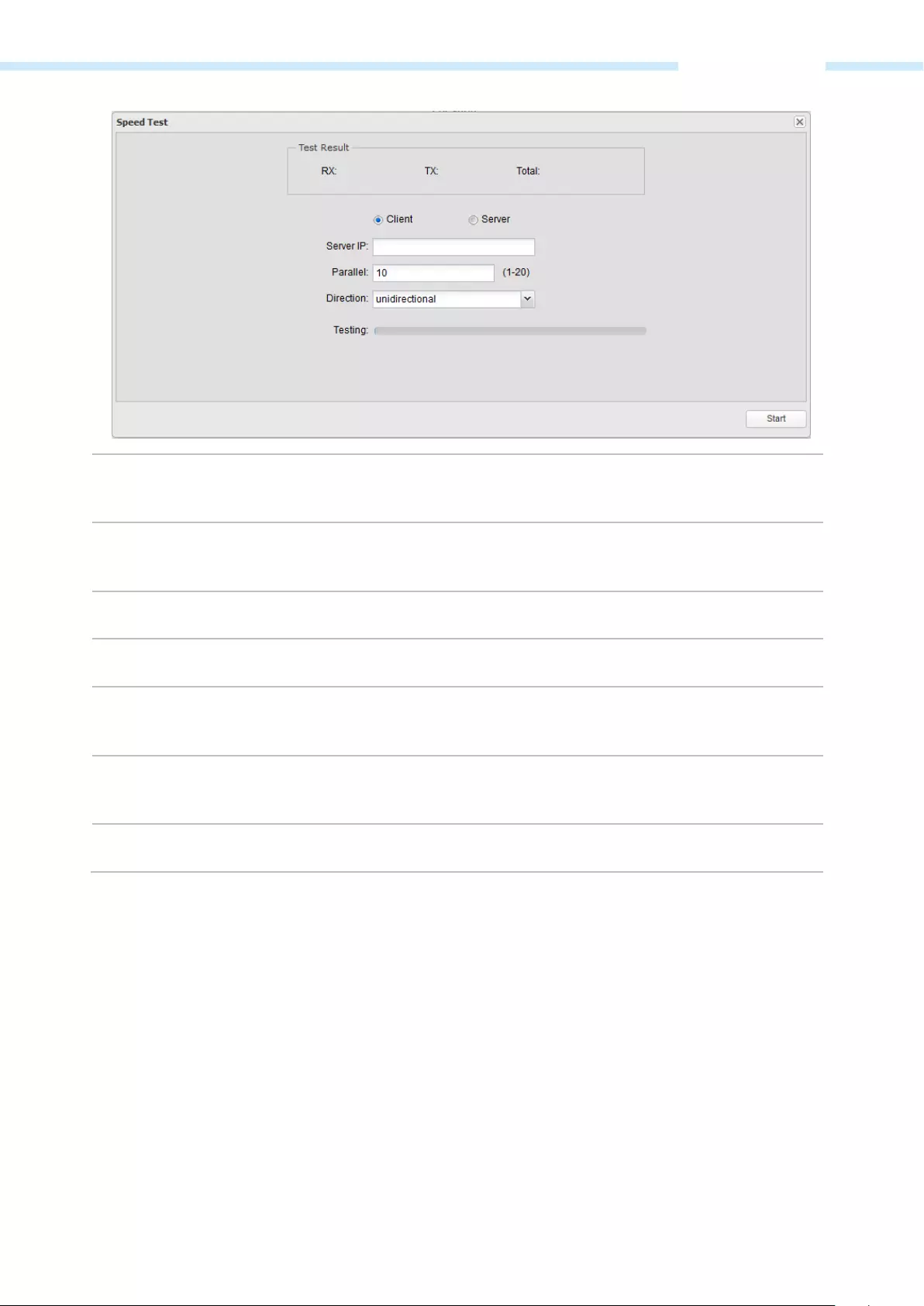
Chapter 9 Tools
Test Result Displays the data streams that the device is transmitting (TX) and receiving
(RX).
Client The side to initiatively launch the test request. T
he client side can configure
parameters including server’s IP, parallel and direction.
Server The side to passively accept the test request.
Server IP The IP address of the server.
Parallel The number of simultaneous connections to make to the server. It ranges from
1 to 20 and the default value is 10.
Direction Se
lect the direction of the speed test including unidirectional and
bidirectional.
Testing Testing progress bar. Click Start to displays the testing progress.
— 85 —

Chapter 9 Tools
Survey
BSSID Displays the BSSID of other APs surveyed by this device.
SSID Displays the SSID of other APs surveyed by this device.
MAXtream Displays the MAXtream capability of other APs surveyed by this device.
Device Name Displays the names of other APs surveyed by this device.
SNR (dB) Displays the Signal Noise Ratio (Unit: dB) of other APs surveyed by this device.
Signal/Noise (dBm) D
isplays the signal and noise value (Unit: dBm) of other APs surveyed by this
device.
Channel Displays the channels of other APs surveyed by this device.
Security Displays the security mode of other APs surveyed by this device.
AP Count Displays the number of other APs surveyed by this device.
Refresh Refresh this page by clicking Refresh.
— 86 —
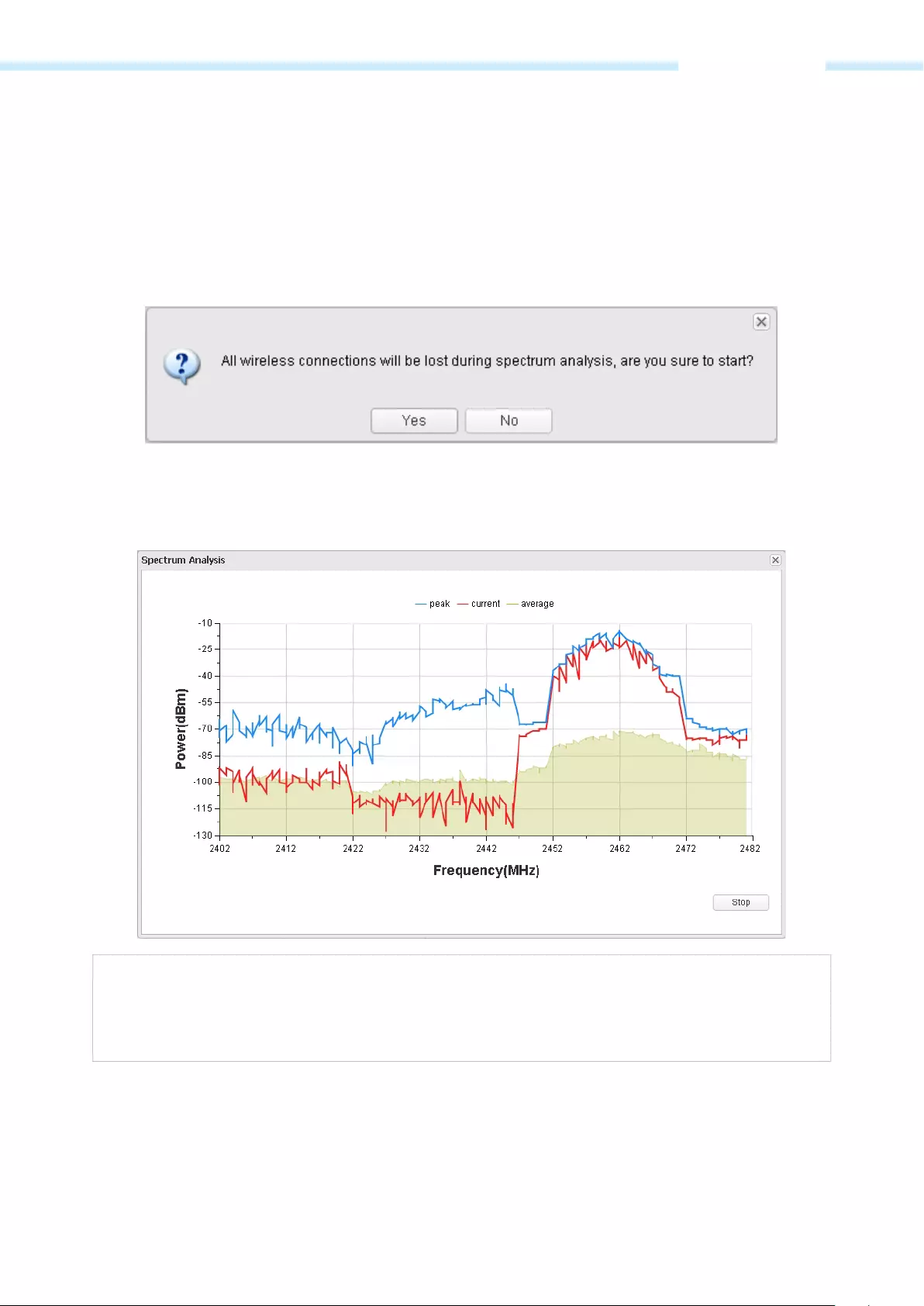
Chapter 9 Tools
Spectrum Analysis
Spectrum Analysis can help you to choose the proper channel/frequency. Through the spectrum analysis
you can learn the distribution of the radio noise and intelligently select the channel/frequency in low noise.
1. Click Spectrum Analysis in the tools’ drop—down list, the following window will pop up to remind
you that all wireless connections will be lost during spectrum analysis. Click Yes and you will then get
into Spectrum Analysis page.
2. Click Start, the PharOS will begin to analyze the power of frequency. Observe the curves for a period
of time, and then click stop. Note that the relatively low and continuous part of the average curve
indicates less radio noise. Here we take the figure below as an example.
NOTE:
CPE510/CPE520/BS510 has a select box of Frequency Range at the top—left corner. Select the required range
and then click Start.
3. When choosing channel/frequency, we should try to avoid the spectrum with large radio noise. In this
example, the recommended channel/frequency is 1/2412MHz and 6/2437MHz.
— 87 —

Appendix A Pharos MAXtream TDMA
Appendix A: Pharos MAXtream TDMA
With the fast expansion of network scale, wireless competition and collisions among CPEs and base
stations will be so enormous that the real throughout of the network will drop, resulting in a serious
impact on end—user experience. To mitigate these effects, TP—LINK’s Pharos series develops MAXtream
TDMA Technology.
Pharos MAXtream is a proprietary protocol developed on the basis of TDMA (Time Division Multiple Access)
by TP—LINK. MAXtream cuts each wireless data frame transmission into certain number of time slots
according to the client connections priority, greatly boosting efficiency of the wireless channel.
The MAXtream technology has the following advantages which make it ideal for point to multi—point links:
Eliminates hidden node collisions and improves channel efficiency
Lower latency, higher throughput, larger network capacity and more stability
To enable the MAXtream function among the AP and stations, you only need to select MAXtream option
on the Wireless tab of the Pharos web management page of the AP, as shown in the following figure.
Stations will automatically adjust their connections according to AP’s MAXtream capability.
NOTE:
1.
Ensure you select a correct Region to comply with local laws. Incorrect settings may violate local
regulations.
2. Pharos MAXtream is a non-standard Wi—Fi protocol that is only compatible with TP—LINK’s Pharos series
products. Please notice that you will not be able to connect other Wi—Fi devices to an AP with MAXtream
enabled.
— 88 —

Appendix B Glossary
Appendix B: Glossary
Glossary Description
A
ALG (Application Layer
Gateway)
Application Level Gateway (ALG) is application specific translation
agent that allows an application on a host in one address realm to
connect to its counterpart running on a host in different realm
transparently.
ARP (Address Resolution
Protocol) Internet protocol used to map an IP address to a MAC address.
C CPE (Customer Premise
Equipment)
A terminal located at a subscriber’s premises and connected with a
carrier‘s telecommunication channel at the demarcation point. The
point is established in a building or complex to separate customer
equipment from the equipment located in either the distribution
infrastructure or central office of the Communications Service Provider.
D
DDNS (Dynamic Domain
Name Server)
The capability of assigning a fixed host and domain name to a dynamic
Internet IP address.
DFS (Dynamic Frequency
Selection)
A method applied in wireless networks, which is used for radar
avoidance and is supported by the novel IEEE 802.11h wireless local
area network standard.
DHCP (Dynamic Host
Configuration Protocol)
A protocol that automatically configures the TCP/IP parameters for all
the PCs that are connected to a DHCP server.
DMZ (Demilitarized Zone)
A Demilitarized Zone allows one local host to be exposed to the
Internet for a special—purpose service such as Internet gaming or
videoconferencing.
DNS (Domain Name Server)
An Internet Server that translates the names of websites into IP
addresses.
DoS (Denial of Service) A hacker attack designed to prevent your computer or network from
operating or communicating.
F FTP (File Transfer Protocol)
Application protocol, part of the TCP/IP protocol stack, used for
transferring files between network nodes.
H HTTP (Hypertext Transfer
Protocol)
The protocol used by Web browsers and Web servers to transfer files,
such as text and graphic files.
— 89 —

Appendix B Glossary
Glossary Description
I
ICMP (Internet Control
Messages Protocol)
Network layer Internet protocol that reports errors and provides other
information relevant to IP packet processing.
Internet
Largest global Internetwork, connecting tens of thousands of networks
worldwide and having a “culture” that focuses on research and
standardization based on real—life use.
IP (Internet Protocol)
Network layer protocol in the TCP/IP stack offering a connectionless
Internetwork service. IP provides features for addressing, type—of—
service specification, fragmentation and reassembly, and security.
ISP (Internet Service
Provider)
Company that provides Internet access to other companies and
individuals.
IPsec (IP Security) A framework of open standards that provides data confidentiality, data
integrity, and data authentication between participating peers.
L LAN (Local Area Network)
High—speed, low—
error data network covering a relatively small
geographic area (up to a few thousand meters). LANs connect
workstat
ions, peripherals, terminals, and other devices in a single
building or other geographically limited area.
M
MAC address (Media Access
Control address)
Standardized data link layer address that is required for every port or
device that connects to a LAN. Other devices in the network use these
addresses to locate specific ports in the network and to create and
update routing tables and data structures. MAC addresses are 6 bytes
long and are controlled by the IEEE.
MTU (Maximum
Transmission Unit) The size in bytes of the largest packet that can be transmitted.
N
NAT (Network Address
Translator)
Mechanism for reducing the need for globally unique IP addresses.
NAT allows an organization with addresses that are not globally
unique to connect to the Internet by translating those addresses into
globally routable address space.
NTP Server NTP Server is used for synchronizing the time across computer
networks.
P PPPoE (Point—to—Point
Protocol over Ethernet)
PPPoE is a network protocol for encapsulating Point-to-Point Protocol
(PPP) frames inside Ethernet frames.
— 90 —

Appendix B Glossary
Glossary Description
S
SMTP (Simple Mail Transfer
Protocol) SMTP is an Internet standard for electronic mail (e—mail) transmission
SSH (Secure Shell Protocol) SSH is a network protocol that allows data to be exchanged using a
secure channel between two networked devices.
SSID
A Service Set Identification is a thirty—two character (maximum)
alphanumeric key identifying a wireless local area network. For the
wireless devices in a network to communicate with each other, all
devices must be configured with the same SSID. This is typically the
configuration parameter for a wireless PC card. It corresponds to the
ESSID in the wireless Access Point and to the wireless network name.
SNMP (Simple Network
Management Protocol)
SNMP provides a management frame to monitor and maintain the
network devices. With SNMP function enabled, network administrators
can easily monitor the network performance, detect the malfunctions
and configure the network devices.
T
TCP (Transfer Control
Protocol)
Connection—oriented transport layer protocol that provides reliable
full—duplex data transmission.
TCP/IP (Transmission
Control Protocol/ Internet
Protocol)
Common name for the suite of protocols to support the construction
of worldwide Internet works. TCP and IP are the two best—known
protocols in the suite.
TDMA (Time Division
Multiple Access)
TDMA (Time Division Multiple Access) cuts each wireless data frame
into certain number of time slots according to the client connections
priority, greatly boosting efficiency of the wireless channel.
U
UDP (User Datagram
Protocol)
UDP is a simple protocol that exchanges datagram without
acknowledgments or guaranteed delivery, requiring that error
processing and retransmission be handled by other protocols.
UPnP (Universal Plug and
Play)
UPnP is a set of networking protocols for primarily residential networks
without enterprise class devices that permits networked devices.
V
VLAN (Virtual Local Area
Network)
Group of devices on one or more LANs that are configured (using
management software) so that they can communicate as if they were
attached to the same wire, when in fact they are located on a number
of different LAN segments. Because VLANs are based on logical instead
of physical connections, they are extremely flexible.
VPN (Virtual Private
Network)
Enables IP traffic to travel securely over a public TCP/IP network by
encrypting all traffic from one network to another.
— 91 —

Appendix B Glossary
Glossary Description
W
WAN (Wide Area Network)
Data communications network that serves users across a broad
geographic area and often uses transmission devices provided by
common carriers.
WEP (Wired Equivalent
Privacy)
A data privacy mechanism based on a 64—bit or 128—bit or 152—bit
shared key algorithm, as described in the IEEE 802.11 standard.
Wi—Fi
A trademark of the Wi—Fi Alliance, founded in 1999 as Wireless Internet
Compatibility Alliance (WICA), comprising more than 300 companies,
whose products are certified by the Wi—Fi Alliance, based on the IEEE
802.11 standards (also called Wireless LAN (WLAN) and Wi—Fi). This
certification warrants interoperability between different wireless
devices.
WISP (Wireless Internet
Service Provider)
WISPs are Internet service providers with networks built around
wireless networking. The technology used ranges from commonplace
Wi—Fi mesh networking or proprietary equipment designed to operate
over open 900MHz, 2.4GHz, 4.9, 5.2, 5.4, and 5.8GHz bands or licensed
frequencies in the UHF or MMDS bands.
WLAN (Wireless Local Area
Network)
A group of computers and associated devices communicate with each
other wirelessly, which network serving users are limited in a local area.
— 92 —

For TP—LINK Pharos Series Products
REV1.0.0
1910011048
User Guide

CONTENTS
Chapter 1 Overview ………………………………………………………………………………………………………… 1
Introduction ……………………………………………………….……………………………………………….………………………………………………... 1
System Requirements …………………………..………………………………………………………………………………………………….…………. 1
Getting Started …………………………..…………………………………………………………………………………………………….………………….. 1
Navigation ……………………………………………………….……………………………………………………..…………………………………………….. 3
Chapter 2 Operation Modes …………………………………………………………………………………………….. 4
Access Point …………………………..……………………………………………………….……………………………………………………….……………. 4
Client……………………………………………….……………………………………………….……………………………………………….……………………. 6
Repeater (Range Extender) ………………………………………………………………………………………………………………………..………. 7
Bridge ……………………………………………………….……………………………………………….……………………………………………….………….. 8
AP Router ……………………………………………………….………………………………………………………………………………………………….….. 8
AP Client Router (WISP Client) …………………………..……………………………………………………….……………………………………… 9
Chapter 3 Quick Setup Guide ………………………………………………………………………………………….10
Access Point …………………………………………………………………………………………………………………………………………….………….. 10
Client……………………………………………….……………………………………………….……………………………………………….………………….. 12
Repeater (Range Extender) ………………………………………………………………………………………………………………………..…….. 14
Bridge ……………………………………………………….……………………………………………….……………………………………………….………… 17
AP Router ……………………………………………………….………………………………………………………………………………………………….… 20
AP Client Router (WISP Client) …………………………..……………………………………………………….……………………………………. 22
Chapter 4 Status Tab ………………………………………………………………………………………………………27
Status Information …………………………………………………………………………………………………………………………………….……….. 28
Monitor ………………………………………………………………………………………………………………..………………………………………………. 32
Chapter 5 Network Tab …………………………………………………………………………………………………..37
WAN ……………………………..…………………………………………………….……………………………………………………….……………………….. 38
LAN …………………………..……………………………………………………….…………………………………………………..……………………………… 44
Forwarding …………………………………………………………………………………………………………………………………………….……………. 46
Security …………………………….……………………………………………………..……………………………………………………….………………….. 50
Access Control ……………………………………………………………………………..……………………………………………….…………………….. 52
Static Routing …………………………………………………………………………………………………………………………………………….……….. 53
Bandwidth Control ………………………………………………………………….……………………………………………….………………………... 54
I

IP&MAC Binding ………………………………………………………………..……………………………………………….………………………………. 55
Chapter 6 Wireless Tab ……………………………………………………………………………………………………57
Wireless Basic Settings ………………………………………………………………………..……………………………………………….……………. 58
Wireless Client Settings …………………………..……………………………………………….……………………………………………….………. 60
Wireless AP Settings ……………………………………………………………………..……………………………………………….…………………… 61
Multi—SSID ……………………………………………………….……………………………………………………….………………………………………….. 64
Wireless MAC Filtering ……………………………………………………….……………………………………………………………………………… 65
Wireless Advanced Settings ……………………………..…………………………………………………….………………………………………… 66
Chapter 7 Management Tab ……………………………………………………………………………………………68
System Log ……………………………………………………….……………………………………………………….………………………………………… 69
Miscellaneous ……………………………………………………………………………………………………………………………………………………… 70
Ping Watch Dog ……………………………………………………………………….…………………………………………………………………………. 71
Dynamic DNS …………………………………………………………………………………………………………………………………………….……….. 72
Web Server ……………………………………………………………..…………………………………………………………………………………………… 73
SNMP Agent ……………………………………………………….……………………………………………………….………………………………………. 74
SSH Server ……………..……………………………………………….………………………………………………..…………………………………………. 75
RSSI LED Thresholds ………………………………………………………………………………………..…………………………………………………. 76
Chapter 8 System Tab ……………………………………………………………………………………………………..77
Device …………………………..……………………………………………………….……………………………………………………….…………………….. 78
Location ……………………………………………………….……………………………………………………….……………………………………………… 78
User Account ……………………………………………………………..………………………………………………………………………………………… 78
Time Setting ………………………………………………………………………………………………………………..………………………………………. 79
Firmware Update ………………………………………………………………………………………….……………………………………………………. 81
Configuration ……………………………………………………….……………………………………………………….……………………………………. 82
Chapter 9 Tools List ………………………………………………………………………………………………………..83
Ping ………………………………………………………..…………………………………………………………………………………………………………….. 83
Traceroute …………………………………………………………………………………………..………………………………………………..……………… 84
Speed Test ………………………………………………………………….……………………………………………….……………………………………….. 84
Survey …………………………..…………………………………………………………………………………….………………………………………………… 86
Spectrum Analysis …………………………………………………………………………………………..……………………………………………….... 87
Appendix A: Pharos MAXtream TDMA …………………………………………………………………………………88
Appendix B: Glossary …………………………………………………………………………………………………………89
II

Chapter 1 Overview
Chapter 1 Overview
Introduction
is TP—LINK’s next generation outdoor product series dedicated to long—distance outdoor
wireless networking solutions.
is a powerful Web—based operating system, which is integrated into all Pharos series
products.
New features of Pharos series products are listed as follows:
Provides User—friendly UI design.
TP—LINK Pharos MAXtream (Time—Division—Multiple—Access) technology improves product
performance in throughput, capacity and latency, which are ideal for Point—to—multipoint applications.
Supports multiple operation modes: Access Point, Client, Repeater (Range Extender), Bridge, AP
Router and AP Client Router (WISP Client).
Provides system—level optimization for long—distance wireless transmission.
Supports adjustable transmit power by 1dBm from 0 to 27dBm/500mW.
Supports selectable bandwidth of 5/10/20/40MHz.
Supports easy antenna alignment with Wireless Signal Indicators on Web interface.
Provides Throughput Monitor, Spectrum Analyzer, Speed Test and Ping tools.
Supports discovery and management via Pharos Control application.
System Requirements
Operating system:
Microsoft Windows XP, Windows Vista, Windows 7, Windows 8, Linux, or Mac OS X
Web Browser:
Google Chrome, Safari, Firefox, and Apple Safari. IE browsers are not recommended.
Getting Started
To access the PharOS Configuration Interface, perform the following steps:
1. Configure the Ethernet adapter on your computer with a static IP address on the 192.168.0.x subnet
(for example, IP address: 192.168.0.100 and subnet mask: 255.255.255.0).
2. Launch your Web browser. Enter the default IP address of your device in the address field. Press Enter
(PC) or Return (Mac).
For Example, enter 192.168.0.254 to access the PharOS.
— 1 —

Chapter 1 Overview
3. Upon initial login, please enter admin in the Username and Password fields, and select the
appropriate region from the Region drop—down lists. Check the box next to I agree to these terms of
use, and click Login.
NOTE:
Ensure you select a correct Region to comply with local laws. Incorrect settings may
regulations.
4. We recommend you change the device’s user name and password from its default settings for
network security. Enter and confirm new user name and password, then click Finish.
5. For subsequent logins, you only need to enter the user name and password that you have set to log
in.
— 2 —

Chapter 1 Overview
Navigation
The PharOS Web Interface contains six main tabs, each of which provides a Web—based management page
to configure the specific parameters of the Pharos series products.
Quick Setup
On Quick Setup Guide
, you can quickly configure your device through the step—by—step Quick Setup
Wizard.
Status
The Status Tab
displays a summary of the link status information, current values of the basic configuration
settings (depending on the operating mode), network settings and information, and traffic statistics.
Network
The Network Tab
configures the function of WAN, LAN, forwarding, security, access control, static routing,
bandwidth control and IP&MAC binding.
Wireless
On The Wireless Tab
, you can configure the related wireless parameters in different modes.
Management
The Management Tab
configures system management services: System Log, Miscellaneous, Ping Watch
Dog, and Dynamic Domain Name System (DDNS). Web server, Simple Network Management Protocol
(SNMP), SSH server, RSSI LED Thresholds are also available.
System
The System Tab
controls system maintenance routines, device customization, location management, user
account management, firmware update, Time setting and configuration backup.
Tools
The Tools list
provides some useful tools including Ping, Traceroute, Speed Test, Survey and Spectrum
Analysis.
— 3 —

Chapter 2 Operation Modes
Chapter 2 Operation Modes
The Pharos series products support six modes to satisfy user’s diversified network requirements including
Access Point mode, Client mode, Repeater (Range Extender) mode, Bridge mode, AP Router mode and AP
Client Router (WISP Client) mode. This chapter introduces typical usage scenarios of each mode. You can
choose the desired scenario according to your needs, and refer to the Installation Guide for hardware
connection instruction and Chapter 3 Quick Setup Guide
for software configuration.
Access Point
In AP mode, the device acts as a central hub and provides wireless access point for wireless clients, thus
the AP mode is very applicable to the following three scenarios. Meanwhile, Multi—SSID function can be
enabled in this mode, providing four wireless networks with different SSIDs and passwords.
Scenario 1
Network requirements: Establish wireless network coverage in the campus, community, industrial park or
public places to provide wireless access points for wireless users.
The device in the network: With the access to campus network or local area network, the device in AP
mode provides the wireless access point based on the existing wired local area network for wireless clients,
such as smart phones, laptops and tablets.
Advantages: Increase wireless access points and enrich the access ways of local area network.
Network diagram:
Scenario 2
Network requirements: Establish the network coverage in the remote areas without long—distance cabling.
The device in the network: In the adjacent town covered by wired network, ISP (Internet Service Provider)
can put up a device in AP mode with the access to ISP network by connecting to ISP’s router to transform
wired signal into wireless one. The remote users can put up a device in AP Client Router mode to access
the Internet the AP device provides wirelessly.
— 4 —

Chapter 2 Operation Modes
Advantages: Transmit data wirelessly across a long distance and reduce the cabling cost.
Network diagram:
Scenario 3
Network requirements: Establish a point—to—point link for video monitor or combine two separate office
networks as one.
The device in the network: For video monitor, the device in AP mode connects to the monitoring
computer and the device in Client mode connects to IP Camera. For combining two separate office
networks as one, two devices in AP and Client mode respectively connect to the switches in two office
networks so as to connect two office networks.
Advantages: Establish a point—to—point WLAN across a long distance to achieve the connectivity between
two networks and avoid the cabling trouble.
Network diagram:
Video monitor
— 5 —

Chapter 2 Operation Modes
Internet sharing
Client
Network requirements: The most common usage scenario of Client is point—to—point networking with AP
for video monitor or combining two separate office networks. Please refer to Scenario 3 of Access Point
for detailed information.
The device in the network: In this mode, the device actually serves as a wireless adapter to receive the
wireless signal from root AP or Station. In the case, wired devices can access the network provided by root
AP or Station through connecting to Client.
Network diagram:
Video monitor
Internet sharing
— 6 —

Chapter 2 Operation Modes
Repeater (Range Extender)
The device in Repeater mode can extend wireless coverage of an existing wireless network to cover “dead”
spots, especially to eliminate signal—blind corners in a larger space. The SSID and encryption type of the
device should be the same as those of root AP.
Network requirements: Eliminate the wireless signal-blind areas and repeat wireless signal.
The device in the network: In a large campus or industrial park, the device in Repeater mode can reinforce
the wireless signal strength of the existing network and extend the network coverage to eliminate the
signal-blind areas. Remote data can be transmitted across a long distance beyond the transmission range.
Meanwhile, the wireless users can experience a wireless network roaming when moving around.
Network diagram:
Eliminate the wireless signal—blind areas
Repeat wireless signal
— 7 —

Chapter 2 Operation Modes
Bridge
Network requirements: Reinforce the wireless signal strength of the root AP device to eliminate the
wireless signal—blind areas. Meanwhile, the wireless users can use the SSID and encryption type different
from those of the root AP device to access the network.
The device in the network: Similar to the Repeater mode, the Bridge mode is used to reinforce the exiting
wireless signal. However, the very difference is that the Bridge has its own SSID and encryption type
different from those of root AP.
Network diagram:
Eliminate the wireless signal—blind areas
Bridge for wireless signal
AP Router
Network requirements: Establish the wireless network coverage in the campus, community, industrial park
or other public places and so on.
The device in the network: Similar to the home wireless router, the device in AP Router mode connects to
root ADSL/Cable Modem. The difference lies in that the coverage area of this device is wider. Smart
— 8 —

Chapter 2 Operation Modes
phones, laptops, and other wireless clients can share wide area network via the access to wireless network
this device provides.
Network diagram:
AP Client Router (WISP Client)
In AP Client Router mode, after accessing the wireless network provided by WISP, the device provides
wireless network service for downstream wireless clients. Meanwhile, the device allows wired devices,
such as desktop computer, to access it via LAN1 port or PoE adapter’s LAN port. In this way, all members of
a home user can share the Internet using one account applied from WISP.
— 9 —

Chapter 3 Quick Setup Guide
Chapter 3 Quick Setup Guide
Quick Setup wizard allows you to quickly configure your device step by step. Choose the suitable
operation mode according to your network environment and follow the step—by—step instructions.
Access Point
If Access Point is selected, click Next and take the following steps:
1. The LAN Settings page will appear as shown below. The default IP Address is 192.168.0.254 and the
default Subnet Mask is 255.255.255.0. You can change the IP Address and Subnet Mask on this page
when there is an IP conflict with other devices. We recommend you keep it by default. Click Next.
— 10 —

Chapter 3 Quick Setup Guide
2. The Wireless AP Settings page will appear as shown below. Create an easy—to—remember name for
your wireless network. Select WPA—PSK/WPA2—PSK in the Security box and enter the PSK Password
below to prevent unauthorized access to your AP. Enter the distance between this device and the
furthest client in Distance Setting. Then click Next.
3. The Finish page will appear and display what you’ve configured previously. If you want to modify any
parameter, click Back to reconfigure it. If all are confirmed, click Finish to complete the configuration.
— 11 —

Chapter 3 Quick Setup Guide
Client
If Client is selected, click Next and take the following steps:
1. The LAN Settings page will appear as shown below. The default IP Address is 192.168.0.254 and the
default Subnet Mask is 255.255.255.0. You can change the IP Address and Subnet Mask on this page
when there is an IP conflict with other devices. We recommend you keep it by default. Click Next.
2. The Wireless Client Settings page will appear as shown below. Click Survey to search for wireless
networks.
— 12 —

Chapter 3 Quick Setup Guide
3. The AP list will appear as shown below. Select the desired wireless network and click Connect. It’s
possible that two or more networks use the same SSID in the AP list. Lock to AP can make the device
connect to the specified AP you had connected before the next time.
4. If the root AP needs password to be connected, you should select the same Mode, Channel Width
and Security type and enter the same PSK Password as entered on the root AP/router. Enter the
distance between this device and the root AP in Distance setting. Then click Next.
— 13 —

Chapter 3 Quick Setup Guide
5. The Finish page will appear and display what you’ve configured previously. If you want to modify any
parameter, click Back to reconfigure it. If all are confirmed, click Finish to complete the configuration.
Repeater (Range Extender)
If Repeater (Range Extender) is selected, click Next and take the following steps:
1. The LAN Settings page will appear as shown below. The default IP Address is 192.168.0.254 and the
default Subnet Mask is 255.255.255.0. You can change the IP Address and Subnet Mask on this page
when there is an IP conflict with other devices. We recommend you keep it by default. Click Next.
— 14 —

Chapter 3 Quick Setup Guide
2. The Wireless Client Settings page will appear as shown below. Click Survey to search for wireless
networks.
3. The AP list will appear as shown below. Select the desired wireless network and click Connect. It’s
possible that two or more networks use the same SSID in the AP list. Lock to AP can make the device
connect to the specified AP you had connected before the next time.
— 15 —

Chapter 3 Quick Setup Guide
4. If the root AP needs password to be connected, you should select the same Mode, Channel Width
and Security type and enter the same PSK Password as entered on the root AP/router. Enter the
distance between this device and the root AP/router in Distance setting. Then click Next.
5. The Finish page will appear and display what you’ve configured previously. If you want to modify any
parameter, click Back to reconfigure it. If all are confirmed, click Finish to complete the configuration.
— 16 —

Chapter 3 Quick Setup Guide
Bridge
If Bridge is selected, click Next and take the following steps:
1. The LAN Settings page will appear as shown below. The default IP Address is 192.168.0.254 and the
default Subnet Mask is 255.255.255.0. You can change the IP Address and Subnet Mask on this page
when there is an IP conflict with other devices. We recommend you keep it by default. Click Next.
2. The Wireless Client Settings page will appear as shown below. Click Survey to search for wireless
networks.
— 17 —
